The realm of cybersecurity is becoming more and more chaotic with each passing day, and there will always be a new actor entering the world of cybersecurity. The Dark Pink APT Group is one such entity that has recently caught the attention of security researchers and organizations worldwide. With a series of sophisticated cyberattacks under their belt, this group has become a topic of concern for many.
This article delves into the intricate details of the Dark Pink APT Group, shedding light on their campaigns, targets, and the security measures one can adopt to safeguard against malicious endeavors.

Who is Dark Pink APT?
The Dark Pink APT Group (as identified by Group-IB), also known as Saaiwc Group, is a sophisticated cyber-espionage group that has been active since at least 2021. Their operations are characterized by a high degree of stealth and precision, making them a formidable adversary in the cyber realm.
According to Group-IB, the actor was named because of the addresses blackpink.301@outlook[.]com and blackred.113@outlook[.]com that the actor used for exfiltration.

While the exact origins of this group remain a subject of debate among experts, some sources suggest a potential link to state-sponsored activities, hinting at the possibility of a nation-state sponsored. According to some researchers, Dark Pink APT is allegedly linked to OceanLotus, a Vietnamese state-sponsored threat actor. Also, as a result of our research, we noticed that Dark Pink exploited a vulnerability that was used by the Indian state-sponsored APT group APT-C-35.
In the light of these facts, at most we can identify the origin of the actor as being from Southeast Asia. In addition, this prediction can be supported by the fact that the time zone of the attack is based on Indochina Peninsula Standard Time according to Anheng Security Data Department’s analysis:
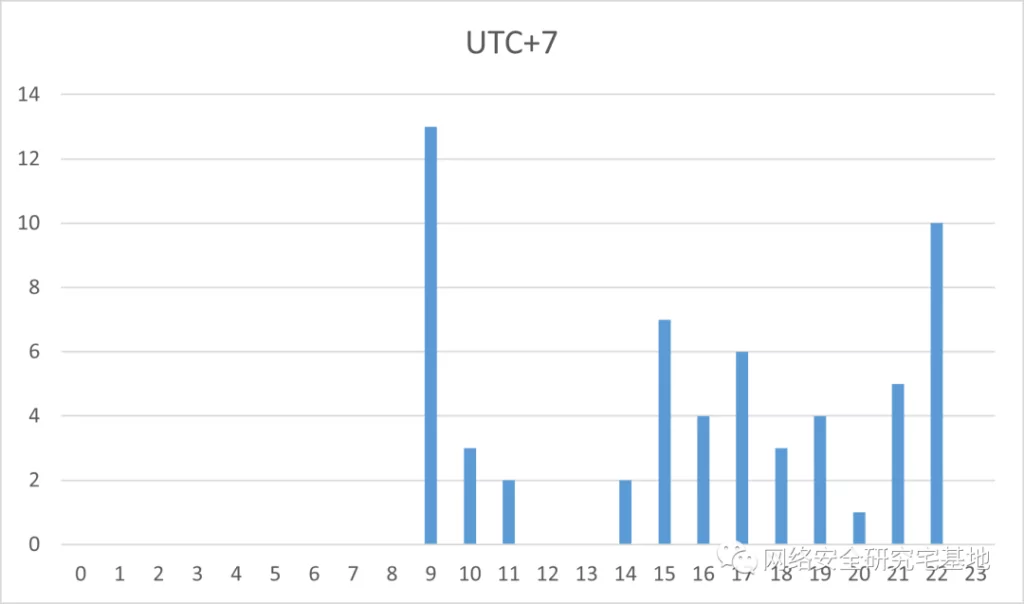
How does Dark Pink APT attack?
Dark Pink mainly uses the spear-phishing method as initial access and carries out its attack with an ISO file transmitted in its phishing attacks. This ISO file always contains the following files:
- A decoy document,
- A signed executable file,
- A malicious DLL file.
