Summary: The analysis by Cybereason highlights the evolving capabilities of Beast Ransomware, a Ransomware-as-a-Service (RaaS) platform that has been actively targeting various organizations since 2022. With customizable options and cross-platform functionality, Beast poses a significant threat to both Windows and Linux systems, leveraging advanced encryption techniques and self-propagation mechanisms.
Threat Actor: Beast Ransomware Group | Beast Ransomware Group
Victim: Organizations globally | organizations globally
Key Point :
- Beast Ransomware offers customizable binaries for various operating systems, including Windows, Linux, and ESXi, allowing affiliates to tailor attacks.
- The ransomware employs advanced encryption methods and a self-propagation mechanism, enabling rapid infection across networks.
- Beast specifically avoids encrypting systems in CIS countries to evade local law enforcement attention.
- It targets shadow copies on Windows systems to prevent victims from recovering files through backups.
- Recent updates include an offline builder, enhancing the malware’s versatility for targeted attacks without internet access.
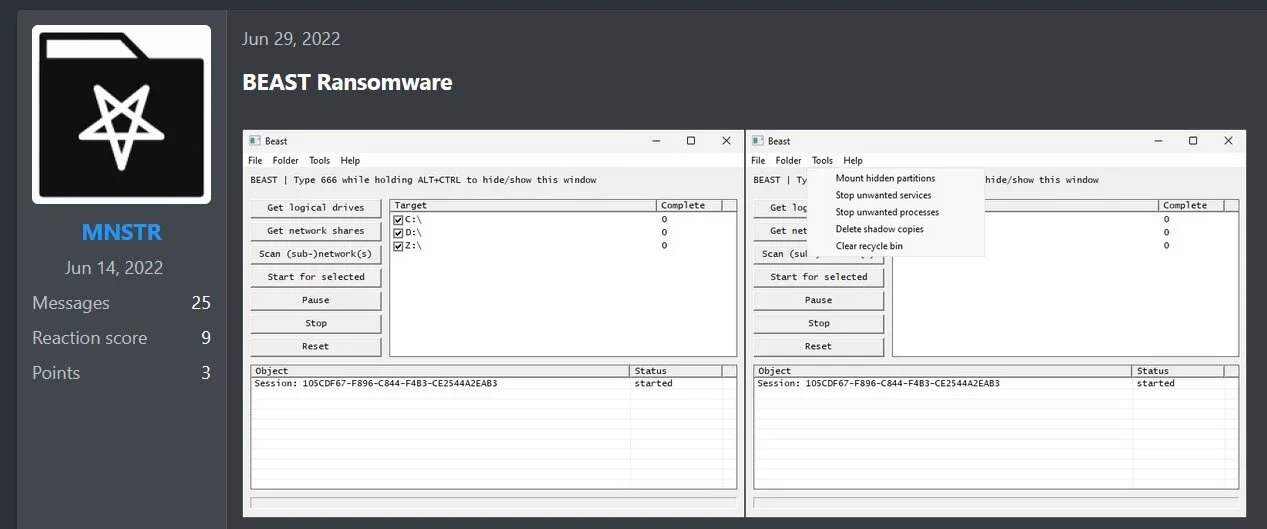
In a recent analysis by Cybereason, security researcher Mark Tsipershtein delves into the intricacies of Beast Ransomware, a Ransomware-as-a-Service (RaaS) platform that has been actively targeting organizations since 2022. Beast, also known as Monster, continues to evolve, with new features and customizable options allowing affiliates to adapt the malware for a variety of targets across different operating systems, including Windows, Linux, and VMware ESXi servers.
As the underground cybercrime ecosystem continues to expand, so does the popularity of RaaS platforms like Beast. “The Beast Ransomware group provides various tools with constant version updates. These updates are made to appeal to wider audiences across the underground cybercrime ecosystem,” Cybereason’s report reveals. This flexibility makes Beast a favorite among cybercriminals looking to deploy ransomware in a targeted, efficient manner, leveraging customizable binary options to suit their specific needs.
The Beast Ransomware platform allows attackers to tailor their payloads for maximum impact. Affiliates can build binaries to encrypt files on Windows, Linux, and ESXi systems. For Windows systems, the encryption process uses a combination of Elliptic-curve cryptography and ChaCha20 encryption models, ensuring robust file encryption. The ransomware also features a multithreaded queue for faster file encryption and terminates critical services before encrypting data to avoid interference from open files.
What sets Beast apart is its ability to seamlessly operate across multiple platforms. The Windows version supports capabilities like ZIP wrapper mode, where files are converted into .zip files with ransom notes embedded inside, and subnet scanning to identify and infect nearby systems(ransom). Meanwhile, the Linux and ESXi versions offer attackers additional flexibility, such as shutting down virtual machines (VMs) before encrypting their files, further disrupting the target’s operations.
In August 2024, Beast added an offline builder that allows affiliates to create ransomware tailored to target Windows, NAS, and ESXi systems without needing an internet connection. This feature significantly boosts the malware’s versatility, providing attackers with offline capabilities to generate unique payloads for various environments.
One of the most dangerous aspects of Beast is its self-propagation mechanism. By performing SMB scans, the ransomware automatically searches for and infects vulnerable systems on the same network. This allows Beast to spread rapidly without requiring manual intervention, making it highly effective in large-scale attacks.
Interestingly, Beast avoids encrypting systems located in Commonwealth of Independent States (CIS) countries, including Russia, Belarus, and Moldova. This is achieved by checking the system’s default language settings, country code, and IP address. If the ransomware detects a CIS country, it halts its encryption activities, likely to avoid drawing attention from local law enforcement.
To ensure that victims cannot recover encrypted files through system backups, Beast ransomware targets shadow copies—a key feature in Windows systems that creates backups of files and folders. “Beast calls the IWbemServices::ExecQuery command to query and delete shadow copies, ensuring that no backup copies of encrypted files remain,” the report explains. This step is critical in preventing victims from using system restores to circumvent the ransomware attack.
Related Posts:
Source: https://securityonline.info/beast-ransomware-raas-platform-targets-windows-linux-and-vmware-esxi