Mustang Panda, also known as Bronze President, is a Chinese cyber threat actor, active since 2012. This group has launched cyberattacks against organizations worldwide, targeting foreign governments, NGOs, and other entities deemed adversaries of the Chinese Communist Party. Mustang Panda is notorious for its sophisticated spear-phishing campaigns, which utilize the target’s native language and often impersonate government services. These campaigns are crafted to exploit current international events, making the phishing emails appear highly legitimate to their intended victims.
Their primary tactic for initial penetration involves sending meticulously researched phishing emails, which closely resemble authentic documents relevant to the targeted individuals and their organizations. One of their hallmark techniques includes the use of the PlugX remote access trojan (RAT), a tool first identified by threat researchers in 2012. Since then, PlugX has been consistently employed by various Chinese cyber threat groups, including Mustang Panda, to facilitate their malicious activities.
Alias: Earth Preta, PKPLUG, Red Lich, RedDelta, Bronze President, Camaro Dragon, HoneyMyte, Luminous Moth, Stately Taurus, TA416, Temp.Hex
Motivation: Information theft and espionage

Targeted Countries
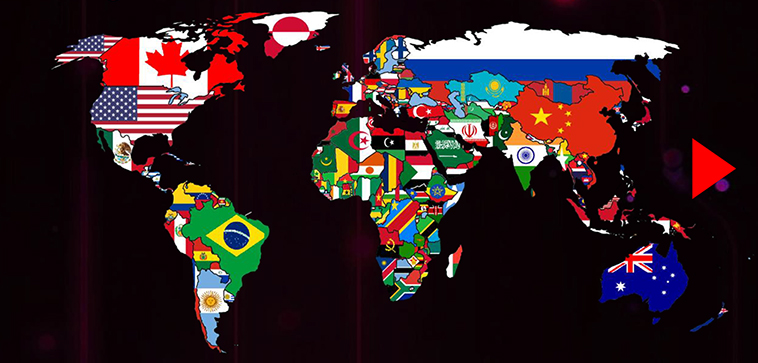
Australia, Bangladesh, Belgium, Bulgaria, China, Cyprus, Czech, Ethiopia, France, Germany, Greece, Hong Kong, Hungary, India, Indonesia, Japan, Mongolia, Myanmar, Nepal, Pakistan, Philippines, Russia, Singapore, Slovakia, South Africa, South Korea, South Sudan, Sweden, Taiwan, Thailand, Tibet, UK, USA, and Vietnam.
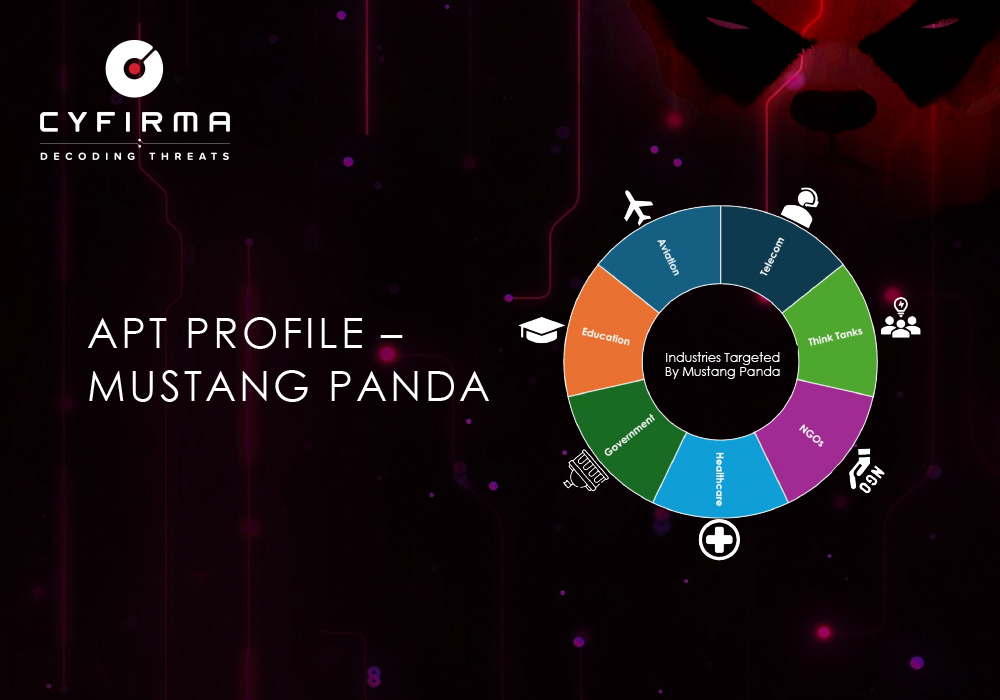
Mustang Panda Campaigns Tracked by CYFIRMA
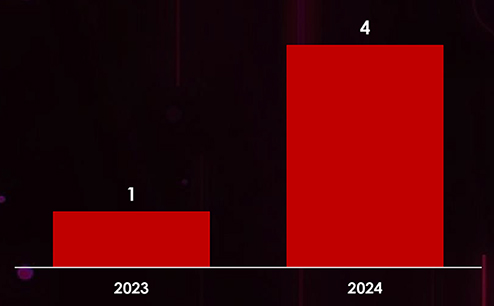
Recently Exploited Vulnerabilities by Mustang Panda
- CVE-2021-1675
- CVE-2021-34527
- CVE-2021-40444
Malware used by Mustang Panda
Horse Shell, WispRider, PlugX and Poison Ivy, DOPLUGS, MQsTTang, MirrorFace, Sogu
MITRE ATT&CK Techniques used by Mustang Panda
| Resource Development | Execution | Defense Evasion | Credential Access | Command and Control |
|---|---|---|---|---|
| T1585.002 | T1203 | T1036.007 | T1003.003 | T1573.001 |