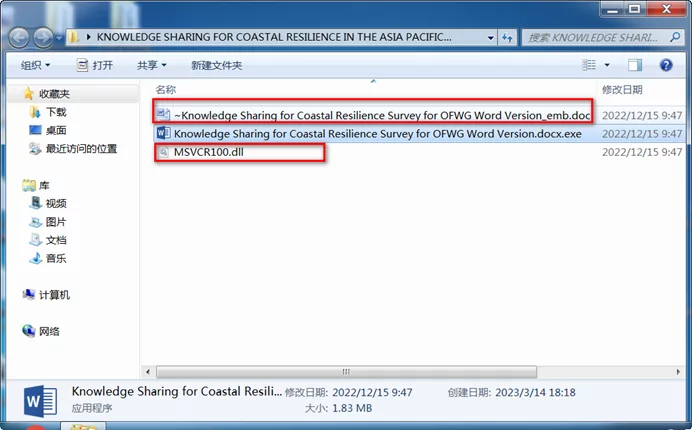
If we are going to list the way of attacks:
- Initial Access Vector: The primary method of intrusion used by Dark Pink is spear-phishing e-mails. These e-mails are carefully crafted to lure the recipient into clicking on malicious links or downloading infected attachments. Once the attackers gain access to a target’s network, they employ advanced persistence mechanisms to remain undetected and maintain control over the compromised system.

- Custom Malware Tools: Dark Pink employs a set of custom malware tools, notably TelePowerBot and KamiKakaBot. These tools are designed to exfiltrate sensitive data from compromised hosts. The latest versions of these tools have seen modifications to impede analysis and accommodate improvements.
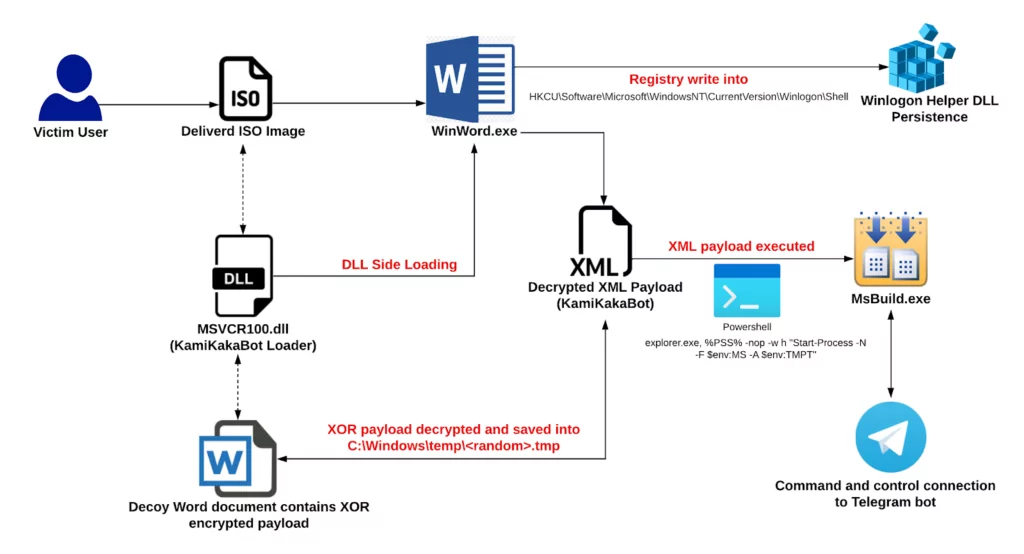
For instance, KamiKakaBot can execute commands from a threat actor-controlled Telegram channel via a Telegram bot. This bot’s functionality is split into two parts: one for controlling devices and another for harvesting valuable information.
- Use of Microsoft Office Vulnerability: Dark Pink has been observed to exploit CVE-2017-0199, the Microsoft Office Remote Code Execution Vulnerability, in most of its attacks and apparently continues to actively exploit this CVE.
