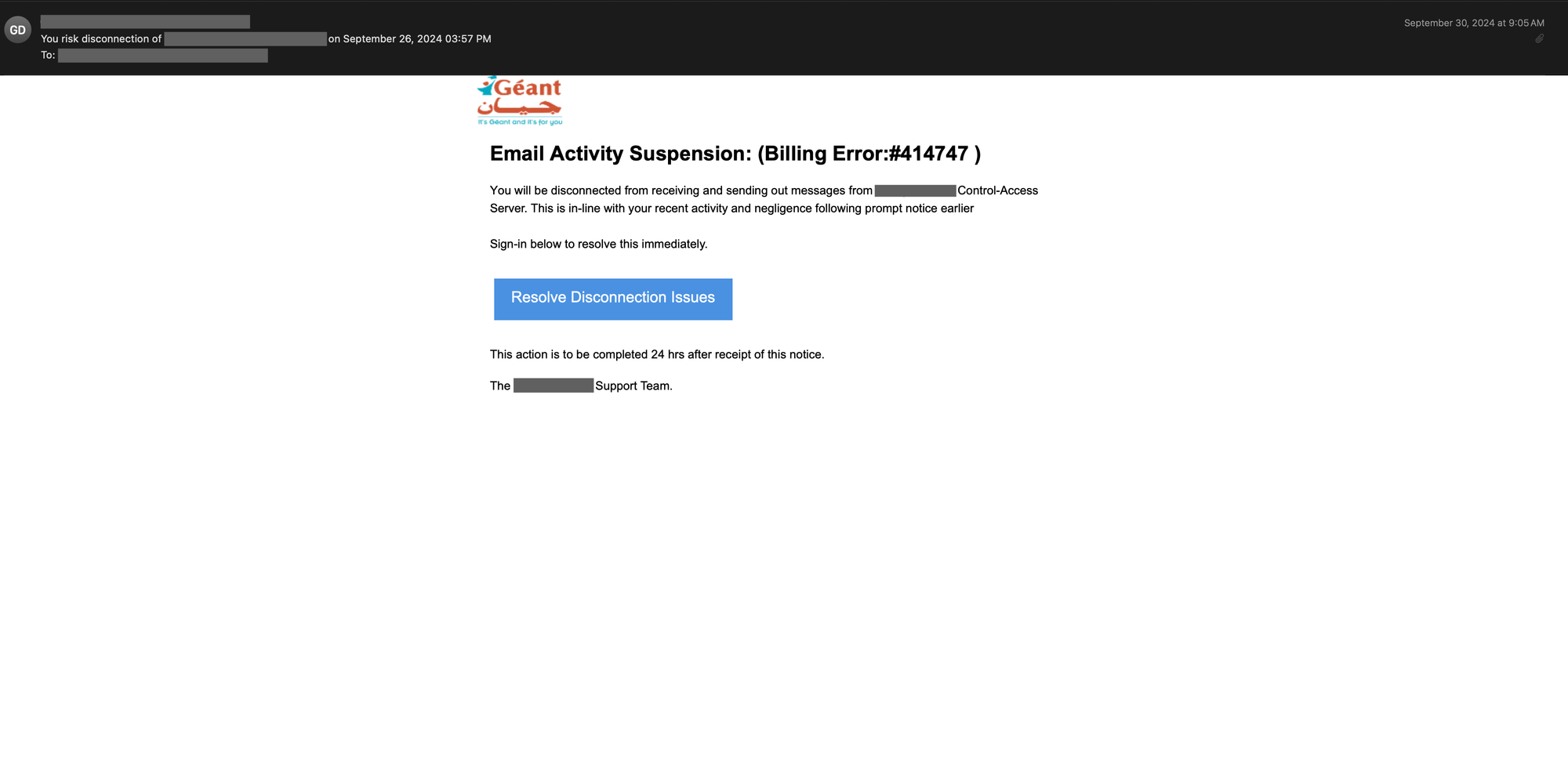
Cisco Talos has identified the misuse of Cascading Style Sheets (CSS) by threat actors to evade spam filters and track user actions and preferences, posing security and privacy risks. The blog discusses various methods of CSS abuse, including hidden text and tracking capabilities that exploit the functionality of CSS in emails. Affected: Users, Email Clients, Organizations
Keypoints :
- Threat actors use CSS to evade spam filters and detection systems.
- CSS is abused for tracking user actions and preferences, impacting privacy.
- Hidden text salting is a notable technique used by attackers in phishing emails.
- CSS properties can conceal content, making it invisible in email clients.
- Tracking capabilities include monitoring when emails are opened and printed.
- CSS can be leveraged to fingerprint users’ hardware and software configurations.
- Mitigation strategies include advanced filtering mechanisms and email privacy proxies.
MITRE Techniques :
- Technique: Phishing (T1566) – Threat actors have employed phishing emails containing hidden text to deceive recipients.
- Technique: User Tracking (T1071) – CSS properties are used to track user actions like email opens and prints.
- Technique: Exploit Public-Facing Application (T1190) – Attackers leverage CSS for tracking and fingerprinting through URLs assigned to certain CSS properties.
Indicator of Compromise :
- [Email Address] attacker@example.com
- [URL] http://malicious.com/path
- [Domain] example.com
- [IP Address] 192.168.1.1
- [Hash] c4ca4238a0b923820dcc509a6f75849b15
Full Story: https://blog.talosintelligence.com/css-abuse-for-evasion-and-tracking/