Short Summary
In June 2024, Zscaler ThreatLabz reported on BlindEagle, an APT actor targeting the Colombian insurance sector through phishing emails. The actor utilizes the BlotchyQuasar RAT to gain access and steal sensitive data, primarily from banking services. The attack chain involves sophisticated obfuscation techniques and the use of compromised Google Drive folders to distribute malware.
Key Points
- BlindEagle began targeting the Colombian insurance sector in June 2024.
- Phishing emails impersonated the Colombian tax authority to lure victims.
- BlotchyQuasar RAT was used, featuring multiple layers of obfuscation.
- Malware was distributed via password-protected ZIP files hosted on compromised Google Drive accounts.
- BlindEagle’s infrastructure includes the use of VPNs and dynamic DNS services.
- The malware is capable of keylogging and monitoring interactions with banking services.
- Indicators of compromise (IOCs) have been identified, including specific C2 domains.
MITRE ATT&CK TTPs – created by AI
- T1583.001 – Acquire Infrastructure: Domains
- BlindEagle uses DDNS services to create third level domains for C2.
- T1586.002 – Compromise Accounts: Email Accounts
- BlindEagle controlled a Google Drive folder owned by a Colombian government organization.
- T1587.001 – Develop Capabilities: Malware
- BlindEagle operates BlotchyQuasar, a customized variant of QuasarRAT.
- T1608.001 – Stage Capabilities: Upload Malware
- BlindEagle staged a BlotchyQuasar sample on a compromised Google Drive folder.
- T1566.002 – Phishing: Spearphishing Link
- BlindEagle attempted to gain initial access via phishing emails containing malware links.
- T1204.002 – User Execution: Malicious File
- BlindEagle renamed the BlotchyQuasar sample to match the phishing email lure.
- T1204.001 – User Execution: Malicious Link
- The attack chain starts with the victim clicking a link in the phishing email.
- T1547.001 – Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
- BlotchyQuasar achieves persistence by setting a RunKey.
- T1053.005 – Scheduled Task/Job: Scheduled Task
- BlotchyQuasar creates a scheduled task that launches itself every 3 minutes.
- T1562.001 – Impair Defenses: Disable or Modify Tools
- BlotchyQuasar attempts to disable several Defender features if executed with elevated privileges.
- T1564.001 – Hide Artifacts: Hidden Files and Directories
- BlotchyQuasar creates hidden directories to store keylogger files.
- T1027.003 – Obfuscated Files or Information: Steganography
- BlotchyQuasar loader uses a Bitmap image as a .NET-managed resource for protection.
- T1027.009 – Obfuscated Files or Information: Embedded Payloads
- BlotchyQuasar malware is buried under three layers of encrypted code.
- T1027.013 – Obfuscated Files or Information: Encrypted/Encoded File
- BlotchyQuasar stores keylogger logs after encrypting them with AES.
- T1553.005 – Subvert Trust Controls: Mark-of-the-Web Bypass
- BlotchyQuasar deletes the Zone.Identifier ADS to bypass the MOTW.
- T1027.002 – Obfuscated Files or Information: Software Packing
- BlotchyQuasar loader is obfuscated with .NET obfuscators.
- T1140 – Deobfuscate/Decode Files or Information
- The BlotchyQuasar C2 domain is decrypted with AES.
- T1056.001 – Input Capture: Keylogging
- BlotchyQuasar logs keystrokes.
- T1539 – Steal Web Session Cookie
- BlotchyQuasar can steal cookies and passwords from browsers and FTP clients.
- T1056.002 – Video Capture
- BlotchyQuasar can control the webcams of infected systems.
- T1095 – Non-Application Layer Protocol
- BlotchyQuasar establishes a socket-based C2 channel.
- T1041 – Exfiltration Over C2 Channel
- BlotchyQuasar exfiltrates stolen information over the C2 channel.
- T1490 – Inhibit System Recovery
- BlotchyQuasar deletes shadow copies with the vssadmin utility if executed with high privileges.
