Summary:
Keypoints:
MITRE Techniques
CERT-AGID has recently released a new version of the hashr tool (v.2.0.1) as free and open-source software under the EUPL license. This tool, available for free download from the dedicated page, is designed for the detection of malicious files within a filesystem by comparing the hash values of found files with a list of known hash fingerprints. Hashr can be used with custom search lists or, for public administrations accredited to the CERT-AGID IoC feed, with hashes derived from recorded malicious campaigns that impact the Italian territory.
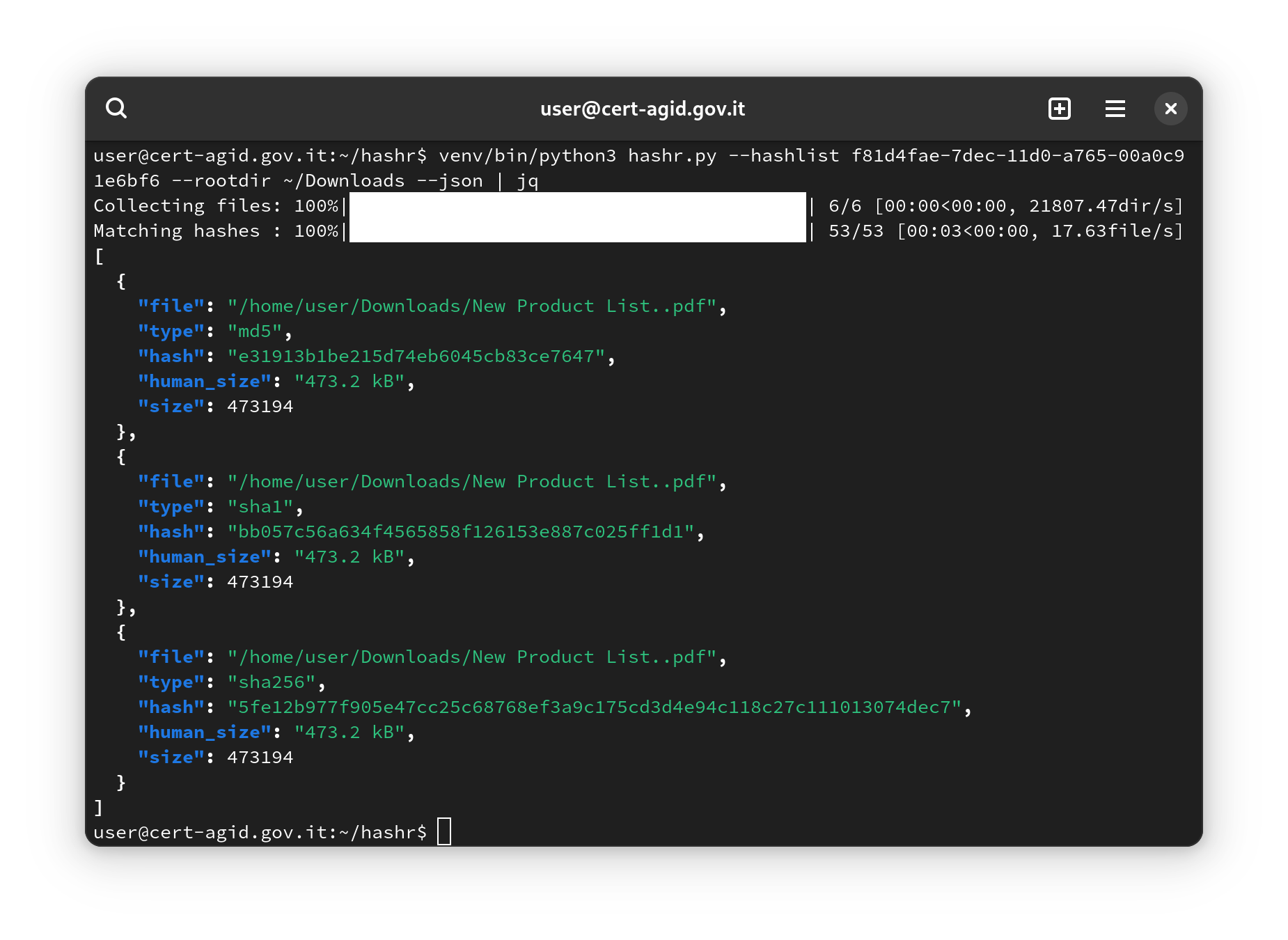
All Public Administrations can register for the CERT-AGID IoC feed to access a real-time stream of Indicators of Compromise (IoC), which lists and shares data on detected malware and phishing campaigns during daily monitoring and prevention activities, such as the IP addresses used for fraudulent activities, URLs of malicious sites, hashes of harmful files, and other information. This service, offered for free, is intended exclusively for Public Administrations.
