Introduction
On October 11, 2023, the Cybersecurity and Infrastructure Security Agency (CISA) published an advisory for AvosLocker, which was a sophisticated double extortion Ransomware-as-a-Service (RaaS) group that was last observed being active in May 2023. Our research team put this report together so the security community can learn how to counteract other threats that employ similar tactics and procedures (TTPs).
The AvosLocker group gained prominence in July 2021 and was known for employing a double extortion strategy where they first stole data before encrypting it. The group would then threaten to release the data on a dedicated leak site unless a ransom was paid. Initially, AvosLocker primarily targeted Windows systems, but they subsequently expanded their reach by creating a Linux version of their ransomware designed to target VMware ESXi.
Key Takeaways
- AvosLocker was a Ransomware-as-a-Service double extortion group.
- No new activity has been observed since May 2023.
- AvosLocker hosted a data leak site from July 2021 to July 2023, where they would add stolen proprietary data unless a ransom was paid.
- AvosLocker heavily targeted the education sector – accounting for 25% of their attacks.
- The United States bore the brunt of most AvosLocker attacks accounting for a whopping 72.2%, with Canada trailing far behind at 9.3%.
Attack Methodologies
Since different affiliates employed distinct intrusion techniques, each threat actor’s deploying AvosLocker approach to gain unauthorized access varied significantly. Affiliates were observed exploiting ProxyShell vulnerabilities, like CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207, present in the Microsoft Exchange server to obtain initial access. AvosLocker affiliates also infiltrated victims’ networks via compromised RDP and VPN accounts, and exploited the Zoho ManageEngine ServiceDesk Plus vulnerability.