Introduction
In June 2024, Zscaler ThreatLabz detected fresh activity from BlindEagle, an advanced persistent threat (APT) actor also identified as AguilaCiega, APT-C-36, and APT-Q-98. BlindEagle predominantly focuses on organizations and individuals from the government and finance sector in South America, particularly in Colombia and Ecuador. BlindEagle’s primary method to gain initial access to the targets’ systems is through phishing emails. Once accessed, the threat actor usually employs commodity .NET Remote Access Trojans (RATs), like AsyncRAT, RemcosRAT, and more, to steal credentials from various banking service providers. BlindEagle is also known for operating repurposed or customized variants of commodity RATs like BlotchyQuasar, a variant of QuasarRAT.
In this blog, we focus on BlindEagle’s use of the BlotchyQuasar RAT to target the Colombian insurance sector to steal payment-related data.
Key Takeaways
- Beginning in June 2024, BlindEagle was observed targeting the Colombian insurance sector.
- Attacks have originated with phishing emails impersonating the Colombian tax authority.
- BlindEagle has leveraged a version of BlotchyQuasar for attacks, which is heavily protected by several nested obfuscation layers.
- Zscaler ThreatLabz uncovered additional malicious domains that are likely used by this threat actor.
Technical Analysis
Overview
A BlindEagle attack chain typically originates with a phishing email that contains a PDF attachment and a URL that points to a ZIP archive file. The PDF attachment contains the same URL as the one provided in the email body. In other words, the ZIP file can be either downloaded from the PDF or directly from the email.
Upon clicking the URL (in either the email body or PDF), the victim downloads a ZIP archive from a Google Drive folder. This specific folder is under the ownership of a compromised account belonging to a regional government organization in Colombia. The ZIP archive contains a .NET BlotchyQuasar executable.
The figure below provides for a high-level overview of the attack chain.
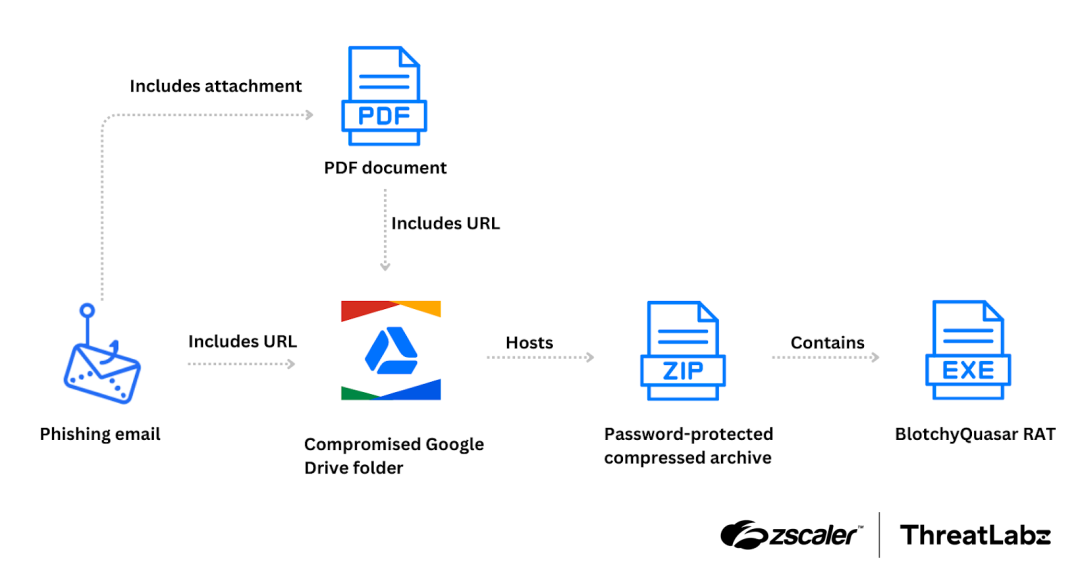
Figure 1: A high-level overview of a BlindEagle attack chain, where the initial phishing email includes a download URL for a password-protected compressed archive and the final payload is a packed BlotchyQuasar sample.
Phishing email as initial vector
In the phishing email, the threat actor impersonated the Dirección de Impuestos y Aduanas Nacionales (DIAN), which is the Colombian National Tax and Customs Authority. The lure used by BlindEagle involved sending a notification to the victim, claiming to be a seizure order due to outstanding tax payments. This is intended to create a sense of urgency and pressure the victim into taking immediate action. Our observations indicate that a substantial number of the targeted individuals are employees within the Colombian insurance industry.
The figure below shows the phishing email, which includes the PDF and download URL, spoofing the Colombian tax authority.

