What happened
Proofpoint recently identified a SugarGh0st RAT campaign targeting organizations in the United States involved in artificial intelligence efforts, including those in academia, private industry, and government service. Proofpoint tracks the cluster responsible for this activity as UNK_SweetSpecter.
SugarGh0st RAT is a remote access trojan, and is a customized variant of Gh0stRAT, an older commodity trojan typically used by Chinese-speaking threat actors. SugarGh0st RAT has been historically used to target users in Central and East Asia, as first reported by Cisco Talos in November 2023.
In the May 2024 campaign, UNK_SweetSpecter used a free email account to send an AI-themed lure enticing the target to open an attached zip archive.
Analyst note: Proofpoint uses the UNK_ designator to define clusters of activity that are still developing and have not been observed enough to receive a numerical TA designation.
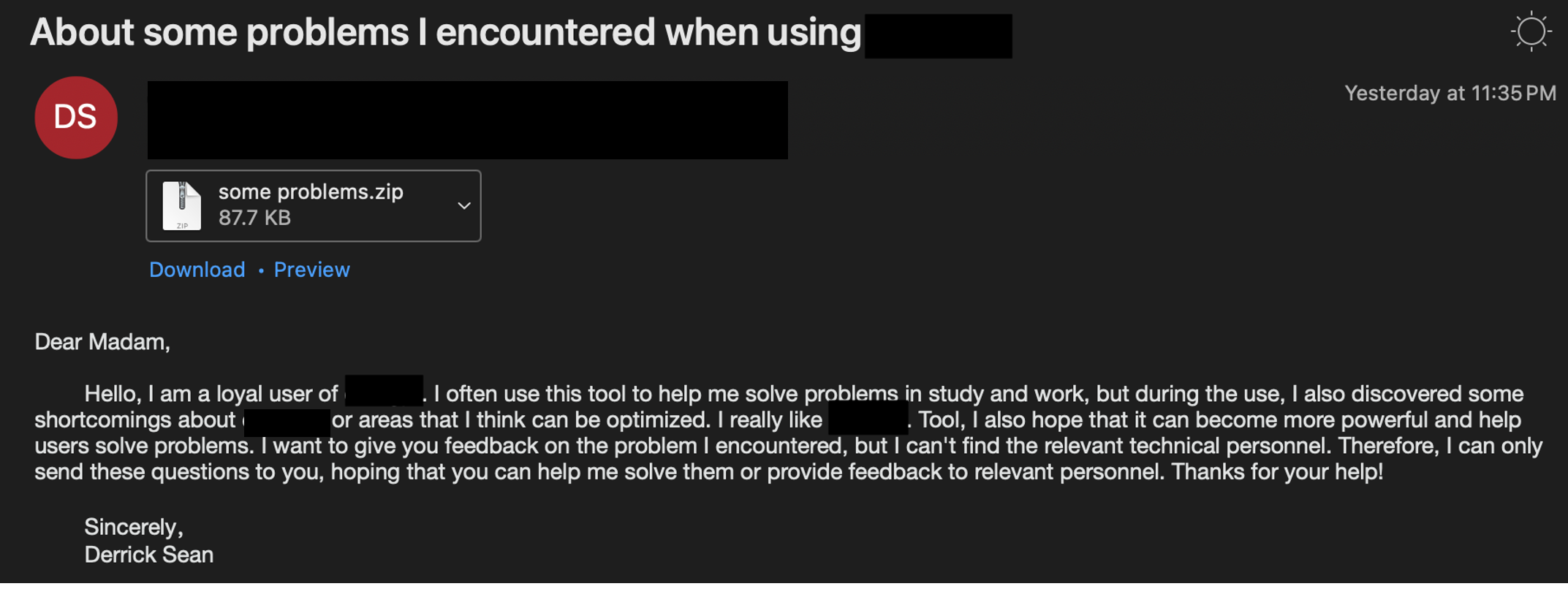
Lure email
Following delivery of the zip file, the infection chain mimicked “Infection Chain 2” as reported by Cisco Talos. The attached zip file dropped an LNK shortcut file that deployed a JavaScript dropper. The LNK was nearly identical to the publicly available LNK files from Talos’ research and contained many of the same metadata artifacts and spoofed timestamps in the LNK header. The JavaScript dropper contained a decoy document, an ActiveX tool that was registered then abused for sideloading, and an encrypted binary, all encoded in base64. While the decoy document was displayed to the recipient, the JavaScript dropper installed the library, which was used to run Windows APIs directly from the JavaScript. This allowed subsequent JavaScript to run a multi-stage shellcode derived from DllToShellCode to XOR decrypt, and aplib decompress the SugarGh0st payload. The payload had the same keylogging, command and control (C2) heartbeat protocol, and data exfiltration methods. The main functional differences in the infection chain Proofpoint observed compared to the initial Talos report were a slightly modified registry key name for persistence, CTFM0N.exe, a reduced number of commands the SugarGh0st payload could run, and a different C2 server. The analyzed sample contained the internal version number of 2024.2.
