CVE-2025-24813 is a critical vulnerability in Apache Tomcat that can allow remote, unauthenticated attackers to execute arbitrary code or access sensitive files. Organizations using vulnerable versions need to apply patches to protect their systems. Affected: Apache Tomcat
Keypoints :
- Critical path equivalence vulnerability in Apache Tomcat, identified as CVE-2025-24813.
- Allows attackers to execute arbitrary code on vulnerable servers without authentication.
- Affected Tomcat versions include 11.0.0-M1 to 11.0.2, 10.1.0-M1 to 10.1.34, 9.0.0-M1 to 9.0.98, and some 8.5.x versions.
- Exploitation involves sending a Base64-encoded serialized Java payload to the server.
- Conditions for successful exploitation include default servlet write permissions, partial PUT support, and specific libraries in use.
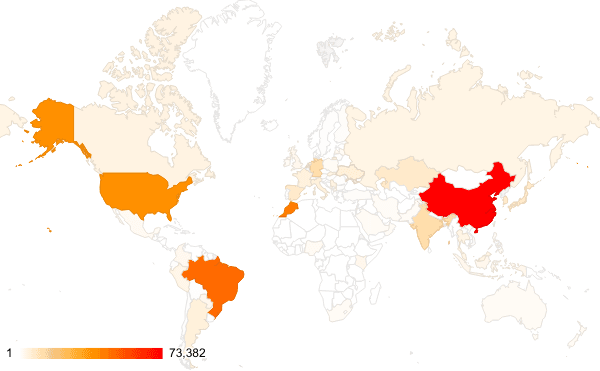
- Cybersecurity firm Greynoise has identified six malicious IP addresses targeting affected systems.
- Multiple proof-of-concept exploits have been released, increasing exploitation risk.
- Recommended actions include upgrading to safe versions or implementing access controls if upgrading isn’t feasible.
MITRE Techniques :
- TA0002 – Execution: Remote attackers send a PUT request containing a malicious payload to execute arbitrary code.
- TA0007 – Discovery: Attackers can view security-sensitive files and inject content into them by exploiting server vulnerabilities.
Indicator of Compromise :
- [URL] http://example.com/path/to/unexpected.jsp
- [URL] http://example.com/path/to/suspicious.jsp
- [JSP File] Presence of unexpected JSP files in the web server root directory
- [Request] External POST or GET requests targeting suspicious JSP files
- [Request] Occurrence of unexpected PUT requests in web server logs
Full Story: https://www.recordedfuture.com/blog/apache-tomcat-cve-2025-24813-vulnerability-analysis