Figure 2: Example BlindEagle phishing email spoofing DIAN with a PDF attachment and malicious link in the email body.
The download URL directs the victim to a password-protected ZIP archive. The password necessary to open the archive is provided within the email body.
This ZIP archive is hosted on a Google Drive folder, which is associated with a compromised Gmail account owned by a government organization with a “.gov.co” top-level domain.
Based on analysis of the phishing email’s metadata, the threat actor likely sent the emails from their own infrastructure. Specifically, the first header received in the email indicates that the message originated from the IP address 69.167.8.118, which is associated with Powerhouse Management VPN. Powerhouse Management is a VPN service known to be utilized by BlindEagle to obfuscate the true source of their malicious activities and acquire IP addresses that are geographically close to their intended targets.
BlotchyQuasar
BlotchyQuasar is a powerful RAT that possesses a wide range of capabilities. It can log keystrokes, execute shell commands, and perform various other functions. Since BlotchyQuasar is a variant of QuasarRAT, we will not delve into a detailed analysis of its functionalities. Instead, in the following sections, we will concentrate on specific aspects that have not been extensively covered in previous publications.
Loader
As shown in the figure below, BlotchyQuasar is concealed within multiple layers of protection. Each layer consists of a .NET executable that has been safeguarded using either commercial or open-source obfuscators like DeepSea or ConfuserEx. These obfuscators are employed to make the code more complex and challenging to analyze, hindering reverse engineering attempts.

Figure 3: Nested structure of the BlotchyQuasar sample.
Layer 1 is the outer executable file that is contained within the ZIP archive. It decrypts the Layer 2 data that is contained in a resource named vh by utilizing a custom XOR-based algorithm. Layer 2 consists of a DLL with the name SimpleLogin.dll. When executed, SimpleLogin.dll loads and extracts the contents of a GZip-compressed resource named key0. Within this resource lies another DLL, Gamma.dll, which provides a utility for converting integers to Unicode characters. This utility is used to compose the name of a resource within Layer 1, which is subsequently loaded by SimpleLogin.dll. This resource is named HSOm and is stored as a bitmap image that undergoes a transformation process. This transformation involves discarding the last 150 rows and the last 150 columns of the image. Additionally, the row and column pixel coordinates are inverted. The figure below shows the bitmap when rendered.

Figure 4: The resource HSOm rendered as a bitmap containing the Layer 3 data.
By extracting the ARGB coordinates from each pixel, another DLL named Tyrone.dll is obtained. This DLL represents Layer 3, which decrypts the final payload by loading a resource named SIxfc1 and applying a custom XOR-based algorithm. This produces an executable file named Client.exe, which is a BlotchyQuasar malware sample.
Obtaining the C2
The installation steps completed by BlotchyQuasar are discussed in a previous publication. In the sample we analyzed, we observed a similar process. However, the procedure employed to obtain the command-and-control (C2) domain has not been previously analyzed.
When BlotchyQuasar is executed, the C2 server location is retrieved from Pastebin. The specific URL used to fetch the paste is hXXps://pastebin[.]com/raw/XAfmb6xp. The content of the paste is an encrypted string, as shown in the example below. (The relevant part is highlighted in bold and separated by the two “¡” symbols.)
GNNwsubynrt5oCZ+pAP97K9Sizq1eRn8XQQ8yxktdrbYQL263pZf+aQwkap8YEa09tg1w69qsZYEwGWF482CW3WBNKOJESQBz8IXYNzbbf+jrHUcNUEjV0lhaeAINnCtkqrp2l8esXBEB4rFHUqROAAwi¡CllIOSeGR/pSE1OqzWOtN5zIKVp5TOLPJ1rBUGNg5fA=¡GViPOxT6+nDuUYPCfRyIL0TFRvVOl4JGV9SCkyJUZQo06AvBlwsvaGwpLuv2q6UltL3e0awC1mmp0Cpfg7hAAmY4RpG+qIBxOYnqhLSbyuOAaWlMH4PxrqJ6p35T6Xg2+Z8esryidjlXGJVTWLISvofA2+vX4747n1lVUv4030D6Ds6NyAPHk9mRoDDsqRtW9g+xR0r479umTn8nb7wBCx5tOw2zqnWxpdGkyOrDIEcvb+cHDrA0geAclmePsRIi4CYe3ka41EMQMscoQ+2iUa43AM
This encrypted string is divided into three parts, with the symbol “¡” serving as a separator. Of particular interest is the middle part, enclosed by the separators (i.e., CllIOSeGR/pSE1OqzWOtN5zIKVp5TOLPJ1rBUGNg5fA=).This string is Base64 decoded and decrypted using standard 3DES encryption in ECB mode with PKCS7 padding. The 3DES key used is derived from the MD5 hash of the string qualityinfosolutions. In the provided example, the resulting C2 domain is edificiobaldeares.linkpc[.]net. The C2 communication for this sample leveraged the hardcoded port 9057.
