On February 2, 2024, AnyDesk, a popular remote desktop software provider, announced that it had fallen victim to a cyberattack that compromised its production systems. The breach, orchestrated by malicious actors, has far-reaching implications for AnyDesk customers.
The incident came to light when AnyDesk released a public statement about possible security breaches on some of its systems. Subsequently, the company conducted a thorough security audit, confirming that its production systems had been compromised. The consequences of this breach are alarming, as it exposed sensitive customer data to cybercriminals.
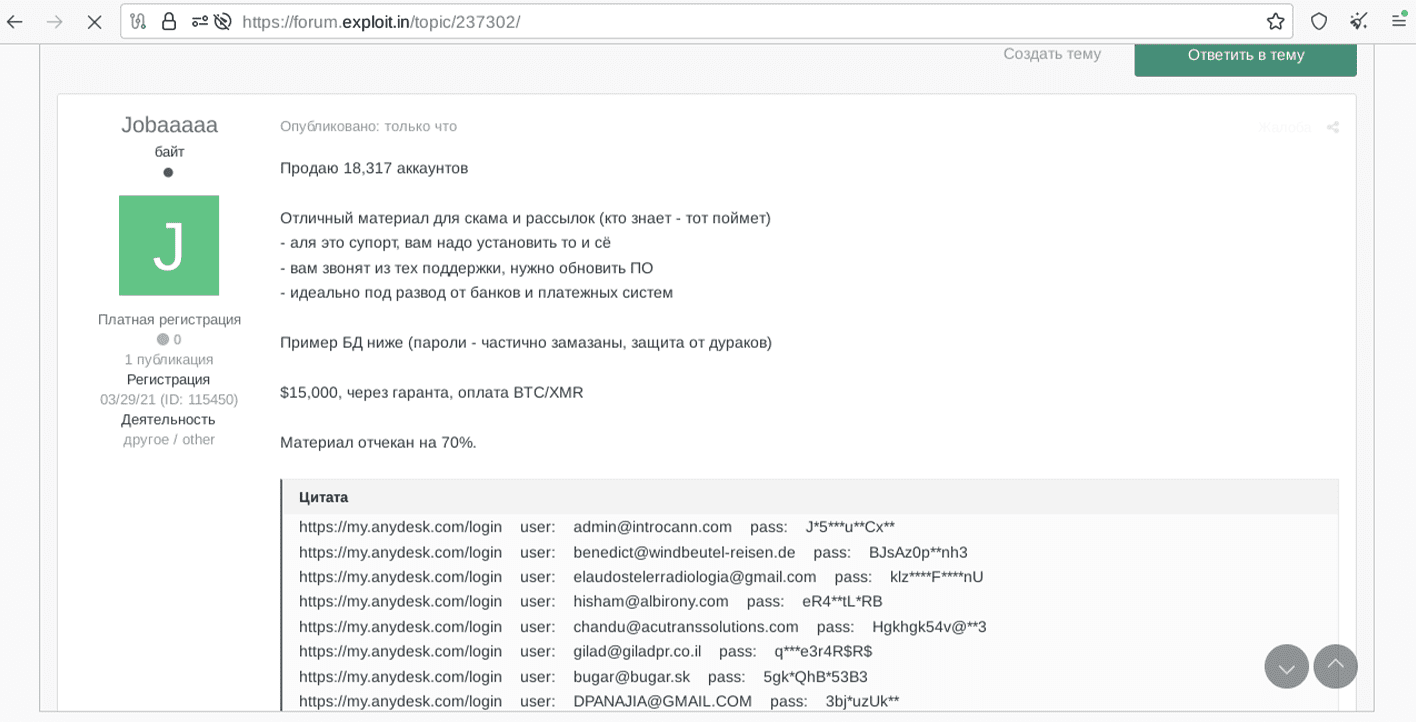
On February 3, 2024, cybersecurity firm Resecurity identified two threat actors involved in the breach, one of them operating under the alias “Jobaaaaa.” This actor, whose registration date traces back to 2021, was offering a substantial number of AnyDesk customer credentials for sale on the Dark Web marketplace Exploit[.]in. Resecurity’s HUNTER team engaged with the actor, collecting information to share with the wider community and mitigate the risk.
The compromised data included access credentials belonging to both individual consumers and enterprises, potentially unlocking the AnyDesk customer portal. The actor attempted to sanitize some of the passwords to evade detection. Shockingly, 18,317 accounts were up for sale at $15,000, payable in cryptocurrency. The actor even agreed to conduct the transaction via an escrow service on an underground forum.
The ramifications of this breach are profound. Cybercriminals who gained access to the AnyDesk portal could glean valuable information about customers, including license keys, active connections, session durations, contact information, email addresses, and the number of managed remote access hosts, all with their online/offline status and IDs. Such details open up a plethora of malicious possibilities.
Furthermore, the timestamps on the shared screenshots indicated successful unauthorized access even after the breach was disclosed, suggesting that not all customers had changed their credentials. This presents a complex challenge for proper remediation, as cybercriminals could continue to exploit this vulnerability.
The absence of two-factor authentication (2FA) on the majority of exposed accounts adds to the danger. This breach could catalyze new attacks, including targeted phishing campaigns that leverage the acquired information to gain the trust of potential victims.
The breach exposed the data of AnyDesk customers and revealed the potential victims’ diverse nature, as some of the screenshots contained localization in foreign languages.
AnyDesk’s response to the breach included notifying customers about planned maintenance and temporarily disabling login functionality as a security measure. The login functionality was restored by February 1, 2024, regarding Single Sign-On (SSO) and Identity Provider (IDP) mechanisms. However, the company faces the challenge of addressing the aftermath of the breach, especially with the risk of cybercriminals rushing to monetize the stolen customer credentials.
Interestingly, the AnyDesk breach follows recent incidents involving prominent entities such as Cloudflare, Microsoft, and Hewlett Packard Enterprise, allegedly orchestrated by a nation-state attacker known as Midnight Blizzard/Nobelium. Resecurity’s observations suggest that the line between cybercrime and nation-state activity can blur, as cybercriminal actors operating on the Dark Web may conduct campaigns resembling those of nation-state actors.
In light of this breach, AnyDesk customers must take proactive steps to protect their accounts and data. Password changes alone are insufficient. AnyDesk offers a whitelist feature, enabling users to specify who can connect to their devices, adding an extra layer of security.
Multi-factor authentication (MFA) is strongly recommended to enhance account protection. Organizations should also monitor for any unexpected password and MFA changes, suspicious sessions, and emails referencing AnyDesk accounts from unknown sources.
Source: Original Post