
Summary :
Sophos has analyzed GootLoader, a malware that uses cat-related content to lure victims, leading to data theft and ransomware deployment. The research identified numerous indicators of compromise (IoCs) linked to this threat. #GootLoader #CyberThreats #MalwareAnalysis
Keypoints :
- GootLoader uses SEO poisoning to direct users to malicious sites.
- The malware can deploy a second-stage payload called GootKit, which is a data stealer and RAT.
- Sophos identified 12 domains as IoCs, with further analysis revealing additional related domains and IPs.
- 33 email-connected domains and 15 IP addresses were also identified, with six being malicious.
- The threat actors prefer using older domains created between 2015 and 2020.
MITRE Techniques :
- Phishing (T1566): Utilizes cat-related content to lure victims into visiting malware-laden sites.
- Command and Control (T1071): Maintains communication with compromised systems through multiple domains.
- Remote Access Tools (T1219): Employs GootKit for remote access and data theft.
Indicator of Compromise :
- [domain] beezzly[.]com
- [domain] chanderbhushan[.]com
- [domain] climatehero[.]me
- [domain] fannisho[.]com
- [domain] playyourbeat[.]com
- [email] 33 email-connected domains
- [ip address] 103[.]169[.]142[.]0
- [ip address] 141[.]193[.]213[.]10
- [ip address] 75[.]2[.]60[.]5
Back in 2015, a survey found that cats drove 15% of the overall Internet traffic. That said, it is not surprising for threat actors to use cat-related content to lure victims to visit their malware-laden sites. Such was the case for GootLoader, which allowed cybercriminals to steal data and deploy post-exploitation tools and ransomware.
Sophos recently analyzed GootLoader, which has been known to use search engine optimization (SEO) poisoning to gain initial access. Users who fall for the ruse get directed to a compromised site that hosts a malicious payload. If the malware remains undetected on a victim’s computer, it makes way for a second-stage payload dubbed “GootKit,” a highly evasive data stealer and remote access Trojan (RAT). Threat actors can use GootKit to deploy ransomware or other tools for follow-on exploitation.
The Sophos researchers identified 12 domains as indicators of compromise (IoCs) in their report. The WhoisXML API research team expanded the IoC list aided by exhaustive DNS intelligence and found:
- 33 email-connected domains
- 15 IP addresses, six of which turned out to be malicious
- 692 IP-connected domains
- 302 string-connected domains