Monitoring the consumption of banking & payment services
BlotchyQuasar implements a multitude of features, including the ability to monitor a victim’s interactions with specific banking and payment services. In order to identify such events, the malware examines the title of each newly opened window. If the window title contains certain predefined strings associated with the targeted services, BlotchyQuasar logs a reference to indicate the occurrence of the interaction.
The figure below shows an example log collected with references to several banking and payment services. In the example provided, websites for Banco Coomeva, Banco of Machala, and PayPal services were accessed. The log, in this case, is a simple XML document that contains all the references within elements labeled as NameCliente. This log file, named settings.xml, is stored on the disk within the startup folder of the compromised system.

Figure 5: Example BlotchyQuasar log containing references to the victim’s interaction with specific banking and payment service providers.
The table below lists the organizations that BlotchyQuasar targets. Since the list mainly includes Colombian and Ecuadorian banks, the malware was most likely designed to target individuals in those countries.
|
Organization |
Location |
|---|---|
|
BBVA |
Global |
|
Banco AV Villas |
Colombia |
|
Banco Bolivariano |
Ecuador |
|
Banco Caja Social |
Colombia |
|
Banco Coomeva |
Colombia |
|
Banco Davivenda |
Colombia |
|
Banco Guayaquil |
Ecuador |
|
Banco Internacional |
Ecuador |
|
Banco Pichincha |
Ecuador |
|
Banco Popular Colombia |
Colombia |
|
Banco de Bogotá |
Colombia |
|
Banco de Machala |
Ecuador |
|
Banco de la Producción |
Ecuador |
|
Banco del Austro |
Ecuador |
|
Banco del Pacifico |
Ecuador |
|
Bancolombia |
Colombia |
|
PayPal |
Global |
|
Scotiabank Colpatria |
Colombia |
|
TransUnion |
Global |
Table 1: List of banking and payment service providers targeted by BlotchyQuasar.
Keylogging
BlotchyQuasar provides keylogging functionality, with the keylogging module set to flush logs every 15 seconds. These logs are stored in the %APPDATA%GPrets directory with the filename format MM-dd-yyyy (e.g., 06-18-2024). The log file is structured according to the figure below, which details the captured keylogging data.

Figure 6: Structure of a BlotchyQuasar key log.
The initial 32 bytes of the encrypted log file comprise an HMAC SHA256 hash of the remaining content that is used as an integrity check. The subsequent 16 bytes store an AES initialization vector (IV) that is randomly generated per file. The AES key is hardcoded within the malware’s configuration class. In the sample analyzed by ThreatLabz, the AES key was represented by the Base64-encoded string 1WvgEMPjdwfqIMeM9MclyQ==. BlotchyQuasar uses AES in CBC mode (Cipher Block Chaining) with PKCS7 padding. The remaining portion of the file following the IV encompasses the encrypted log data itself.
A Python implementation of the BlotchyQuasar keylogging decryption routine is shown in the code sample below.
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
def decrypt(log: bytes, key: bytes) -> bytes:
encrypted_payload = log[48:]
iv = log[32:48]
cypher = AES.new(
key,
AES.MODE_CBC,
iv
)
decrypted_payload = cypher.decrypt(encrypted_payload)
block_size = cypher.block_size
decrypted_payload = unpad(decrypted_payload, block_size, "pkcs7")
return decrypted_payloadAs illustrated in the figure below, the decrypted logs are stored in HTML format.

Figure 7: Example decrypted key log data created by BlotchyQuasar.
