Short Summary:
APT42 is an Iranian state-sponsored cyber espionage group primarily focused on information collection and surveillance against individuals and organizations of strategic interest to Iran. Active since at least 2015, they employ targeted spear phishing and deploy mobile malware to gain access to sensitive information. Their operations are characterized by adaptability to Iran’s evolving priorities and a focus on entities opposing the Iranian government.
Key Points:
- Group Name: APT42 (also known as Mint Sandstorm, TA453, Yellow Garuda)
- Motivation: Espionage
- Targeted Countries: USA, Canada, UK, Germany, France, Middle East, Australia
- Active Since: At least 2015
- Techniques Used: Spear phishing, mobile malware deployment
- Recent Campaigns: Targeting organizations opposing Iran through social engineering and credential harvesting
- Notable Malware: NICECURL, TAMECAT
- Tools Used: CHAIRSMACK, GHAMBAR, POWERPOST, among others
- Recent Vulnerability Exploited: CVE-2023-38831
MITRE ATT&CK TTPs – created by AI
- Reconnaissance – T1595.002
- Gathering information about targets to plan attacks.
- Execution – T1047
- Using a command-line interface to execute commands.
- Defense Evasion – T1218.011
- Bypassing security mechanisms to avoid detection.
- Lateral Movement – T1021.001
- Moving through a network to access additional systems.
- Collection – T1589.001
- Gathering sensitive information from compromised systems.
- Credential Access – T1003.001
- Harvesting user credentials for unauthorized access.
- Command and Control – T1071.001
- Establishing a communication channel with compromised systems.
- Initial Access – T1098.002
- Gaining initial access to target systems.
- Privilege Escalation – T1065
- Gaining higher-level permissions on a system.
- Discovery – T1566.002
- Identifying system and network information.
APT42 is an Iranian state-sponsored cyber espionage group tasked with conducting information collection and surveillance operations against individuals and organizations of strategic interest to the Iranian government. We estimate with moderate confidence that APT42 operates on behalf of the Islamic Revolutionary Guard Corps (IRGC) Intelligence Organization (IRGC-IO) based on targeting patterns that align with the organization’s operational mandates and priorities.
Active since at least 2015, APT42 is characterized by highly targeted spear phishing and surveillance operations against individuals and organizations of strategic interest to Iran. The group’s operations, which are designed to build trust and rapport with their victims, have included accessing the personal and corporate email accounts of government officials, former Iranian policymakers or political figures, members of the Iranian diaspora and opposition groups, journalists, and academics who are involved in research on Iran. After gaining access, the group deployed mobile malware capable of tracking victim locations, recording phone conversations, accessing videos and images, and extracting entire SMS inboxes. APT42 has demonstrated the ability to alter its operational focus as Iran’s priorities evolve over time. We anticipate APT42 will continue to conduct cyber espionage operations in support of Iran’s strategic priorities in the long term based on its extensive operational history and imperviousness to public reporting and infrastructure takedowns.
Alias: APT42 Alias Mint Sandstorm, TA453, Yellow Garuda
Motivation: Espionage
Targeted Countries
USA, Canada, United Kingdom, Germany, France, Middle East, Australia

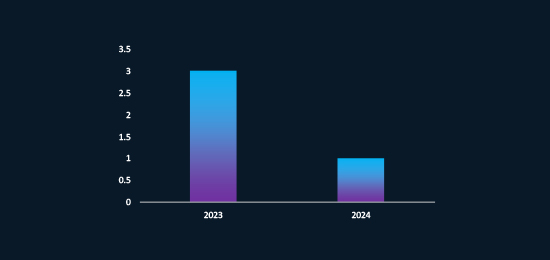
APT42 Campaigns Tracked by CYFIRMA
Malware used by APT 42
NICECURL,TAMECAT,NokNok
Tools used by APT42:
CHAIRSMACK, GHAMBAR, POWERPOST, BROKEYOLK, MAGICDROP, PINEFLOWER, TABBYCAT, TAMECAT, VBREVSHELL, VINETHORN, DOSTEALER
MITRE ATT&CK Techniques used by APT 42
| Reconnaissance | Execution | Defense Evasion | Lateral Movement |
| T1595.002 | T1047 | T1218.011 | T1021.001 |
| T1589.001 | T1053.005 | T1027 | |
| T1598.003 | T1059.003 | T1562.001 | Collection |
| T1589.002 | T1059.001 | T1036.005 | T1114 |
| T1589 | T1204.001 | T1112 | T1005 |
| Resource Development | T1204.002 | T1562 | T1113 |
| T1585.002 | T1059.005 | T1564.003 | T1114.002 |
| T1583.006 | T1070.004 | T1114.001 | |
| T1588.002 | Persistence | T1562.004 | T1560.001 |
| T1584.001 | T1505.003 | T1070.003 | T1056.001 |
| T1583.001 | T1053.005 | ||
| T1586.002 | T1136.001 | Credential Access | Command and Control |
| T1585.001 | T1547.001 | T1003.001 | T1071.001 |
| Initial Access | T1098.002 | T1056.001 | T1571 |
| T1566.003 | T1102.002 | ||
| T1189 | Privilege Escalation | Discovery | T1065 |
| T1566.002 | T1053.005 | T1016 | T1071 |
| T1190 | T1547.001 | T1049 | T1105 |
| T1057 | |||
| T1087.003 | |||
| T1033 | |||
| T1082 | |||
| T1083 |
Recently Exploited Vulnerabilities by APT 42 CVE-2023-38831
APT 42’s Recent Campaign Highlights and Trends
- In a recent campaign, threat actors from APT42 targeted organizations in Western and Middle Eastern countries through social engineering attacks. They impersonated journalists to gain the trust of their targets and infiltrated corporate networks and cloud environments. The attackers used malicious emails to deliver two custom backdoors, named Nicecurl and Tamecat, which allowed them to execute commands and steal sensitive data from the compromised systems.
- In recent campaigns, APT42 has predominantly focused on targeting entities that oppose Iran, including government and political bodies, media and journalism outlets, healthcare organizations, academic institutions, and non-governmental organizations (NGOs).
- APT42’s activities are not limited to direct cyber-attacks. The group also conducts extensive credential harvesting operations, intricately designed to appear as legitimate interactions. These operations are carried out through carefully crafted spear-phishing campaigns that often impersonate well-known news outlets or NGOs. For example, domains masquerading as major publications like The Washington Post and The Economist have been used to disseminate malicious links that redirect users to fake login pages, effectively stealing their credentials.
- Given APT42’s historical resilience and adaptability, it is expected that they will continue their cyber espionage operations in support of Iran’s strategic objectives, particularly as geopolitical dynamics evolve.
Source: Original Post