Authored by Yukihiro Okutomi
McAfee’s Mobile team observed a smishing campaign against Japanese Android users posing as a power and water infrastructure company in early June 2023. This campaign ran for a short time from June 7. The SMS message alerts about payment problems to lure victims to a phishing website to infect the target devices with a remote-controlled SpyNote malware. In the past, cybercriminals have often targeted financial institutions. However, on this occasion, public utilities were the target to generate a sense of urgency and push victims to act immediately. Protect your Android and iOS mobile devices with McAfee Mobile Security.
Smishing Attack Campaign
A phishing SMS message impersonating a power or water supplier claims a payment problem, as shown in the screenshot below. The URL in the message directs the victim to a phishing website to download mobile malware.
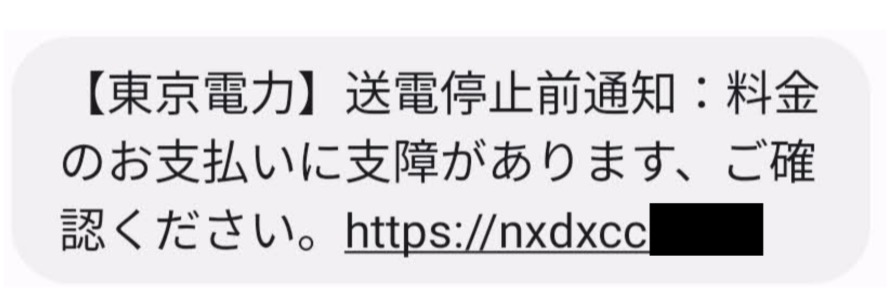
Notice of suspension of power transmission because of non-payment of charges from a power company in Tokyo (Source: Twitter)
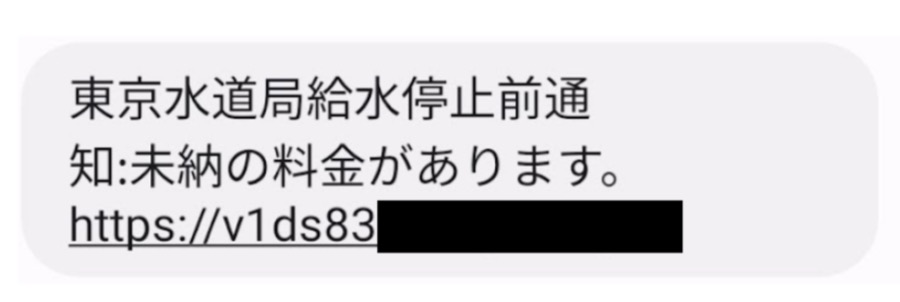
Notice of suspension of water supply because of non-payment of charges from a water company in Tokyo (Source: Twitter)
When accessed with a mobile browser, it will start downloading malware and display a malware installation confirmation dialog.
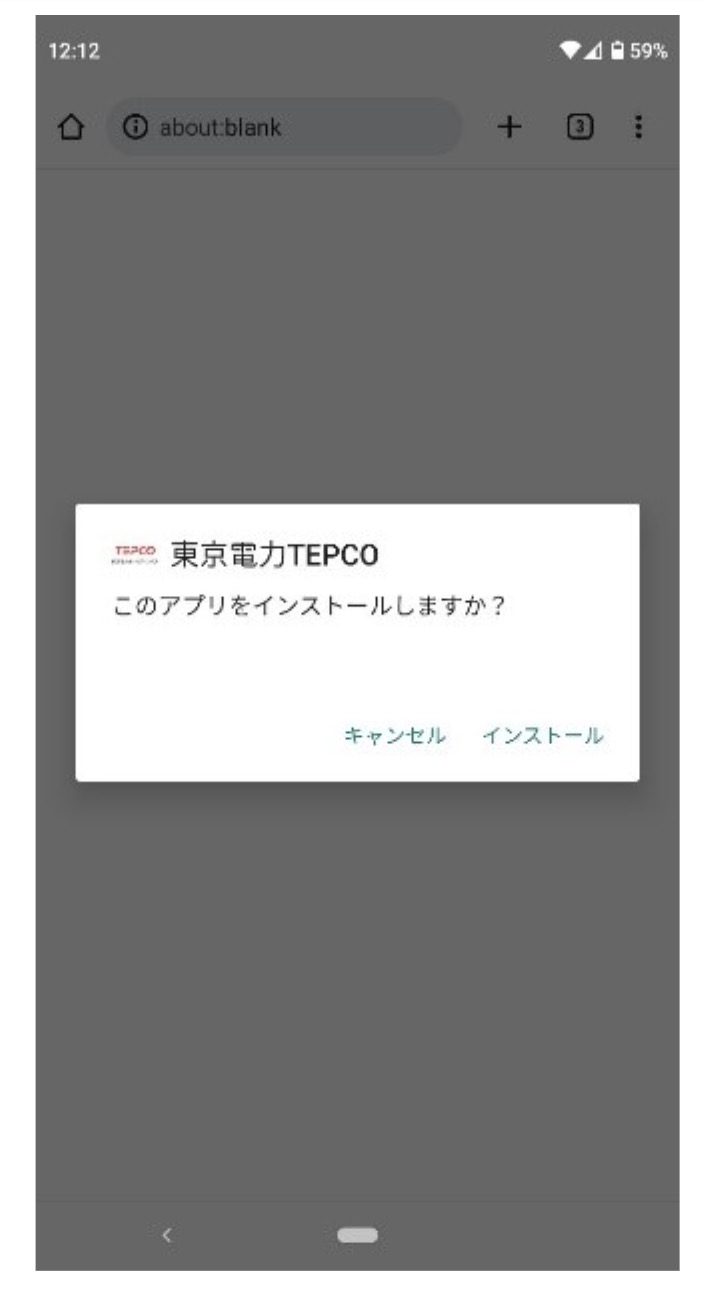
The confirmation dialog of Spyware installation via browser (Source: Twitter)
SpyNote malware
SpyNote is a known family of malware that proliferated after its source code was leaked in October 2022. Recently, the malware was used in a campaign targeting financial institutions in January and targeting Bank of Japan in April 2023.