| T1608.001 | T1047 | T1027 | Discovery | T1102 |
| T1608 | T1059.003 | T1027.001 | T1049 | T1071.001 |
| T1583.001 | T1053.005 | T1036.005 | T1016 | T1219 |
| Initial Access | T1204.001 | T1564.001 | T1057 | T1105 |
| T1566.001 | T1059.001 | T1070.004 | T1518 | |
| T1566.002 | T1204.002 | T1218.004 | T1082 | |
| T1091 | T1059.005 | T1574.002 | T1083 | |
| Persistence | Privilege Escalation | T1218.005 | Lateral Movement | |
| T1053.005 | T1053.005 | Collection | T1091 | |
| T1546.003 | T1546.003 | T1074.001 | Exfiltration | |
| T1574.002 | T1574.002 | T1560.001 | T1052.001 | |
| T1547.001 | T1547.001 | T1119 | ||
| T1560.003 |
Mustang Panda’s Recent Campaigns: Highlights and Trends
- In the recently observed campaigns, the primary targets have included the Ministry of Defense and Foreign Affairs departments of various governments in the APAC region, although the scope of targeting extends beyond these entities.
- Based on a recent campaign Mustang Panda has primarily focused on targeting government entities, particularly within the Asia-Pacific region and Europe. In the APAC region Mustang Panda activities are highly concentrated in Major Non-NATO Ally (MNNA) countries like Australia, Japan, South Korea, the Philippines, Thailand, and Taiwan as part of pre-positioning themselves to handle possible geopolitical conflicts in the region.
- In one of the campaigns, Mustang Panda employed an executable with a screensaver (SCR) file extension for initial infection, instead of their typical choice of relying on file archive formats (ZIP, RAR, ISO) for delivery highlighting their changing tactics in delivery.
- Mustang Panda has been known to use themed lures relating to various current-day events and issues, including the COVID-19 pandemic, international summits, and various political topics. That trend continued in the recently observed campaigns as well using high-profile summits, meetings, and natural disaster warnings.
- In recent campaigns, Mustang Panda has potentially employed spear phishing emails as an initial access vector to target high-ranking officials within government entities that are heavily involved in international collaborations.
Source: Original Post
Views: 0