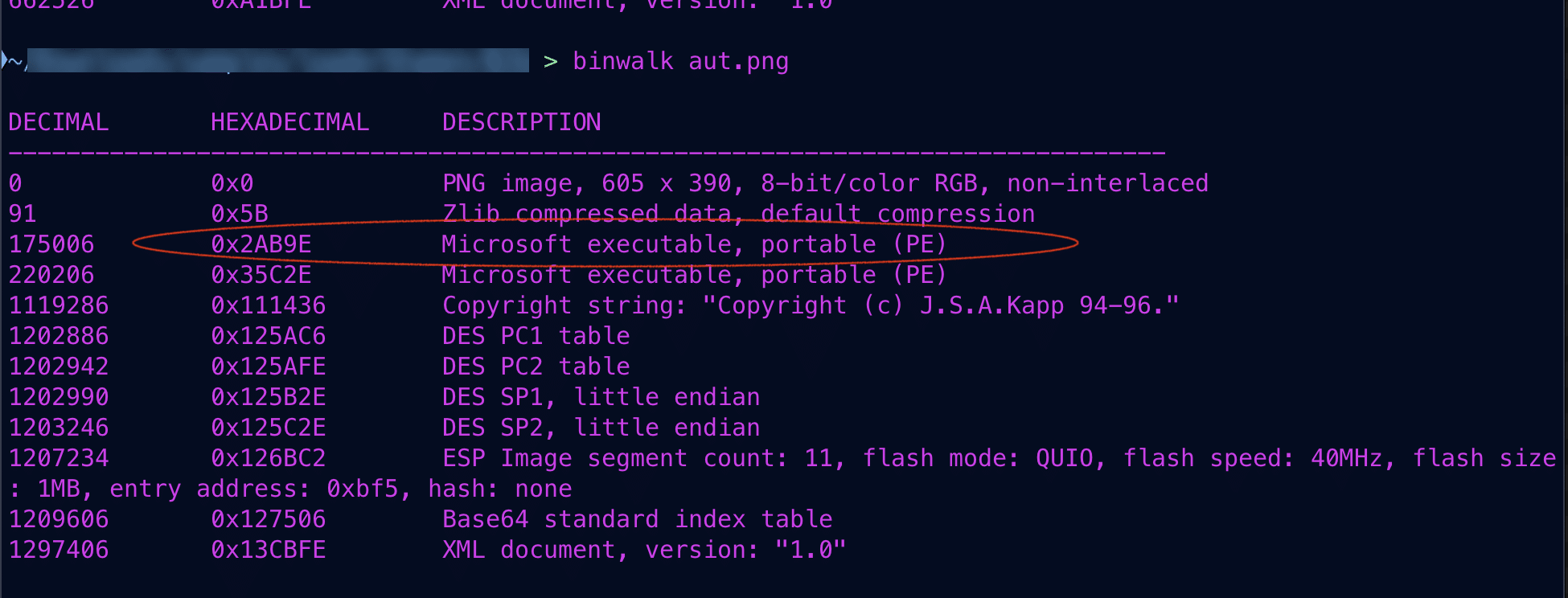
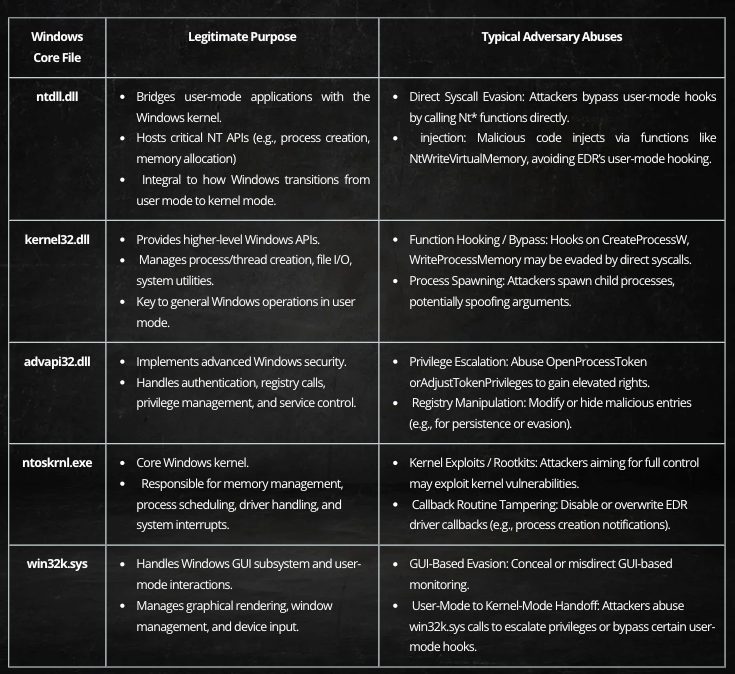
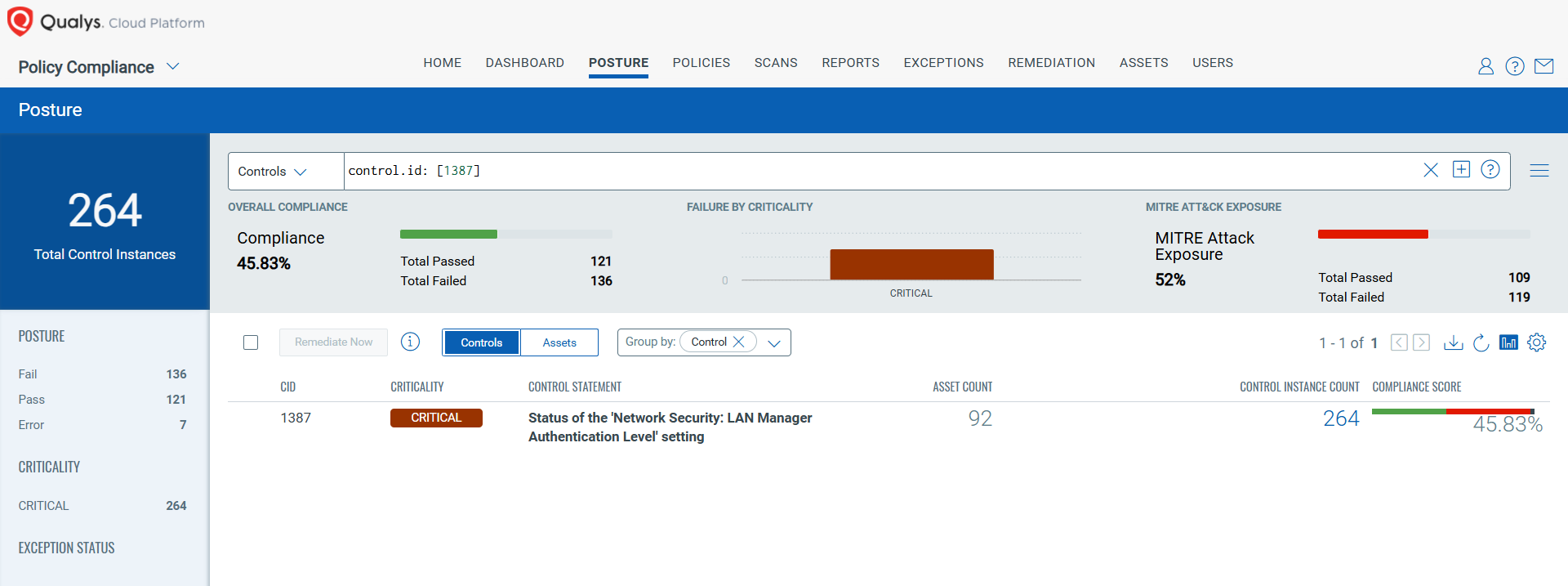
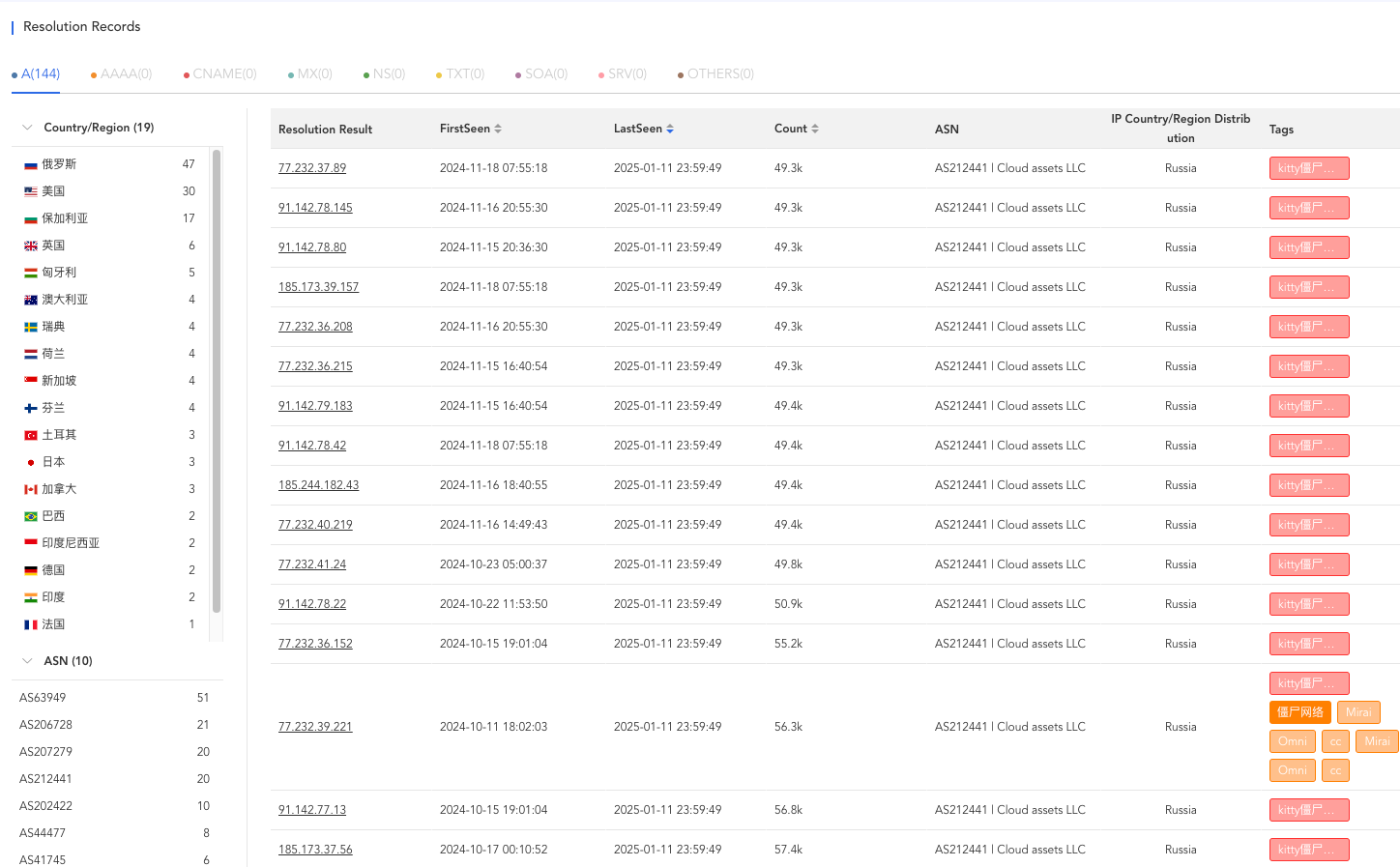