The SpyNote malware is remotely controlled spyware that exploits accessibility services and device administrator privileges. It steals device information and sensitive user information such as device location, contacts, incoming and outgoing SMS messages, and phone calls. The malware deceives users by using legitimate app icons to look real.

Application Icons disguised by malware.
After launching the malware, the app opens a fake settings screen and prompts the user to enable the Accessibility feature. When the user clicks the arrow at the bottom of the screen, the system Accessibility service settings screen is displayed.
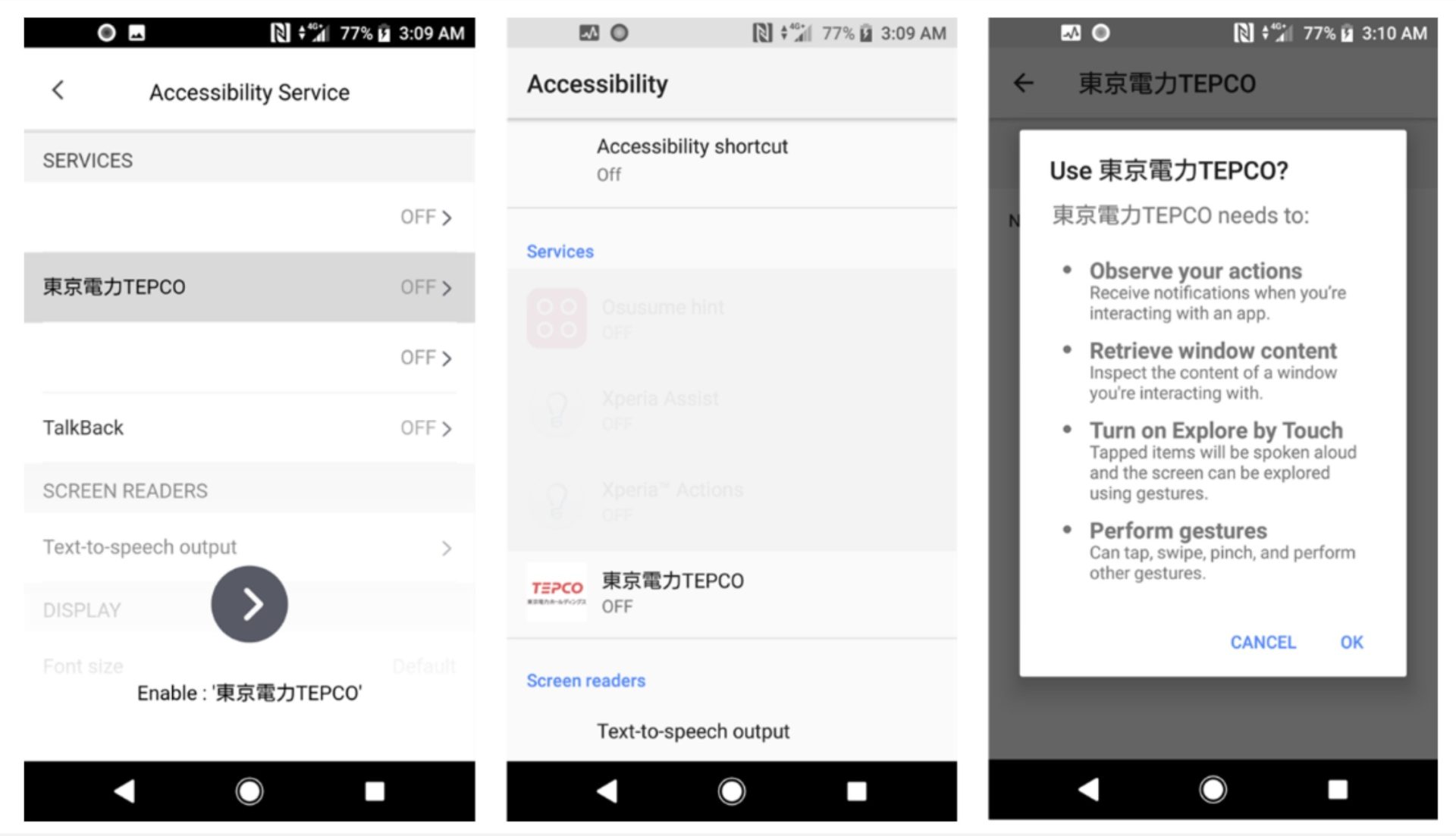
A fake setting screen (left), system setting screen (center and right)
By allowing the Accessibility service, the malware disables battery optimization so that it can run in the background and automatically grants unknown source installation permission to install another malware without the user’s knowledge. In addition to spying on the victim’s device, it also steals two-factor authentication on Google Authenticator and Gmail and Facebook information from the infected device.