After infiltrating a victim’s network, the ransomware was executed in Windows Safe Mode to maximize the number of files that could be encrypted, since applications such as databases and security software (e.g., antivirus programs) would likely not be running. This technique ensured that these applications would not interfere with file encryption. The ability to encrypt files in Windows Safe Mode is a feature that has been observed in other ransomware families, including Conti, REvil, and BlackMatter.
Infections by Industry
Figure 1, shown below, depicts the industries most affected by AvosLocker as a percentage of total attacks over the past year.
- AvosLocker focused its attacks on the education sector and received approximately 25% of the group’s total attacks.
- Furthermore, AvosLocker impacted the manufacturing and healthcare industry, which accounted for approximately 15.38% and 9.62%, respectively.
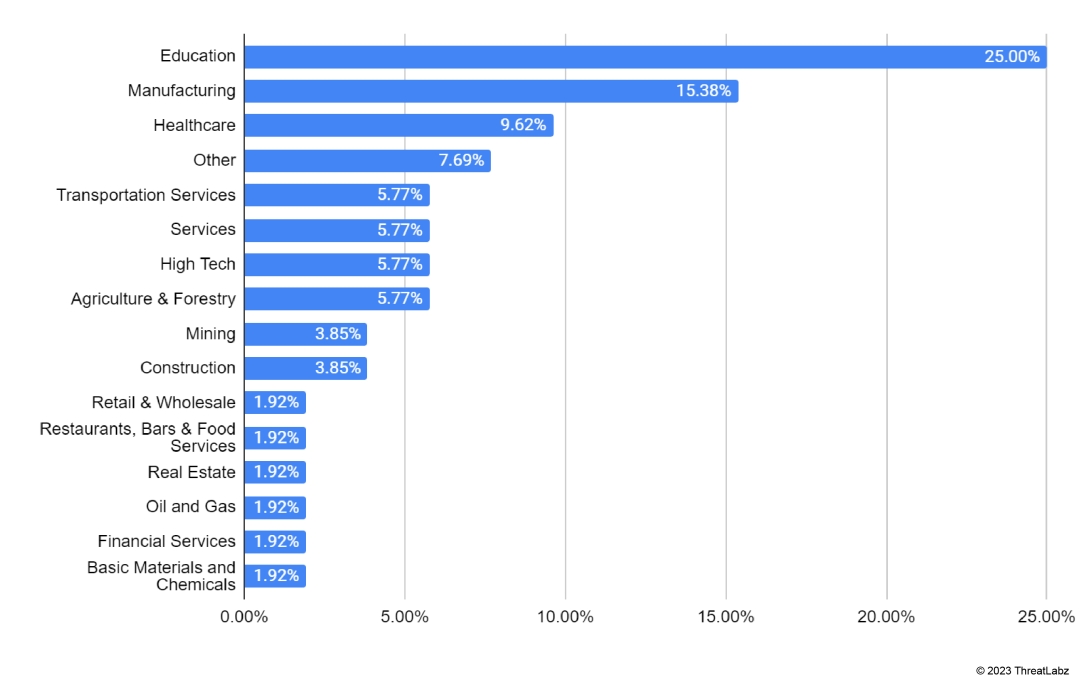
Figure 1: Industry verticals targeted by double extortion attacks using AvosLocker
Countries Targeted by AvosLocker
The U.S. emerged as the hardest-hit country in attacks orchestrated by the AvosLocker group, with more than 72% of attacks as shown in Figure 2. This highlights the scale and severity of the cyberthreat faced by U.S. businesses and institutions. Canadian organizations received 9.3% of AvosLocker’s attacks. China and Taiwan shared a similar level of impact, each experiencing 3.7% of AvosLocker attacks.
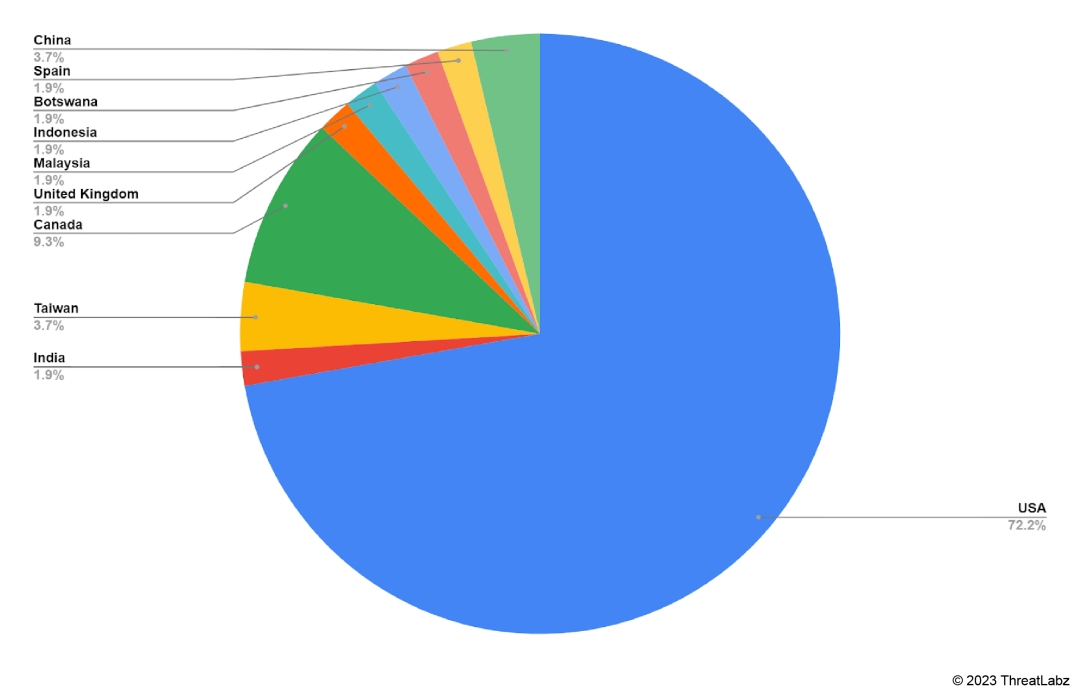
Figure 2: Breakdown of victims by country breached by AvosLocker
Ransomware Analysis
Since first discovered in 2021, AvosLocker binaries have undergone slight changes and improvements. The following is a detailed analysis of the last variant used in-the-wild.
Command line arguments
AvosLocker implements multiple command line arguments, as shown in Figure 3, allowing for customization of the ransomware execution based on affiliate requirements.