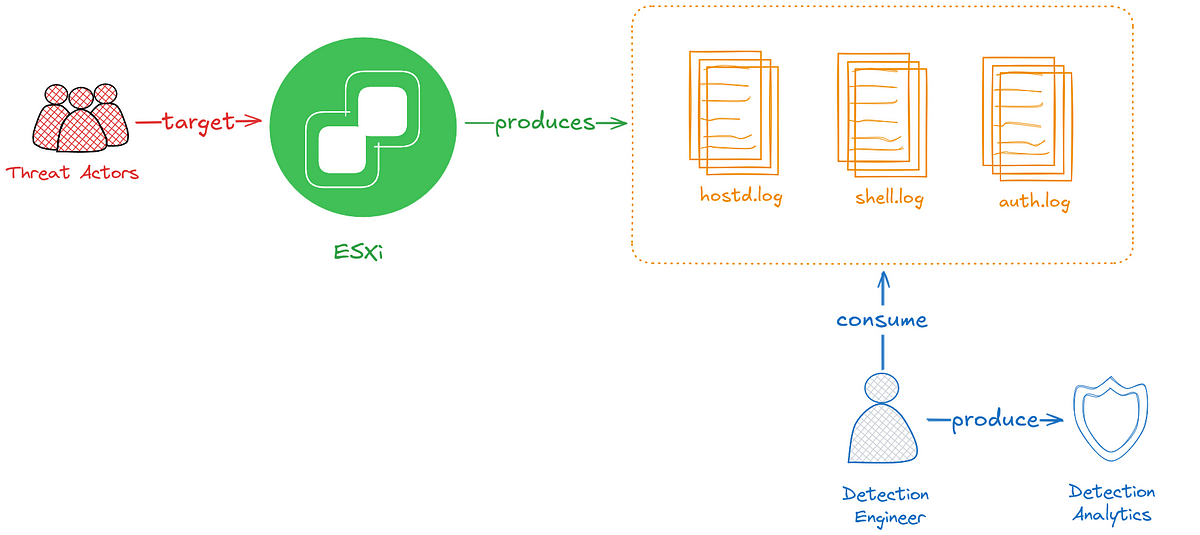
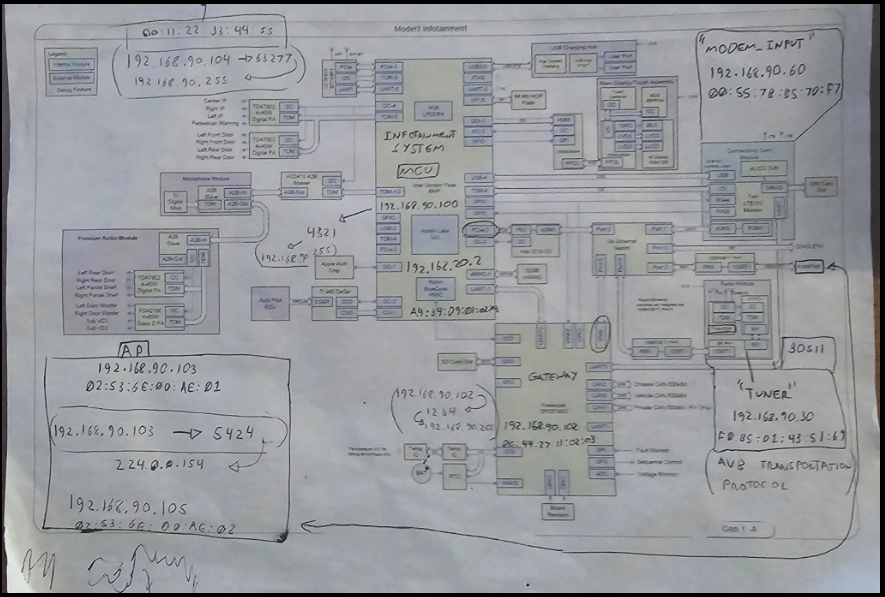
Keypoints :
Cookies collect anonymous data regarding user visits.…
This article discusses various cookies that collect anonymous data related to user visits on websites, including metrics such as the number of visits, average time spent, and pages loaded. These cookies serve to enhance user experience and enable targeted advertising. Affected: websites, advertising platforms
Read More