Although the distribution method is different, the step of requesting Accessibility service after launching the app is similar to the case of the Bank of Japan that occurred in April.
Scammers keep up with current events and attempt to impersonate well-known companies that have a reason to reach out to their customers. The mobile malware attack using SpyNote discovered this time targets mobile apps for life infrastructure such as electricity and water. One of the reasons for this is that electric bills and water bills, which used to be issued on paper, are now managed on the web and mobile app. If you want to learn about smishing, consult this article “What Is Smishing? Here’s How to Spot Fake Texts and Keep Your Info Safe”. McAfee Mobile Security detects this threat as Android/SpyNote and alerts mobile users if it is present and further protects them from any data loss. For more information, visit McAfee Mobile Security.
Indicators of compromise (IoC)
C2 Server:
- 104.233.210.35:27772
Malware Samples:
| SHA256 Hash | Package name | Application name |
| 075909870a3d16a194e084fbe7a98d2da07c8317fcbfe1f25e5478e585be1954 | com.faceai.boot | キャリア安全設定 |
| e2c7d2acb56be38c19980e6e2c91b00a958c93adb37cb19d65400d9912e6333f | com.faceai.boot | 東京電力 |
| a532c43202c98f6b37489fb019ebe166ad5f32de5e9b395b3fc41404bf60d734 | com.faceai.boot | 東京電力TEPCO |
| cb9e6522755fbf618c57ebb11d88160fb5aeb9ae96c846ed10d6213cdd8a4f5d | com.faceai.boot | 東京電力TEPCO |
| 59cdbe8e4d265d7e3f4deec3cf69039143b27c1b594dbe3f0473a1b7f7ade9a6 | com.faceai.boot | 東京電力TEPCO |
| 8d6e1f448ae3e00c06983471ee26e16f6ab357ee6467b7dce2454fb0814a34d2 | com.faceai.boot | 東京電力TEPCO |
| 5bdbd8895b9adf39aa8bead0e3587cc786e375ecd2e1519ad5291147a8ca00b6 | com.faceai.boot | 東京電力TEPCO |
| a6f9fa36701be31597ad10e1cec51ebf855644b090ed42ed57316c2f0b57ea3c | com.faceai.boot | 東京電力TEPCO |
| f6e2addd189bb534863afeb0d06bcda01d0174f5eac6ee4deeb3d85f35449422 | com.faceai.boot | 東京電力TEPCO |
| 755585571f47cd71df72af0fad880db5a4d443dacd5ace9cc6ed7a931cb9c21d | com.faceai.boot | 東京電力TEPCO |
| 2352887e3fc1e9070850115243fad85c6f1b367d9e645ad8fc7ba28192d6fb85 | com.faceai.boot | 東京電力TEPCO |
| 90edb28b349db35d32c0190433d3b82949b45e0b1d7f7288c08e56ede81615ba | com.faceai.boot | 東京電力TEPCO |
| 513dbe3ff2b4e8caf3a8040f3412620a3627c74a7a79cce7d9fab5e3d08b447b | com.faceai.boot | 東京電力TEPCO |
| f6e2addd189bb534863afeb0d06bcda01d0174f5eac6ee4deeb3d85f35449422 | com.faceai.boot | 東京電力TEPCO |
| 0fd87da37712e31d39781456c9c1fef48566eee3f616fbcb57a81deb5c66cbc1 | com.faceai.boom | 東京水道局アプリ |
| acd36f7e896e3e3806114d397240bd7431fcef9d7f0b268a4e889161e51d802b | com.faceai.boom | 東京水道局アプリ |
| 91e2f316871704ad7ef1ec74c84e3e4e41f557269453351771223496d5de594e | com.faceai.boom | 東京水道局アプリ |
Source: Original Post
“An interesting youtube video that may be related to the article above”
Views: 0