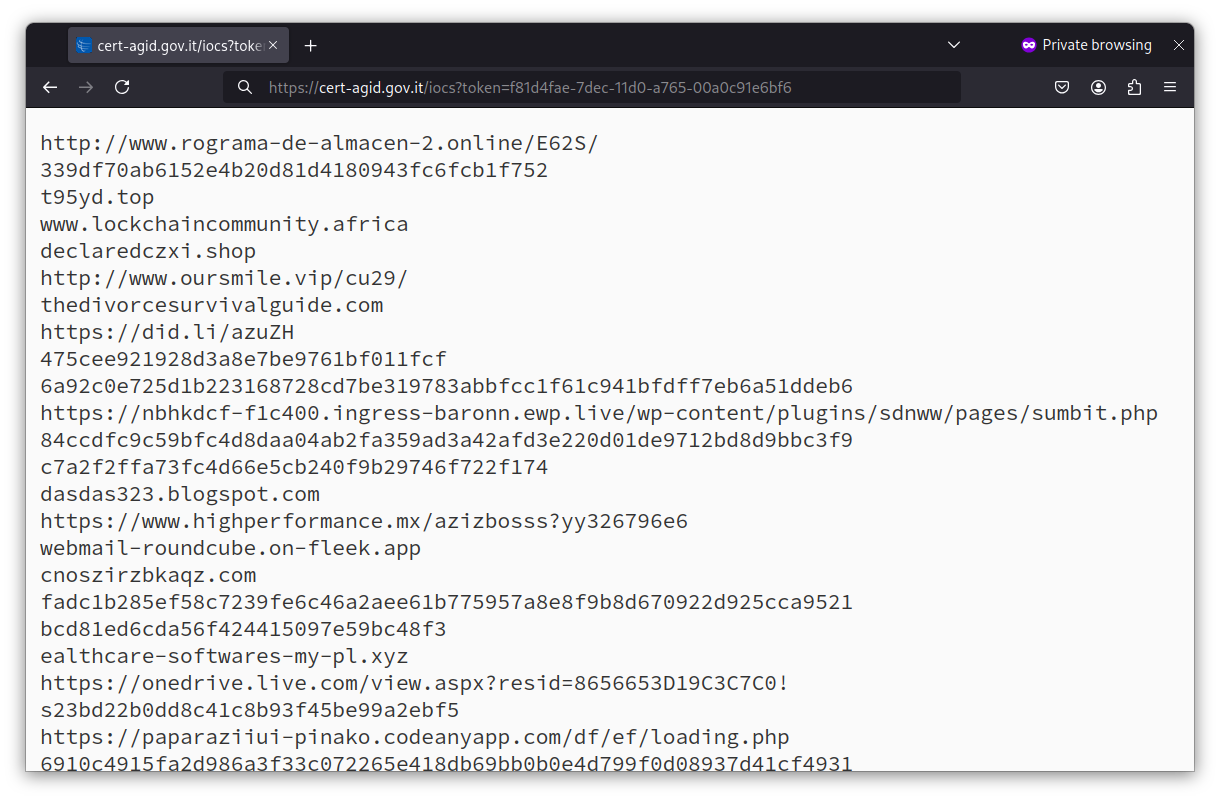
In synergy with the IoC Feed, hashr allows for searching files with hashes related to known malicious campaigns or APTs analyzed by CERT-AGID, enabling quick identification of compromised files. The use of hashr is particularly useful for cybersecurity investigations, forensic analysis, and file integrity verification on large filesystems.
The combined use of hashr and the IoC feed significantly enhances the ability to prevent and detect cyber threats, increasing the overall security of digital infrastructures.
These two tools provided by AGID represent an opportunity for administrations to improve the security of their IT systems, while also complying with the guidelines of the 2024-2026 Digital Plan for Public Administration and strengthening the overall digital resilience of Public Administration.
Useful Links:
Source: Original Post