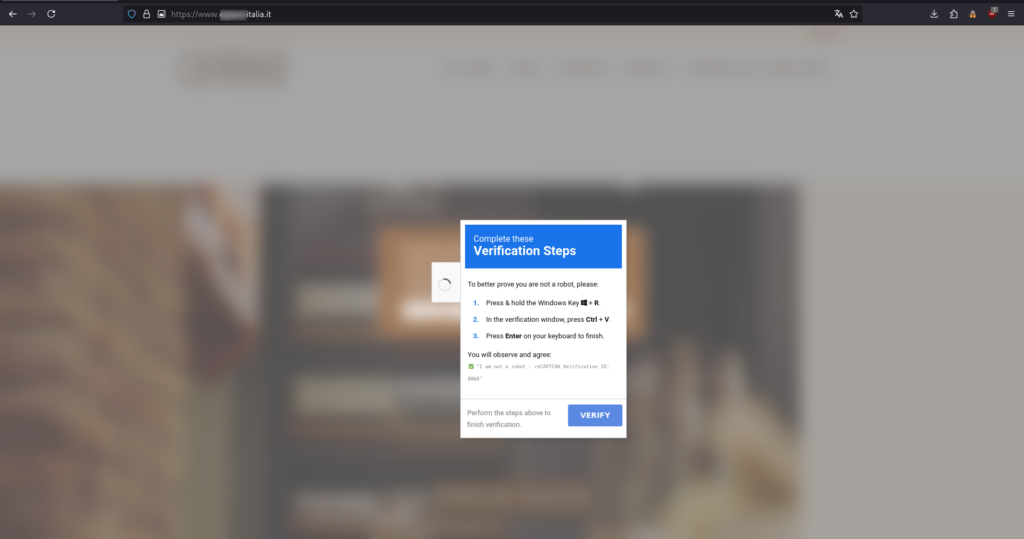
Lumma Stealer has adopted a new tactic involving fake CAPTCHA prompts to deceive victims into executing malicious scripts. This method exploits user trust in CAPTCHA as legitimate security checks. A recent campaign observed by CERT-AGID involved victims being alerted to a supposed GitHub security vulnerability, leading them to execute a PowerShell script that infects their systems with Lumma Stealer. Affected: GitHub, Windows
Keypoints :
- Lumma Stealer uses fake CAPTCHA to trick users into running harmful scripts.
- This tactic takes advantage of user trust in CAPTCHA as a security measure.
- A campaign in October 2024 involved fake alerts about GitHub vulnerabilities.
- Victims were directed to execute a PowerShell script via a fake CAPTCHA.
- A compromised Italian domain was found distributing Lumma Stealer through an outdated WordPress CMS.
- JavaScript code was used to generate fake CAPTCHA for Windows users.
- The PowerShell script downloads and executes a malicious file.
- The XOR key for decoding the malware was derived from a lengthy code.
- Lumma Stealer uses Steam Community profiles for command and control (C2) operations.
- Authorities were informed about the compromised site, and IoCs were shared.
MITRE Techniques :
- Execution (T1203) – Users are tricked into executing PowerShell scripts via fake CAPTCHA prompts.
- Command and Control (T1071) – Lumma Stealer uses Steam Community profiles for C2 communication.
- Obfuscated Files or Information (T1027) – The malware uses Base64 encoding and XOR operations to obfuscate its payload.
Indicator of Compromise :
- [domain] compromised-italian-domain[.]com
- [file name] xorkey.txt
- [tool name] Lumma Stealer
- [url] suspicious-link[.]com
- [others ioc] PowerShell script
- Check the article for all found IoCs.
Full Research: https://cert-agid.gov.it/news/analisi-di-una-campagna-lumma-stealer-con-falso-captcha-condotta-attraverso-domino-italiano-compromesso/