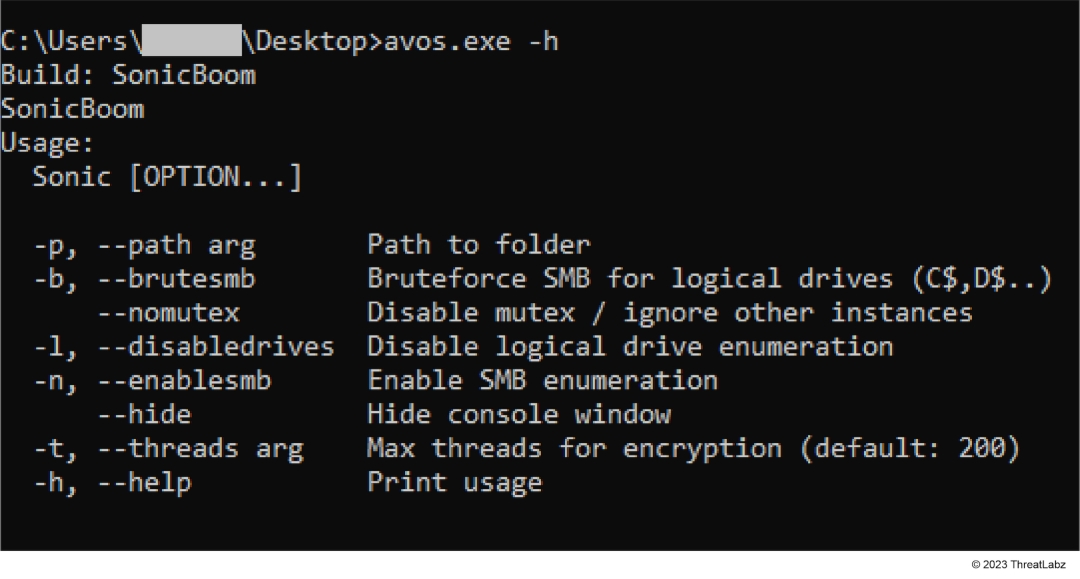
Figure 3: AvosLocker command line arguments
The threat actor decides what functionality to enable/disable during the execution of the AvosLocker ransomware. When executed, the selected options are displayed in the console as shown below.
Build: SonicBoom
b_bruteforce_smb_enable: 0
b_logical_disable: 0
b_network_disable: 1
b_mutex_disable: 0
concurrent_threads_num_max: 200AvosLocker creates the mutex Zheic0WaWie6zeiy by default to ensure that only one ransomware process is running at a given time, unless the –nomutex command line argument is provided.
Pre-encryption measures
Upon execution, AvosLocker first checks whether it has administrative privileges, and if not, it shows the debug message in the console, The token does not have the specified privilege, and then executes a process termination routine targeting databases, web browsers, and other business applications. The list of processes to be terminated were decoded dynamically using a stack-based string obfuscation algorithm (described later in the report). The process names in Table 1 were terminated.
| encsvc | thebat | mydesktopqos | xfssvccon | firefox | infopath |
| winword | steam | synctime | notepad | ocomm | onenote |
| mspub | thunderbird | agntsvc | mydesktopservice | excel | powerpnt |
| outlook | wordpad | dbeng50 | isqlplussvc | sqbcoreservice | oracle |
| ocautoupds | dbsnmp | msaccess | tbirdconfig | ocssd | sql & visio |
Then, AvosLocker performs the following actions:
- Deletes Windows shadow copies to prevent the recovery of files using the following commands:
wmic shadowcopy delete /nointeractive vssadmin.exe Delete Shadows /All /Quiet
- Disables recovery mode and the edits the boot status policy, which prevents access to Windows Recovery Mode with the following commands:
bcdedit /set {default} recoveryenabled No bcdedit /set {default} bootstatuspolicy ignoreallfailures
- Deletes the Windows event logs to cover up evidence of malicious activity with the following PowerShell command:
Powershell -command "Get-EventLog -LogName * | ForEach { Clear-EventLog $_.Log }"Encryption process
AvosLocker leverages multiple threads to encrypt the target files on an infected machine. Then it enumerates all drives (e.g., fixed, removable, and network shares) based on the command line arguments. The ransomware then performs a file extension check where the files with the extensions in Table 2 are excluded and not encrypted.