Stealing capabilities
BlotchyQuasar targets the browser and FTP client applications shown in the table below.
|
Application |
Type |
Targeted Data |
|---|---|---|
|
Chrome |
Browser |
|
|
Chromium |
Browser |
|
|
Internet Explorer |
Browser |
|
|
Firefox |
Browser |
|
|
Opera |
Browser |
|
|
Yandex |
Browser |
|
|
FileZilla |
FTP client |
|
|
WinSCP |
FTP client |
|
Table 2: Applications targeted by BlotchyQuasar for information-stealing purposes.
Infrastructure
BlotchyQuasar accesses Pastebin to retrieve the current C2 domain. The structure of the Pastebin content and the decryption procedure is unique, which enabled us to identify additional pastes consumed by BlotchyQuasar samples. By successfully decrypting these pastes, we uncovered three more C2 domains:
- equipo.linkpc[.]net
- perfect5.publicvm[.]com
- perfect8.publicvm[.]com
All those domains share a few characteristics:
- First, these domains are extensions of second-level domains (SLDs) associated with Dynamic DNS service providers. Second, they exhibit a consistent pattern in their resolution history. Specifically, they predominantly resolve to IP addresses that belong to two primary sets. The first set comprises nodes associated with specific VPN services, namely Powerhouse Management, PrivateVPN, and ParadiseNetworks.
- The second set comprises IP addresses associated with specific Colombian internet service providers (ISPs), namely Colombia Movil, Telmex Colombia, and Tigo. These IP addresses are likely indicative of compromised routers. This information aligns with publicly disclosed findings about the infrastructure under the control of the BlindEagle threat actor.
By shifting our focus towards resolving IP addresses, we gained further insights into the infrastructure underpinning operations similar to the one described in this blog. We discovered additional domains that exhibited similar characteristics. While we lack sufficient information to definitively establish that these domains are controlled by the same threat actor, they continue to pose threats to individuals and organizations. Notably, these domains have been utilized, and may still be in use, as C2 servers for various commodity malware families, including njRAT, QuasarRAT, RevengeRAT, and others. It is crucial to remain vigilant as these domains could potentially be employed for malicious activities in the future.
As an example, the table below displays the date of first submission on VirusTotal of various QuasarRAT samples communicating with the domain edificiobaldeares.linkpc[.]net. This domain has been utilized as a C2 server since July 2022 and active until March 2024. Since a similar pattern repeats in other domains, we strongly recommend blocking them.
|
First Submission Date |
MD5 |
Malware Family |
|---|---|---|
|
18-07-2022 |
a73057824a65a5ac982e298a80febf61 |
QuasarRAT |
|
21-07-2022 |
bd4505316254f00329431fb8b2888643 |
QuasarRAT |
|
22-07-2022 |
d2fc372302180fbabe18c425aa4a0a72 |
QuasarRAT |
|
22-07-2022 |
c944cb638364c74431bf1dbe7dd329ff |
QuasarRAT |
|
24-07-2022 |
64e6ad512eff12e971efdd8979086c5c |
QuasarRAT |
|
26-07-2022 |
a1f5091ad4e12f922a8e760e0980ab66 |
QuasarRAT |
|
29-07-2022 |
ad578125b337168c976ff5e7e1b190b8 |
QuasarRAT |
|
01-08-2022 |
e21b4c9d9da81deea2381f9b988b0f99 |
QuasarRAT |
|
04-08-2022 |
07f661aeeb0774f0cb84b0a5e970c2a5 |
QuasarRAT |
|
09-08-2022 |
c4a946903cc9e9a84763ac1731cdd7dd |
QuasarRAT |
|
11-08-2022 |
75a40cc019c39e3c2800fb2fe5aba1d3 |
QuasarRAT |
|
12-08-2022 |
0fa40788b75896a452398b6a49cc62b6 |
QuasarRAT |
|
15-08-2022 |
59a4f7aed1e3a0718592fb536e987a1d |
QuasarRAT |
|
16-08-2022 |
456211df625002df378cf0f4af9d1a6f |
QuasarRAT |
|
17-08-2022 |
0f35306ad4fede9a9ba0276a5e788138 |
QuasarRAT |
|
19-08-2022 |
6044b126afb86682b4a3440e2924c079 |
QuasarRAT |
|
19-08-2022 |
b432e8ff5797fbaf5808d95d46524647 |
QuasarRAT |
|
20-08-2022 |
a31ff54f33ced7b4180f87afb18185a7 |
QuasarRAT |
|
20-08-2022 |
e3239ac16c6fe9c99d6fac0867121a88 |
QuasarRAT |
|
07-07-2023 |
2784a9fc64d244b14e7d8e4d03f41265 |
QuasarRAT |
|
06-03-2024 |
3125ae6b1462b0b48dc06bc47d8ddbc7 |
QuasarRAT |
Table 3: The most recent recorded interactions between various QuasarRAT malware samples and the domain edificiobaldeares.linkpc[.]net.
