Threat Actor: N/A | N/A Victim: N/A | N/A
Key Point :
Funding rounds decreased by 16%, from 346 to 304, but total raised amount increased by 9% year-over-year.…
Threat Actor: N/A | N/A Victim: N/A | N/A
Key Point :
Funding rounds decreased by 16%, from 346 to 304, but total raised amount increased by 9% year-over-year.…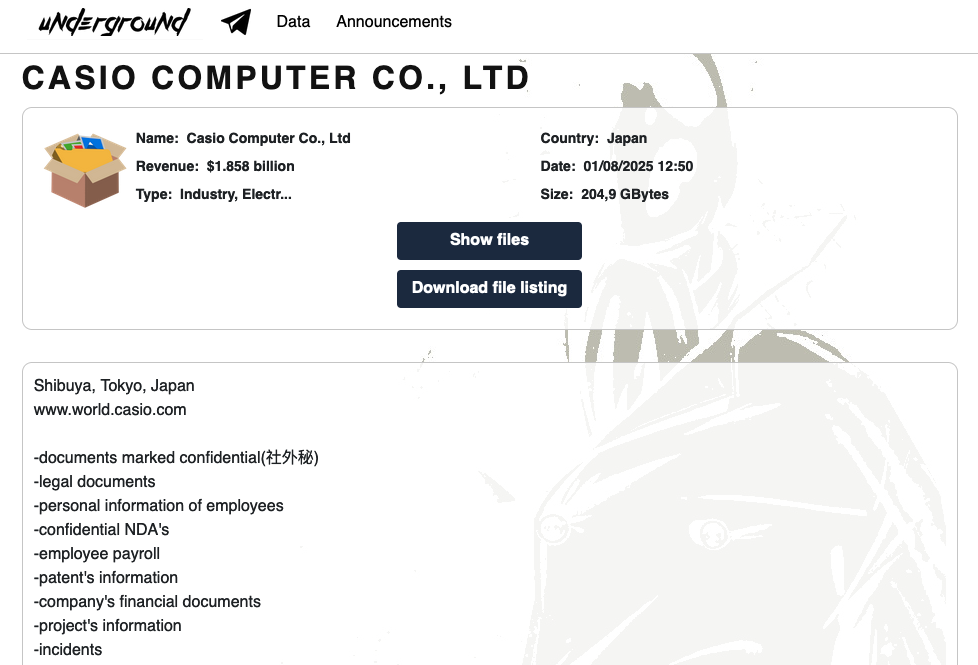
Threat Actor: Underground | Underground Victim: Casio | Casio
Key Point :
Approximately 6,500 employees’ personal information was compromised, including names, email addresses, and taxpayer IDs.…


Threat Actor: Unknown | unknown Victim: Browser Users | browser users
Key Point :
Google’s Chrome 131 update fixes four security defects, including a high-severity type confusion flaw in the V8 JavaScript engine.…
Threat Actor: Unknown | unknown Victim: Google Android Users | Google Android Users
Key Point :
Five critical vulnerabilities could lead to remote code execution on multiple Android versions.…
Threat Actor: Software Supply Chain Attackers | software supply chain attackers Victim: Software Supply Chain | software supply chain
Key Point :
Veracode’s acquisition of Phylum includes malicious package analysis and detection technology.…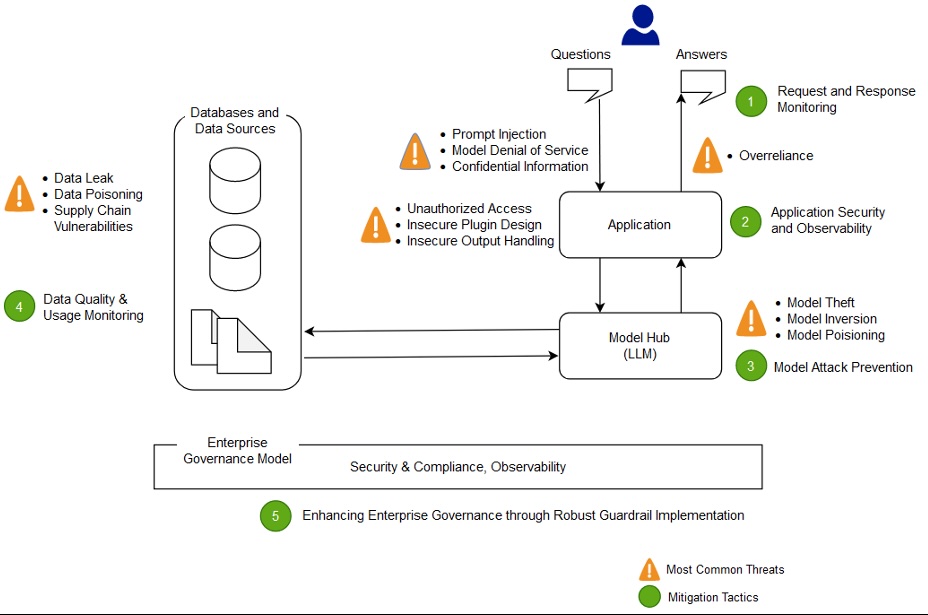


Key Point :
Rob Joyce will help identify and grow startups focused on cybersecurity at DataTribe.…
Threat Actor: John Binns | John Binns Victim: T-Mobile | T-Mobile
Key Point :
The 2021 breach affected over 76.6 million individuals, including more than 2 million Washington residents.…
Threat Actor: Unknown | unknown Victim: MediaTek, HPE, Dell | MediaTek, HPE, Dell
Key Point :
MediaTek patched a critical vulnerability (CVE-2024-20154) in its modem component that could allow remote code execution via rogue base stations.…
Threat Actor: Various | ransomware attackers Victim: Various | critical infrastructure organizations
Key Point :
The CIRA database has documented over 2,000 ransomware attacks since 2013, with a significant increase in larger ransom demands.…

Threat Actor: Tesla | Tesla Victim: Matthew Livelsberger | Matthew Livelsberger
Key Point :
Tesla’s data collection proved crucial for law enforcement in tracking the driver’s movements after a Cybertruck explosion.…