avos | avoslinux | avos2 | avos2j | themepack | nls | diagpkg | msi | lnk |
exe | cab | scr | bat | drv | rtp | msp | prf | msc |
ico | key | ocx | diagcab | diagcfg | pdb | wpx | theme | mpa |
hlp | icns | rom | dll | msstyles | mod | ps1 | nomedia | spl |
ics | hta | bin | cmd | ani | 386 | lock | cpl | adv |
cur | idx | sys | com | deskthemepack | shs | ldf | icl | msu |
In addition, AvosLocker won’t encrypt any files listed in Table 3.
Thumbs.db | ntuser.ini | ntuser.dat.log | ntuser.dat | ntldr | iconcache.db |
desktop.ini | config.msi | bootsect.bak | bootfont.bin | boot.ini | autorun.inf |
Furthermore, AvosLocker won’t encrypt the directories in Table 4.
All Users | AppData | boot | bootmgr |
Games | Intel | Microsoft. | Program Files/Program Files (x86) |
ProgramData | Public | Sophos | System Volume Information |
Windows | Windows.old | WinNT | MicrosoftSQL Server |
AvosLocker encrypts file content using AES in CBC mode with a randomly generated AES key. The AES symmetric key is then encrypted with a 2,048-bit RSA public key embedded in the ransomware binary. Finally, the RSA data containing the encrypted AES key is Base64 encoded and appended to the end of the encrypted file (see Figure 4). Then, the file extension is changed to .avos2.
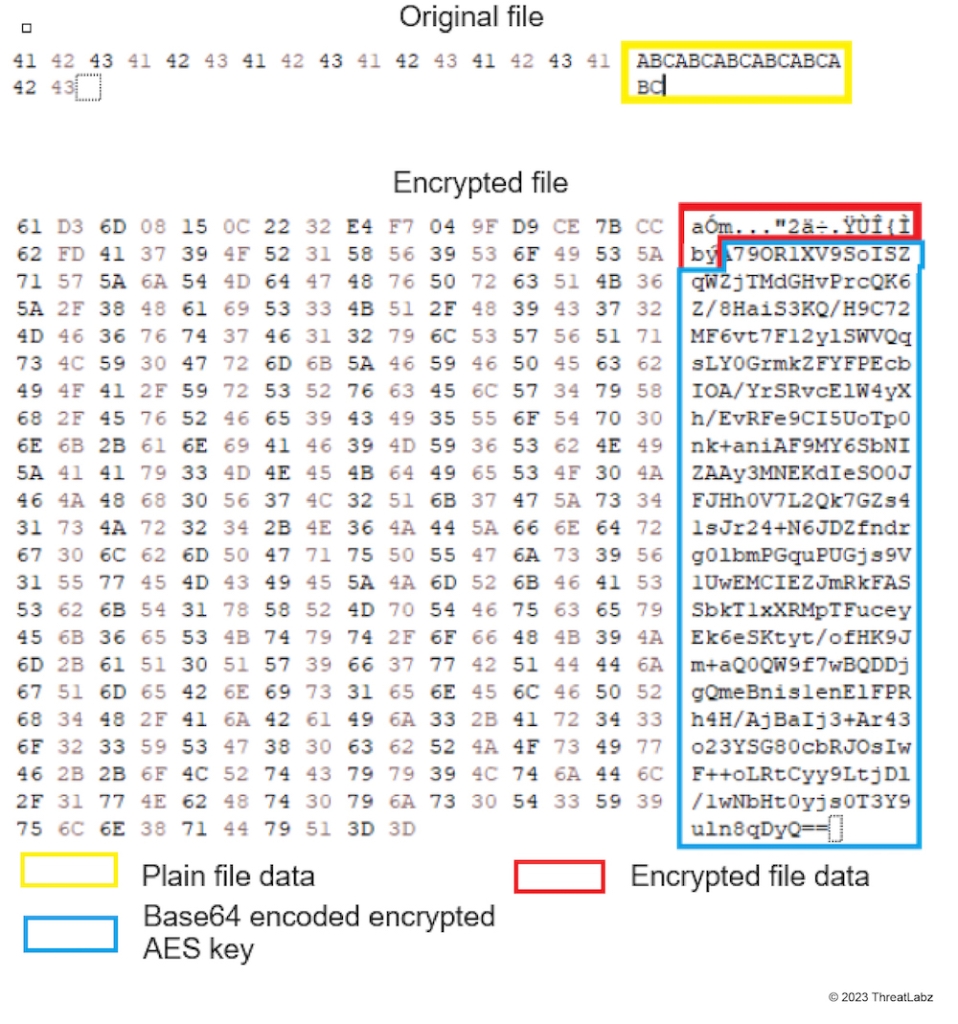
Figure 4: AvosLocker encrypted file contents
During the encryption phase, the ransomware also prints debug messages to the console that show encryption statistics to the threat actor as shown below.