Attribution
We attribute this attack to the threat actor known as BlindEagle with medium to high confidence. Our attribution claim is supported by the following:
- Spoofing DIAN in the phishing email and using a tax-related lure are both documented characteristics of BlindEagle.
- BlindEagle is recognized for employing customized or repurposed variants of commodity or open-source malware as their final payload, as mentioned here and here. In this particular case, they utilized BlotchyQuasar, which is a variant of QuasarRAT, an RAT.
- The extensive usage of Dynamic DNS (DDNS) services to host the C2 domain is another common strategy employed by BlindEagle throughout their operations, as indicated in past documented cases. In this attack, the threat actor utilized linkpc as a DDNS provider, which aligns with their previous choices.
- BlindEagle typically shields its infrastructure behind a combination of VPN nodes and compromised routers, primarily located in Colombia. This attack demonstrates the continued use of this strategy, with the C2 domains resolving to IP addresses associated with known providers frequently adopted by the threat actor, such as the Powerhouse Management VPN service, which is also used to acquire IP addresses geographically close to the targets. Additionally, the C2 domains sometimes resolve to IP addresses belonging to Colombian ISPs (e.g., Colombia Movil, Telmex, or Trigo), suggesting the involvement of compromised routers.
The victims targeted in this attack align with the victimology profile previously established for BlindEagle. The known targets were Colombian individuals employed in organizations operating within the Colombian insurance industry. This nationality and vertical are consistently targeted by the threat actor.
Conclusion
As part of our monitoring and research efforts, ThreatLabz discovered a BlindEagle campaign targeting the Colombian insurance sector. The threat actor employed phishing emails that impersonated DIAN (a Colombian tax collection agency) to gain initial access to the victims’ systems. These emails contained links and passwords to download and open compressed archive files hosted on compromised Google Drive folders. The contents of these archives were instances of the BlotchyQuasar RAT, which grants the threat actor a wide range of capabilities, including keylogging, monitoring of bank services, and stealing information from various applications.
Zscaler ThreatLabz anticipates that BlindEagle will continue launching malware campaigns in the future. We remain vigilant in monitoring the activity of this threat actor to ensure our customers are well-protected against this threat.
Zscaler Coverage

Figure 8: Zscaler sandbox report for the BlotchyQuasar sample.
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators related to BlindEagle at various levels with the following threat names:
- Win32.Trojan.BlindEagle
- HTML.Malurl.Gen.LZ
- HTML.Malurl.Gen.NC
- HTML.Malurl.Gen.TT
- HTML.Phish.Gen.LZ
- Win32.Backdoor.Asyncrat.BS
- Win32.Backdoor.Bladabindi.LZ
- Win32.Backdoor.Dcrat.BS
- Win32.Backdoor.Nanocore.BS
- Win32.Backdoor.Njrat.BS
- Win32.Backdoor.Quasarrat.LZ
- Win32.Backdoor.Remcosrat.BS
- Win32.Backdoor.Smokeloader.BS
- Win32.Trojan.Agent
Indicators Of Compromise (IOCs)
|
Indicator |
Description |
|---|---|
|
b83f6c57aa04dab955fadcef6e1f4139 |
MD5 hash of the BlotchyQuasar sample. |
|
a68cac786b47575a0d747282ace9a4c75e73504d |
SHA1 hash of the BlotchyQuasar sample. |
|
ec2dd6753e42f0e0b173a98f074aa41d2640390c163ae77999eb6c10ff7e2ebd |
SHA256 hash of the BlotchyQuasar sample. |
|
hXXps://pastebin[.]com/raw/XAfmb6xp |
Paste containing the encrypted C2 domain of BlotchyQuasar. |
|
edificiobaldeares.linkpc[.]net |
BlotchyQuasar C2 domain for the analyzed sample. |
|
equipo.linkpc[.]net |
Additional BlotchyQuasar C2 domain. |
|
perfect5.publicvm[.]com |
Additional BlotchyQuasar C2 domain. |
|
perfect8.publicvm[.]com |
Additional BlotchyQuasar C2 domain. |
In addition to those indicators, we added malicious domains likely belonging to the threat actor to our GitHub repository.