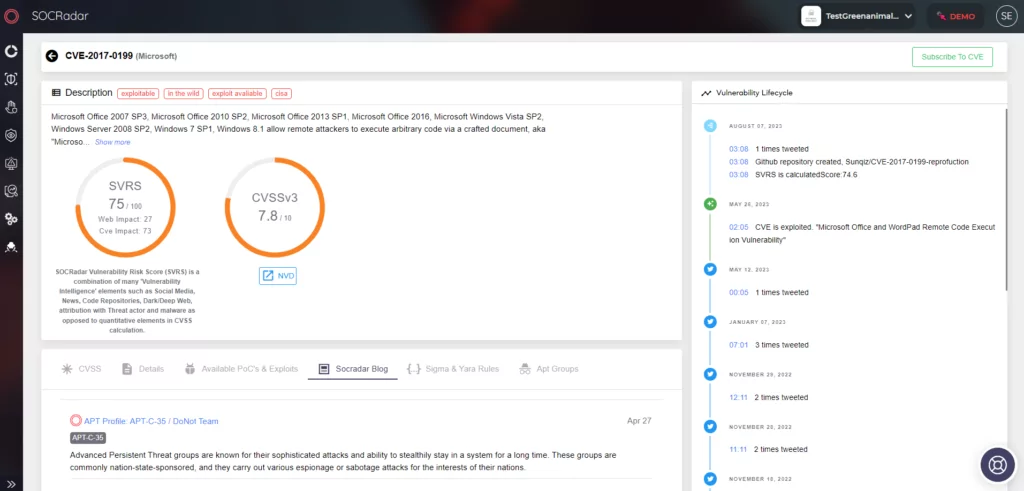
It is possible to say that this vulnerability is also actively exploited by the Indian state-sponsored APT group APT-C-35, which we have previously profiled, and they have common points in this aspect.
- Use of GitHub: The group has been associated with a GitHub account that hosts PowerShell scripts, ZIP archives, and custom malware. These modules are intended for subsequent installation onto victim machines.
Apart from the IoCs available in open source, our platform’s query revealed IoCs related to GitHub content used by Dark Pink and the content of the API utilized by TelePowerBot.
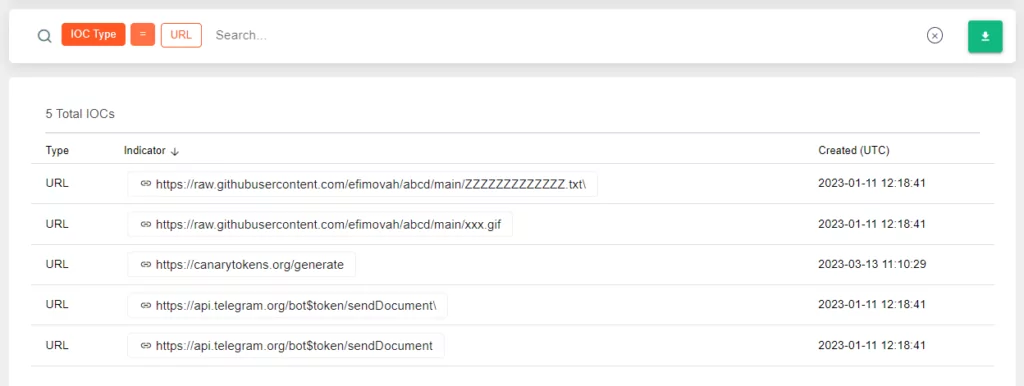
- Data Exfiltration: Apart from using Telegram for command-and-control, Dark Pink has been observed exfiltrating stolen data over HTTP using a service called webhook[.]site. They also utilize a Microsoft Excel add-in to ensure the persistence of TelePowerBot within the infected host.
- Stealth and Evasion: The group’s activities indicate a deliberate attempt to maintain a low profile. They carefully select their targets and limit the number of attacks to reduce the likelihood of exposure. Despite their stealthy approach, evidence suggests that they continuously update their tools to remain undetected and pose an ongoing risk to organizations.
What are the Targets of Dark Pink APT?
The Dark Pink APT Group, also known as Saaiwc Group, has been identified as a significant threat actor with a focus on high-value targets, including educational institutions, government agencies, military bodies, and non-profit organizations across various countries such as Belgium, Brunei, Indonesia, Thailand, and Vietnam.
If we detailed look at their targets:
- Geographical Reach: The group has successfully targeted 13 organizations across 9 countries. Their primary focus has been on countries like Indonesia, Brunei, and Vietnam. However, their reach extends beyond the Asia-Pacific region, with attacks also reported in Belgium and Thailand.
- Type of Organizations:
Looking at the organizations targeted by Dark Pink, it is observed that the majority are Governmental organizations and Military. Non-profit and Educational organizations follow these target organizations.
Conclusion
The Dark Pink APT Group has emerged as a formidable adversary in the cybersecurity landscape. Their operations, spanning across multiple countries and targeting a diverse range of organizations, underscore their capabilities and intentions. With a focus on high-profile targets, including government and military organizations, educational institutions, and other significant entities, Dark Pink has demonstrated a high degree of sophistication and adaptability in its attacks.