drive D: took 0.003000 seconds
drive Z: took 0.119000 seconds
drive A: took 1.060000 seconds
drive C: took 19.672000 seconds
Waiting for encryption threads to finish ... [OK]
Encryption Stats
[+] Locked objects: 6313
asym time: clocks 14465
total time: clocks 20648 | 20.648000 secondsAfter encryption, AvosLocker drops a ransom note named GET_YOUR_FILES_BACK.txt as shown in Figure 5.
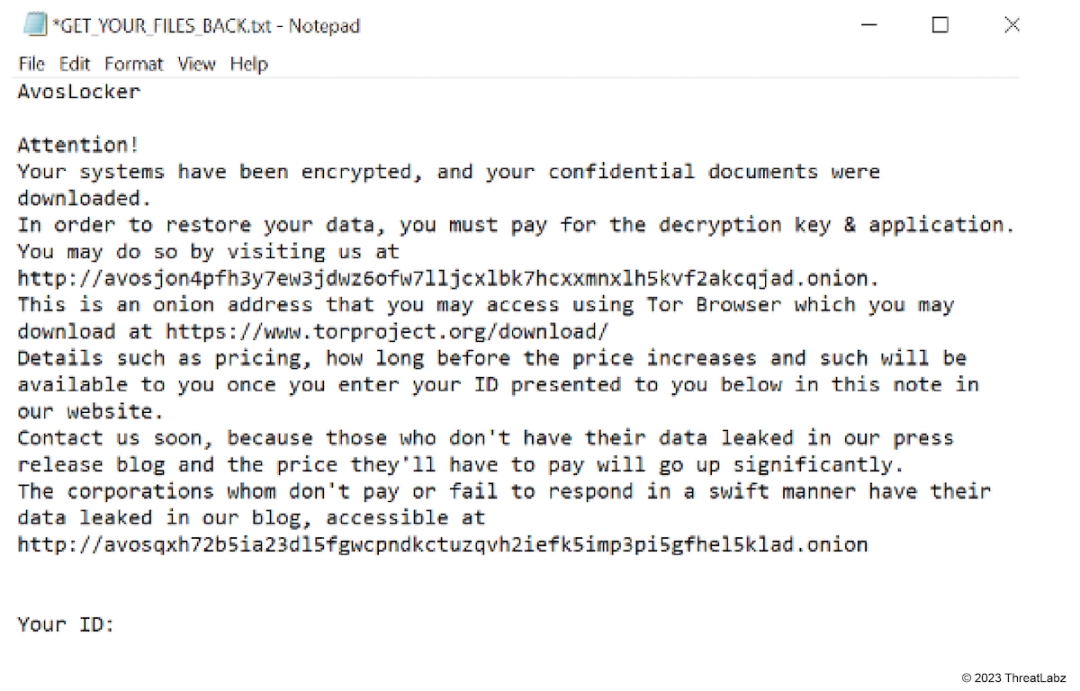
Figure 5: AvosLocker ransom note
AvosLocker also changes the Windows desktop wallpaper (shown in Figure 6) to a message similar to the ransom note text file.