MITRE ATT&CK Profile
|
ID |
Technique |
Annotation |
|---|---|---|
|
T1583.001 |
Acquire Infrastructure: Domains |
BlindEagle uses DDNS services to create third level domains. Those domains serve as C2. |
|
T1586.002 |
Compromise Accounts: Email Accounts |
BlindEagle controlled a Google Drive folder owned by a Colombian, regional, administration organization. |
|
T1587.001 |
Develop Capabilities: Malware |
BlindEagle is operating BlotchyQuasar, which may be considered a customized variant of QuasarRAT. |
|
T1608.001 |
Stage Capabilities: Upload Malware |
BlindEagle staged a BlotchyQuasar sample on a compromised and publicly available Google Drive folder. |
|
T1566.002 |
Phishing: Spearphishing Link |
BlindEagle attempted to gain initial access to the victim’s system by using a phishing email including a link to download BlotchyQuasar malware. |
|
T1204.002 |
User Execution: Malicious File |
BlindEagle renamed the BlotchyQuasar sample to be consistent with the phishing email lure and push the victim to manually execute the malware. |
|
T1204.001 |
User Execution: Malicious Link |
BlindEagle’s attack chain starts with the victim clicking on a link included in the email body and in the attached PDF file. |
|
T1547.001 |
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
BlotchyQuasar achieves persistence by setting a RunKey. |
|
T1053.005 |
Scheduled Task/Job: Scheduled Task |
BlotchyQuasar creates a scheduled task that launches itself every 3 minutes. |
|
T1562.001 |
Impair Defenses: Disable or Modify Tools |
If executed with elevated privileges, BlotchyQuasar attempts to disable several Defender features. |
|
T1564.001 |
Hide Artifacts: Hidden Files and Directories |
BlotchyQuasar creates hidden directories to store keylogger files. |
|
T1027.003 |
Obfuscated Files or Information: Steganography |
One of the protection layers included in the BlotchyQuasar loader is decrypted starting from a Bitmap image included as a .NET-managed resource. |
|
T1027.009 |
Obfuscated Files or Information: Embedded Payloads |
BlotchyQuasar malware is buried under three layers of encrypted code. Those nested code layers are embedded as .NET-managed resources and decrypted with custom XOR-based algorithms. |
|
T1027.013 |
Obfuscated Files or Information: Encrypted/Encoded File |
BlotchyQuasar stores the keylogger logs after encrypting them with AES. |
|
T1553.005 |
Subvert Trust Controls: Mark-of-the-Web Bypass |
BlotchyQuasar deletes the Zone.Identifier ADS (mark-of-the-web) from the original executable to bypass the MOTW. |
|
T1027.002 |
Obfuscated Files or Information: Software Packing |
Some of the protection layers of the BlotchyQuasar loader are obfuscated with .NET obfuscators, such as DeepSea or ConfuserEx. |
|
T1140 |
Deobfuscate/Decode Files or Information |
The BlotchyQuasar C2 domain is decrypted with AES. |
|
T1056.001 |
Input Capture: Keylogging |
BlotchyQuasar is capable of logging keystrokes. |
|
T1539 |
Steal Web Session Cookie |
BlotchyQuasar is capable of stealing cookies and passwords from popular browsers and FTP clients. |
|
T1056.002 |
Video Capture |
BlotchyQuasar is capable of controlling the webcams of the infected system. |
|
T1095 |
Non-Application Layer Protocol |
BlotchyQuasar establishes a socket-based C2 channel. |
|
T1041 |
Exfiltration Over C2 Channel |
BlotchyQuasar is capable of exfiltrating stolen information (keylogs, video recordings, and more) over the C2 channel. |
|
T1490 |
Inhibit System Recovery |
If executed with high privileges, BlotchyQuasar deletes the shadow copies with the vssadmin utility. |
Source: Original Post