Network analysis
Threat Research analysis demonstrated UNK_SweetSpecter had shifted C2 communications from previously observed domains to account.gommask[.]online. This domain briefly shared hosting on 103.148.245[.]235 with previously reported UNK_SweetSpecter domain account.drive-google-com[.]tk. Our investigation identified 43.242.203[.]115 hosting the new C2 domain. All identified UNK_SweetSpecter infrastructure appears to be hosted on AS142032.
Context
Since SugarGh0st RAT was originally reported in November 2023, Proofpoint has observed only a handful of campaigns. Targeting in these campaigns included a U.S. telecommunications company, an international media organization, and a South Asian government organization. Almost all of the recipient email addresses appeared to be publicly available.
While the campaigns do not leverage technically sophisticated malware or attack chains, Proofpoint’s telemetry supports the assessment that the identified campaigns are extremely targeted. The May 2024 campaign appeared to target less than 10 individuals, all of whom appear to have a direct connection to a single leading US-based artificial intelligence organization according to open source research.
Attribution
Initial analysis by Cisco Talos suggested SugarGh0st RAT was used by Chinese language operators. Analysis of earlier UNK_SweetSpecter campaigns in Proofpoint visibility confirmed these language artifacts. At this time, Proofpoint does not have any additional intelligence to strengthen this attribution.
While Proofpoint cannot attribute the campaigns with high confidence to a specific state objective, the lure theme specifically referencing an AI tool, targeting of AI experts, interest in being connected with “technical personnel,” interest in a specific software, and highly targeted nature of this campaign is notable. It is likely the actor’s objective was to obtain non-public information about generative artificial intelligence.
The timing of the recent campaign coincides with an 8 May 2024 report from Reuters, revealing that the U.S. government was furthering efforts to limit Chinese access to generative artificial intelligence. It is possible that if Chinese entities are restricted from accessing technologies underpinning AI development, then Chinese-aligned cyber actors may target those with access to that information to further Chinese development goals.
Why it matters
For enterprise defenders facing a near constant onslaught of vulnerabilities and threats, monitoring targeted threat actors often seems like a herculean task. This campaign is an example of how it’s worth establishing baselines to identify malicious activity, even if the threat may not currently exist across an organization’s threat model. This activity also demonstrates how the operators of highly targeted spearphishing campaigns may find themselves relying on commodity tools for initial access.
Proofpoint Threat Research thanks the Yahoo! Paranoids Advanced Cyber Threats Team for their collaboration in this investigation.
Emerging Threats signatures
- ET MALWARE SugarGh0st RAT CnC Checkin
- UNK_SweetSpecter SugarGh0st CnC Domain in DNS Lookup
- UNK_SweetSpecter SugarGh0st CnC Domain in TLS SNI
Indicators of compromise
| Indicator | Description | First Observed |
| da749785033087ca5d47ee65aef2818d4ed81ef217bfd4bc07be2d0bf105b1bf | SHA256 some problems.zip | 2024-05-08 |
| 71f5ce42714289658200739ce0bbe439f6ef6fe77a5f6757b1cf21200fc59af7 | SHA256 some problems.lnk | 2024-05-08 |
| fc779f02a40948568321d7f11b5432676e2be65f037acfed344b36cc3dac16fc | SHA2256 ~235232302.js | 2024-05-08 |
| 4ef3a6703abc6b2b8e2cac3031c1e5b86fe8b377fde92737349ee52bd2604379 | SHA256 libeay32.dll | 2022-02-18 |
| feae7b2b79c533a522343ac9e1aa7f8a2cdf38691fbd333537cb15dd2ee9397e | SHA256 some_problems.docx | 2024-05-08 |
| account.gommask[.]online | SugarGh0st RAT C2 Domain | 2024-05-08 |
| 43.242.203[.]115 | SugarGh0st RAT C2 IP | 2024-05-08 |
Source: Original Post
Views: 0