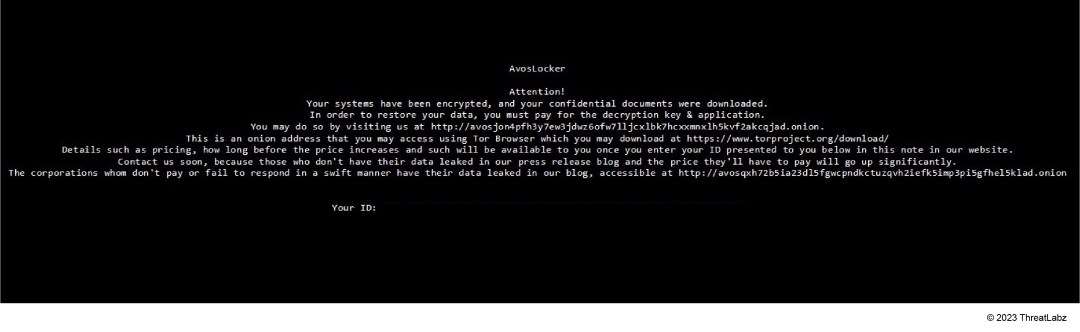
Figure 6: AvosLocker ransom note wallpaper
The victim ID mentioned in the ransom note is hardcoded in the AvosLocker binary and the ransom note’s filename is README_FOR_RESTORE. ThreatLabz also observed AvosLocker using different file extensions such as .avos, .avos2, and .avoslinux, with the latter being used for the Linux variant. The Linux variant is very similar to the Windows version, but also possesses the capability to terminate and encrypt ESXi virtual machines.
Data Leak Site
If a victim decided not to pay a ransom, the group would post stolen data to their data leak site hosted via a Tor hidden service. This tactic was designed to pressure victims to pay a ransom to avoid a loss of sensitive information that may be damaging to the victim organization when publicly disclosed. The AvosLocker data leak