Their use of custom malware tools, spear-phishing emails, and advanced persistence mechanisms highlights their technical prowess. Moreover, their continuous evolution, as evidenced by the updates to their tools and techniques, indicates a proactive approach to staying ahead of cybersecurity defenses.
While the exact origins and motivations of the Dark Pink APT Group remain a subject of research and debate, their activities have undeniably left an indelible mark on the cybersecurity community. Their operations serve as a stark reminder of the ever-evolving threat landscape and the need for organizations to remain vigilant and proactive in their defense strategies.
Security recommendations against Dark Pink APT Group
The Dark Pink APT Group’s sophisticated tactics and techniques pose a significant threat to both private and public institutions, especially in the Asia-Pacific (APAC) region. To counteract the potential risks posed by this group, organizations should adopt the following security measures:
- Employee Training: One of the primary vectors of Dark Pink’s attacks is spear-phishing e-mails. Continuous employee training is essential to ensure that staff can recognize and report suspicious emails. By educating employees about the dangers of spear-phishing campaigns and teaching them how to identify malicious emails, organizations can significantly reduce the risk of a successful attack.
- Strengthen E-mail Security: Implement advanced e-mail security solutions and policies that can detect and stop threat actors before they penetrate network perimeters. This includes solutions that can identify malicious attachments, links, and unusual sender behavior. In this endeavor, SOCRadar Malware Analysis may help you to analyze EML files.
- Monitor for Suspicious Activity: Organizations should continuously monitor their networks for any signs of suspicious activity. This includes unusual data transfers, unauthorized access attempts, and changes to system configurations.
- Update and Patch Systems: Ensure that all systems, software, and applications are regularly updated and patched. Dark Pink is known to exploit vulnerabilities such as CVE-2017-0199, so keeping systems up-to-date can prevent potential breaches.
- Implement Advanced Detection Mechanisms: Use advanced threat detection mechanisms that can identify techniques like DLL side-loading and Event Triggered Execution. These mechanisms can help in the early detection and mitigation of threats.
- Limit Access: Implement the principle of least privilege (PoLP) across the organization. Ensure that employees have only the access they need to perform their job functions and nothing more.
- Stay Informed: Organizations should stay informed about the latest threats and tactics used by groups like Dark Pink. Subscribing to threat intelligence feeds and collaborating with cybersecurity firms can provide timely and relevant information.
- Incident Response Strategy: Ensure you have a clear and established plan for reacting to incidents to achieve a proactive security stance, and when a breach occurs, organized and rapid action may reduce harm and facilitate quicker recovery.
MITRE ATT&CK TTPs of Dark Pink APT
Technique | ID |
Initial Access | |
Phishing | T1566 |
Phishing: Spearphishing Attachment | T1566.001 |
Execution | |
User Execution | T1204 |
Command and Scripting Interpreter | T1059 |
Command and Scripting Interpreter: PowerShell | T1059.001 |
Windows Management Instrumentation | T1047 |
System Services | T1569 |
System Services: Service Execution | T1569.002 |
Persistence | |
Browser Extensions | T1176 |
Event Triggered Execution | T1546 |
Event Triggered Execution: Change Default File Association | T1546.001 |
Boot or Logon Autostart Execution | T1547 |
Scheduled Task/Job | T1053 |
Privilege Escalation | |
Abuse Elevation Control Mechanism | T1548 |
Abuse Elevation Control Mechanism: Bypass User Account Control | T1548.002 |
Defense Evasion | |
Masquerading | T1036 |
Masquerading: Match Legitimate Name or Location | T1036.005 |
Obfuscated Files or Information | T1027 |
Obfuscated Files or Information: Software Packing | T1027.002 |
Virtualization/Sandbox Evasion | T1497 |
Deobfuscate/Decode Files or Information | T1140 |
Trusted Developer Utilities Proxy Execution | T1127 |
Template Injection | T1221 |
Hijack Execution Flow | T1574 |
Hijack Execution Flow: DLL Side-Loading | T1574.002 |
Credential Access | |
Credentials from Password Stores | T1555 |
Discovery | |
Query Registry | T1012 |
File and Directory Discovery | T1083 |
System Information Discovery | T1082 |
Collection | |
Audio Capture | T1123 |
Screen Capture | T1113 |
Command and Control | |
Data Encoding | T1132 |
Web Service | T1102 |

Source: https://socradar.io/apt-profile-dark-pink-apt-group/
Views: 0