Trend Research has identified new versions of the Albabat ransomware targeting Windows, Linux, and macOS platforms. The group is utilizing GitHub to facilitate their ransomware operations. Organizations are advised to enhance security protocols and implement preventive measures to mitigate potential ransomware attacks. Affected: Windows, Linux, macOS
Keypoints :
- New versions of Albabat ransomware have been discovered, indicating a potential expansion of targets.
- Versions 2.0.0 and 2.5 have been identified, targeting Windows, Linux, and macOS.
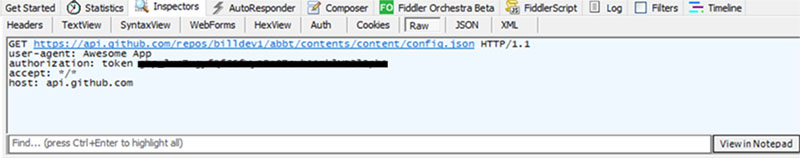
- The ransomware uses GitHub’s REST API for configuration data delivery.
- It encrypts a wide array of file extensions and skips many specific folders and files during encryption.
- Malware operators utilize a PostgreSQL database for tracking infections and ransom payments.
- The GitHub repository used by the ransomware is privately accessible with an authentication token.
- Security measures such as regular backups and network segmentation are recommended to combat the threat.
- Trend Vision One™ offers AI-powered protection against ransomware and provides customers with threat intelligence and insights.
MITRE Techniques :
- T1497 – Virtualization/Sandbox Evasion: The Albabat ransomware targets virtualization platforms by killing specific processes like virtualbox.exe.
- T1071.001 – Application Layer Protocol: GitHub is exploited for command and control communication to retrieve configuration files.
- T1046 – Network Service Discovery: The ransomware gathers system information on various operating systems to identify potential targets.
- T1486 – Data Encrypted for Impact: Targets critical file extensions for encryption, impacting data accessibility.
- T1112 – Modify Registry: It modifies system settings and configurations related to its operation.
Indicator of Compromise :
- [SHA1] 1cc2d1f2a991c19b7e633a92b1629641c019cdeb
- [SHA1] c7c52fdaecf325dfaf6eda14e0603579feaed40a
- [SHA1] 8a3ea65147a156d381d8f1773e91eb8e0f6b1e40
- [SHA1] 8de54cad9d6316679580c91117b484acb493ab72
- [SHA1] d67dc8c4232a3943a66608d62874923e9a3fb628
Full Story: https://www.trendmicro.com/en_us/research/25/c/albabat-ransomware-group.html