site has been down since July 2023 and the payment site went down in August 2023. ThreatLabz observed a total of 60 victims’ data posted on the data leak site as shown in Figure 7.
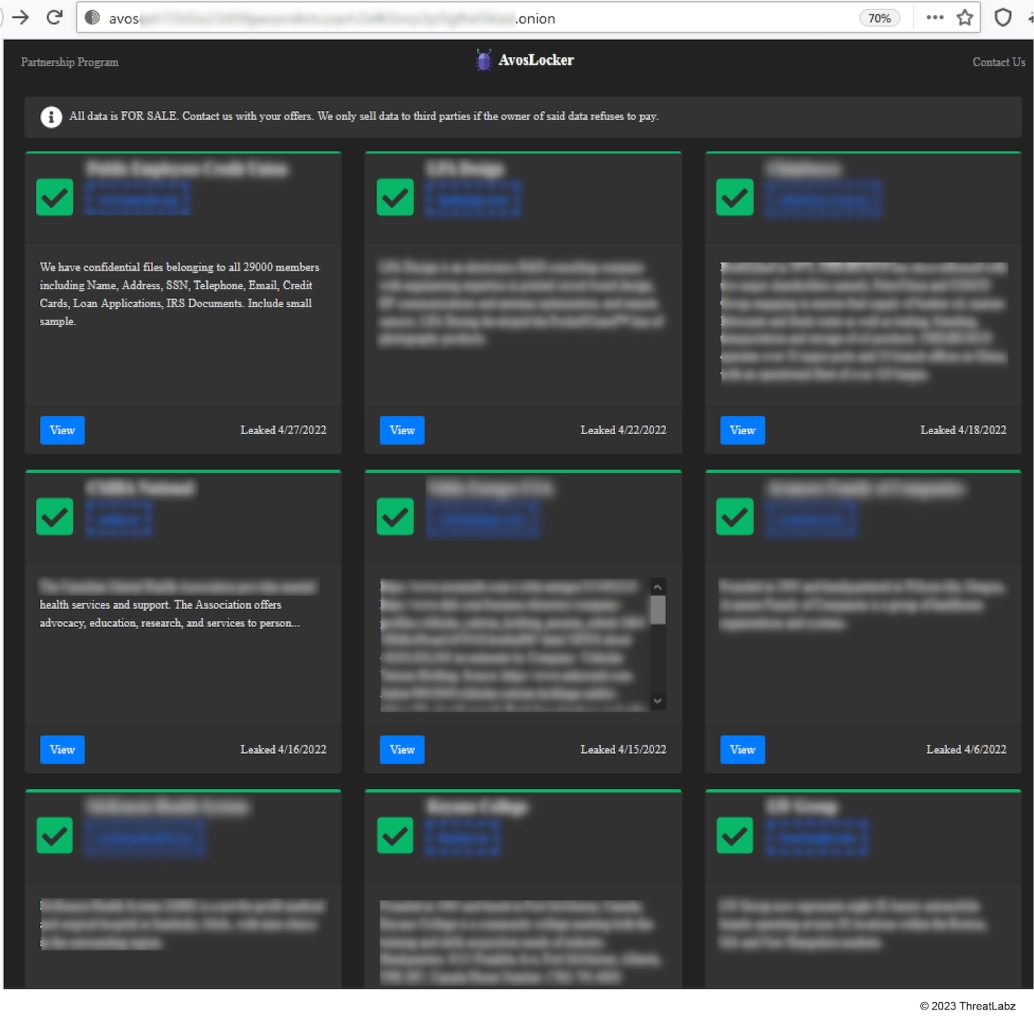
Figure 7: AvosLocker data leak site
Anti-Analysis
All the important strings in AvosLocker ransomware samples are obfuscated using ADVObfuscator,which pushes encoded versions of strings to the stack, and then decodes them at runtime (as shown in Figure 8), using simple but different algorithms and keys.
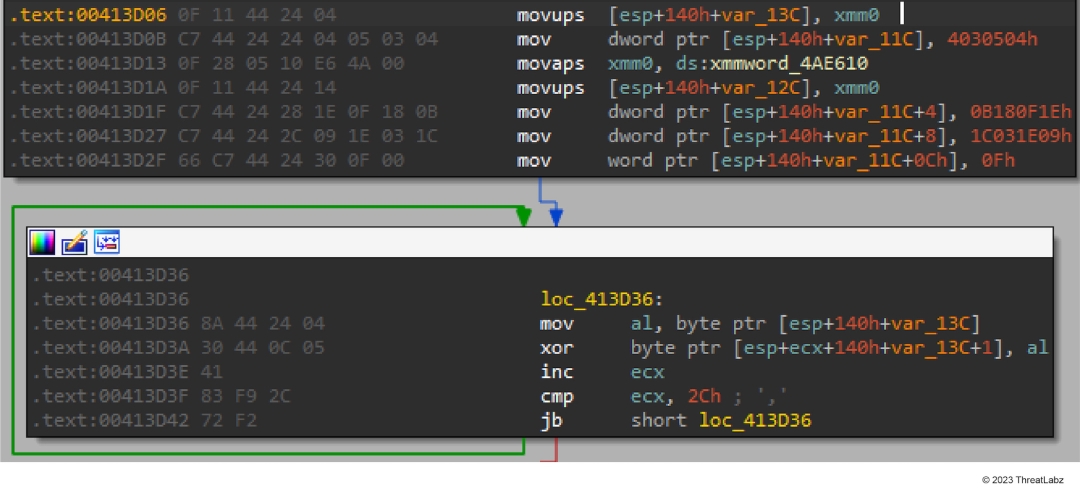
Figure 8: AvosLocker string obfuscation
For instance, the string above decodes to: cmd /c wmic shadowcopy delete /nointeractive
NetMonitor Backdoor
AvosLocker leverages NetMonitor, a tool that appears like a legitimate network monitoring utility, but in reality acts as a backdoor for AvosLocker.
