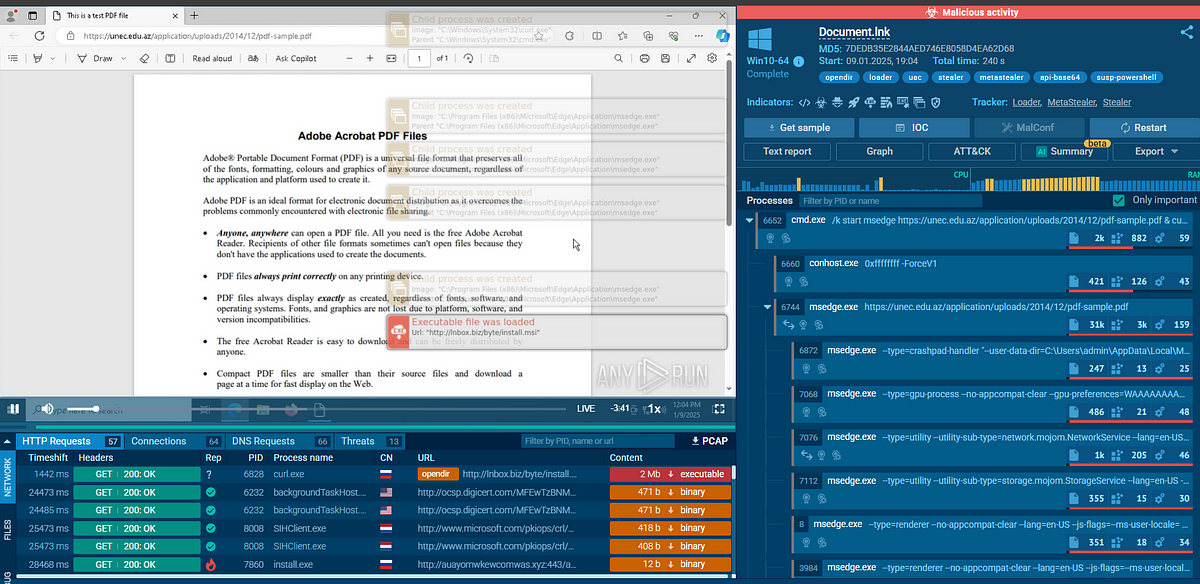
Recent investigations highlight the misuse of legitimate hosting platforms like Namecheap for cybercrime activities, specifically involving a malware loader called MetaStealer. The incident showcases how threat actors exploit services like WebDav Opendir to conduct malicious operations. Affected: Namecheap, WebDav Opendir
Keypoints :
- Malicious activities leveraging WebDav Opendir hosted on Namecheap.
- MetaStealer identified as the associated malware.
- Malware delivered via a Windows shortcut file (Document.lnk).
- AnyRun analysis provided insights into malware behavior and evasion tactics.
- Observed commands executed by the malware involved downloading and executing a malicious MSI installer.
- Technical recommendations include updating security solutions and user awareness training.
MITRE Techniques :
- T1059: Command and Scripting Interpreter – The malware uses PowerShell commands to fetch payloads and disable antivirus protections.
- T1548: Abuse Elevation Control Mechanism – Bypasses User Account Control (UAC) using ComputerDefaults.exe.
- T1562: Impair Defenses – Modifies Windows Defender settings to evade detection.
- T1555: Unsecured Credentials – Steals sensitive user data and credentials.
Indicator of Compromise :
- [url] http://lnbox.biz:8080
- [ip address] 193.233.72.52
- [url] https://auayomwkewcomwas.xyz
- [file name] Document.lnk
- [file hash] MD5: 7DEDB35E2844AED746E8058D4EA62D68
- Check the article for all found IoCs.
Full Research: https://medium.com/@harboot/analysis-of-malicious-webdav-activity-on-namecheap-f8be3eb806ab?source=rss——malware-5
Views: 1