NetMonitor establishes persistence after being installed as a system service, using names such as: NetAppTcp, NetAppTcpSvc, WazuhWinSrv, RSM, WinSSP, WebService, etc. Once initiated, NetMonitor tries to contact its C2 server every 5 seconds using a hardcoded IP address and port (usually 443). The malware uses raw sockets and a small binary protocol for all communication, where the encrypted ping packet contains content similar to that shown in Figure 9.
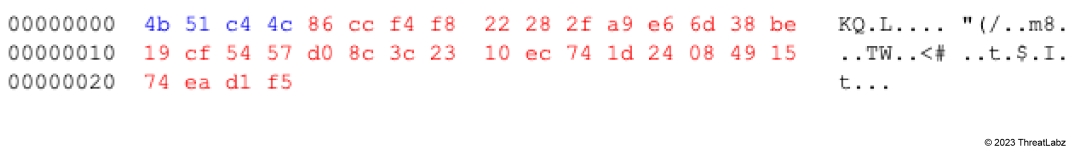
Figure 9: NetMonitor encrypted communication
The first four bytes are random, and the remaining bytes are an RC4 encrypted payload with an 8 byte key. Figure 10 shows the actual payload content after the decryption.

Figure 10: NetMonitor decrypted communication
The first four bytes are also random (and identical to the previous four bytes prepended to the encrypted payload) followed by a command. Depending on the command received, NetMonitor then starts listening on a port or acts as a reverse proxy server.
NetMonitor was closely tied to AvosLocker, with the last observed activity occurring in the first half of 2023, and no new samples have been identified since August 2023.
Conclusion
AvosLocker is a ransomware group that was active and performing double extortion attacks until May 2023. The group also targeted multiple operating systems with different ransomware variants. Zscaler ThreatLabz continues to track different ransomware groups and add indicators of compromise to protect our customers. Please read Zscaler’s yearly ransomware report to learn more about the various trends and most significant ransomware groups.
Zscaler Coverage
Cloud Sandbox
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators related to AvosLocker at various levels with the threat names listed below.
Win32.Ransom.Avos
Indicators of Compromise (IOCs)
AvosLocker
Hashes
1076a979c6a7633ee3a4884d738452c51330887fe501036aff6ed443340e9405d285f1366d0d4fdae0b558db690497ea76e177a94834b3f7c63257bc8011f60fb27f0f2826bacd329fb28d9cda002d7d16a5d134d50eeb34989b48dca166462df9de6998546e9ea169c54527962e1e921933f61951738b6fdbfff3fa0f65d71263e12fa6203dc61fc82343e7dec1b33b4e75f8dc15a82674c57c4f12dbd788088c4bfd216fb8e69f7f1e1f4cb1e3f9a10e9432cd9e9405b04f4e46b368585d6019944159dfa94a1b75effd85e6b906dc869fc579f45a790b7c485d52cb2c89860b3888d8683d3ebb27627452a0179575194c16941dc618facef7d0c4749a39a7c41c5de8abeb92adaf8a86cf8b31570ef091b9085d35e61945c743e3683b1b712d7cf26f4e4dacf637f7ef0b1edfbda5a0a60441609f42f2f79c7826db9ae296
URLs
Payment Sites:
avosjon4pfh3y7ew3jdwz6ofw7lljcxlbk7hcxxmnxlh5kvf2akcqjad.onionavos2fuj6olp6x36.onion
Data Leak Sites:
avosqxh72b5ia23dl5fgwcpndkctuzqvh2iefk5imp3pi5gfhel5klad.onionavos53nnmi4u6amh.onion
NetMonitor
Hashes
A5485e8f09f6428b42b499bc914532e6e5dac186720ea10f3752aa30a96d3fc09ff900a05d75b97948a3b52d8835b21f15e948c18ea77efb5ffbf0a72d05d34885e44d1333422e9b550c94ad7b7202a0d59dca267722dfd923350d5b139b1036
C&Cs
194.213.18.138:443146.70.147.17:443142.44.132.90:44345.66.249.80:44323.227.198.197:44323.236.181.117:443
Source: https://www.zscaler.com/blogs/security-research/retrospective-avoslocker
Views: 0