A sample of the additional artifacts obtained from our analysis is available for download from our website.
About the GootLoader IoCs
First off, we sought to find more information on the 12 domains tagged as IoCs. A bulk WHOIS lookup for them revealed that:
- Only nine of the domains had current WHOIS records.
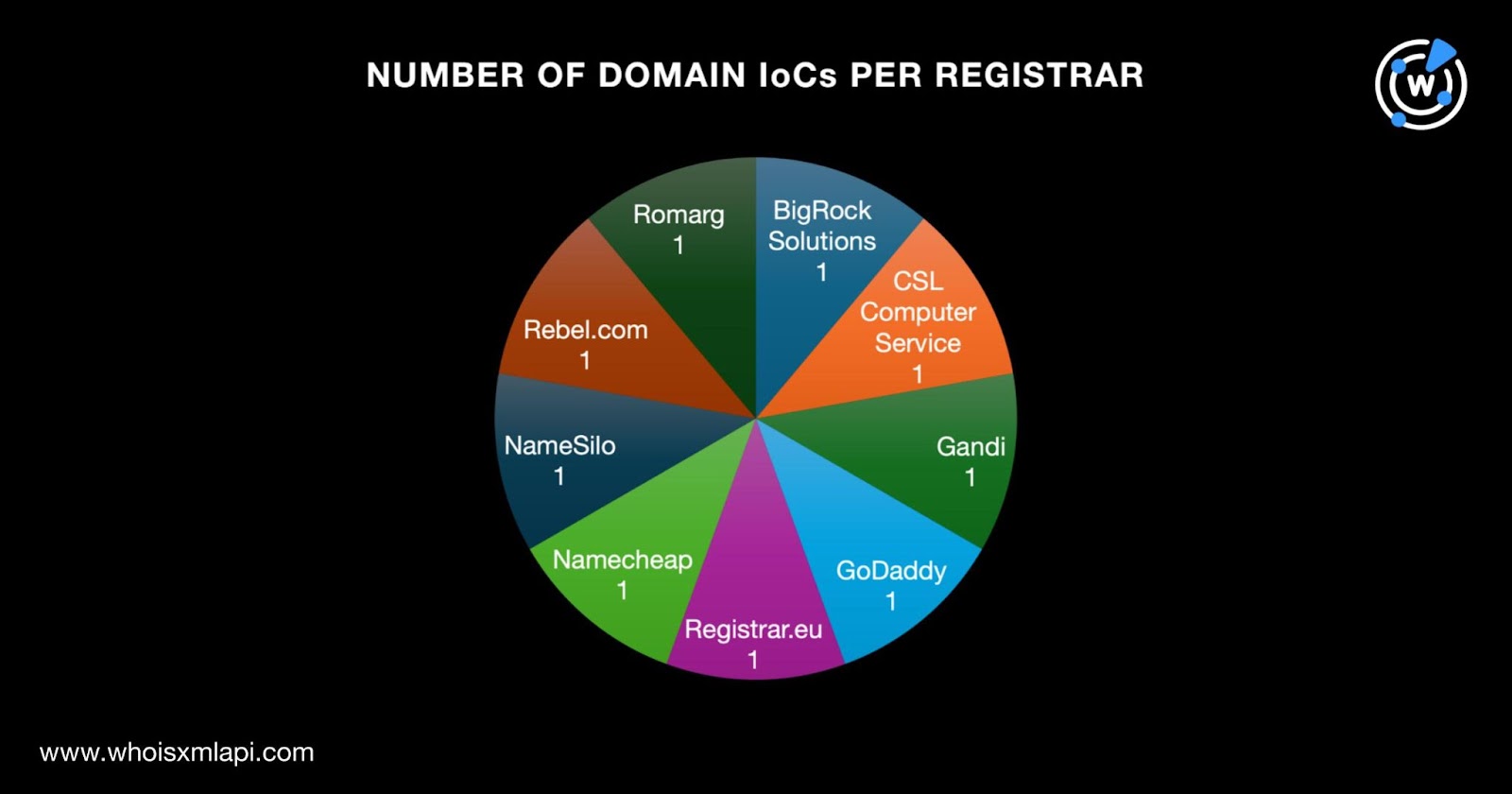
- The nine domains with current WHOIS records were administered by a different registrar each, namely, BigRock Solutions, CSL Computer Service, Gandi, GoDaddy, Registrar.eu, Namecheap, NameSilo, Rebel.com, and Romarg.
-
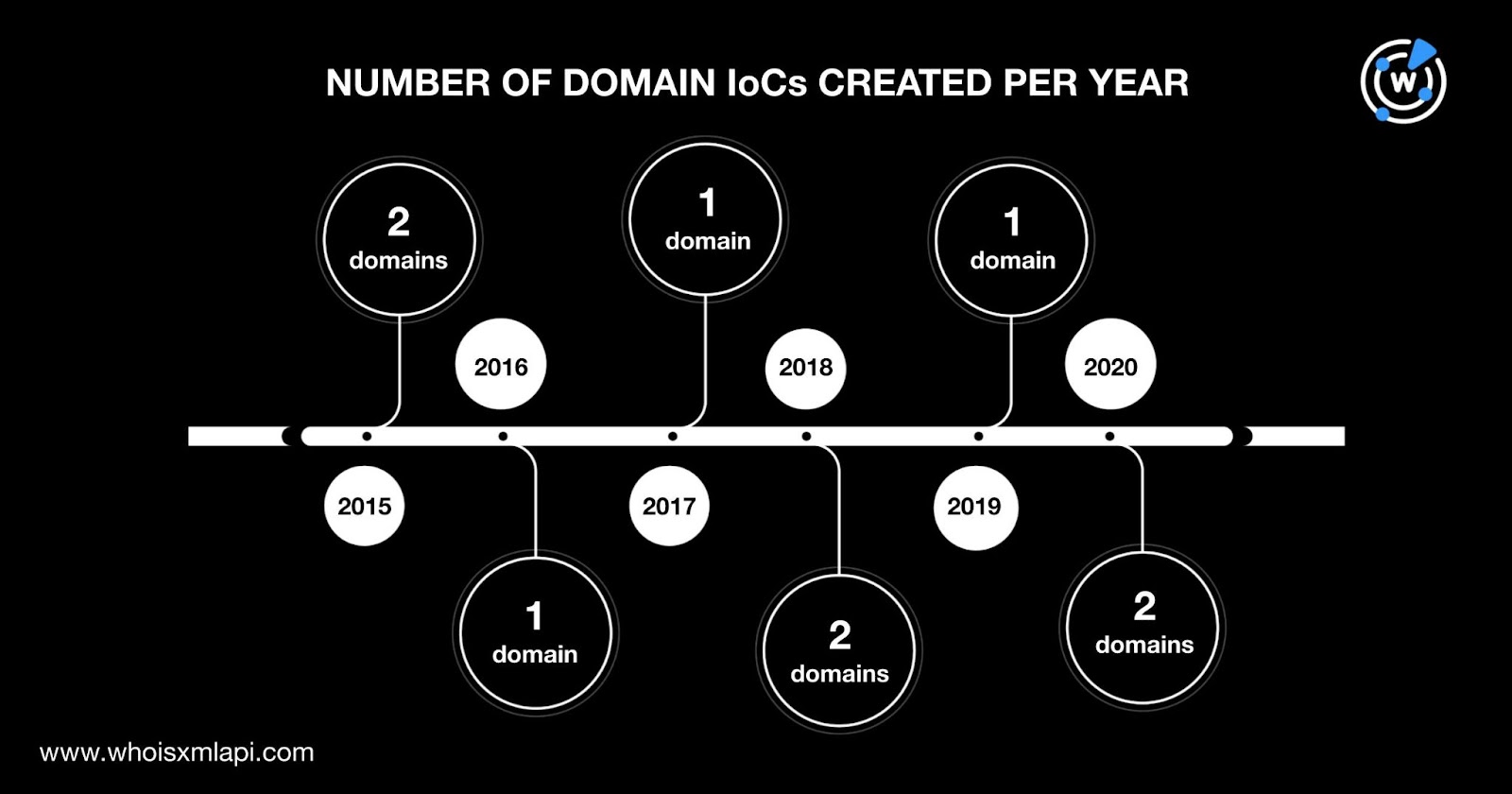
The nine domains were created between 2015 and 2020, indicating that the threat actors may have preferred using old domains.
-
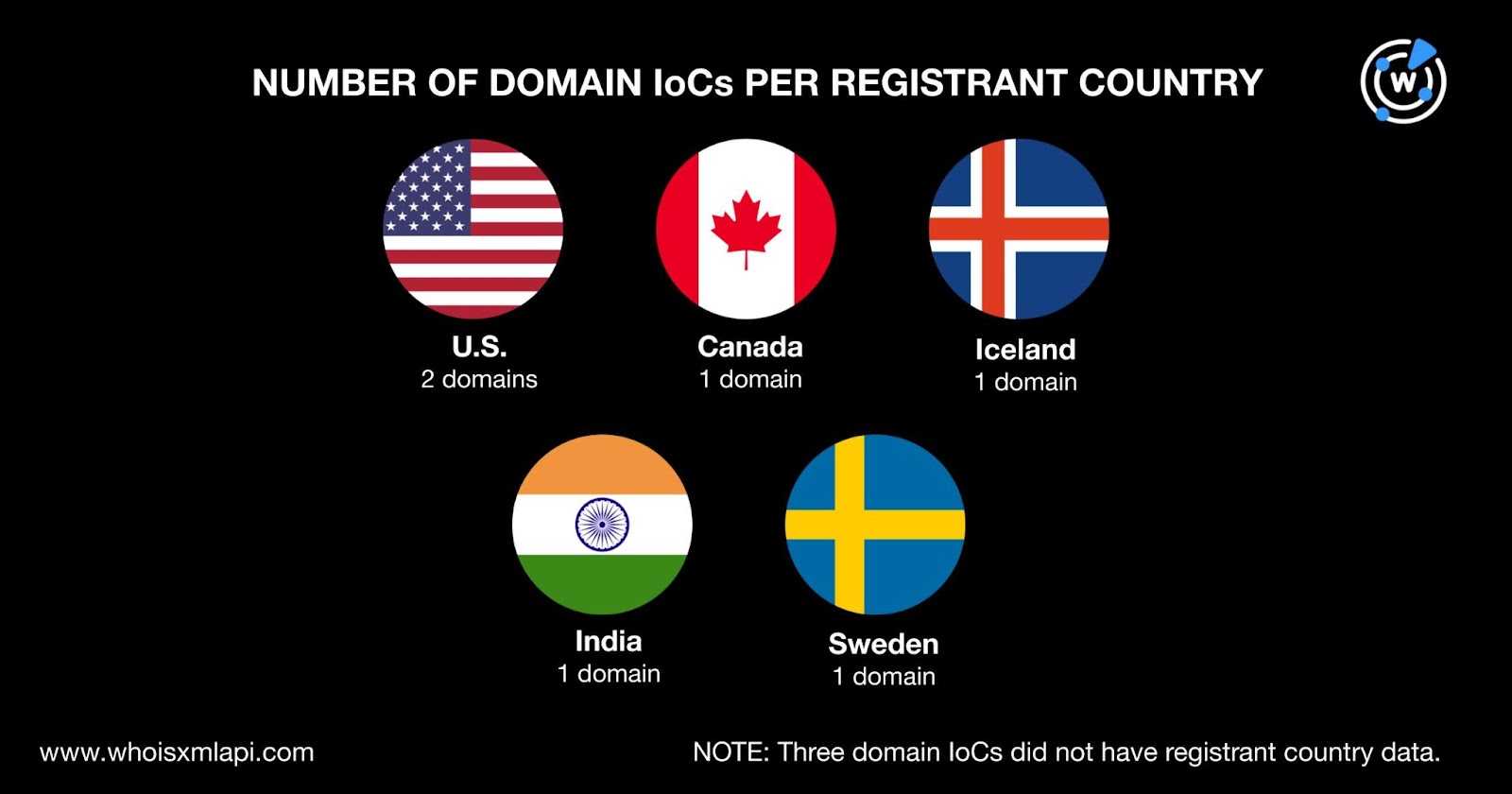
While three of the nine domains did not have registrant country details in their records, we found that two were registered in the U.S., while one each was registered in four different countries, namely, Canada, Iceland, India, and Sweden.
We also looked at the passive DNS records of the 12 domains tagged as IoCs and found that 83% or 10 of them have resolved to 50 or more IP addresses each since 2019. Take a look at five examples below.
| DOMAIN IoC | DATE STARTED RESOLVING TO AN IP ADDRESS | TOTAL NUMBER OF IP ADDRESSES |
|---|---|---|
| beezzly[.]com | 4 October 2019 | 50 |
| chanderbhushan[.]com | 2 May 2021 | 50 |
| climatehero[.]me | 4 October 2019 | 100+ |
| fannisho[.]com | 4 October 2019 | 51 |
| playyourbeat[.]com | 1 October 2019 | 92 |
The domain IoC playyourbeat[.]com, for instance, has seen 92 DNS changes since it first resolved to IP address 85[.]187[.]128[.]9 on 4 October 2019 according to DNS Chronicle Lookup. The first shift occurred 462 days after it was first recorded in our passive DNS database on 8 January 2021. After that, the number of days in-between each change ranged between one and 293 from 8 January 2021 to 1 September 2024.
GootLoader IoC List Expansion Findings
We began our search for connected artifacts by querying the 12 domains tagged as IoCs on WHOIS History API. That led to the discovery of 22 email addresses in their historical WHOIS records although only nine were public.
Next, we queried the nine public email addresses on Reverse WHOIS API. Three of them appeared in the current WHOIS records of other domains, leading us to uncover 33 email-connected domains after filtering out duplicates and the IoCs.
DNS lookups for the 12 domains tagged as IoCs showed that 11 actively resolved to 15 unique IP addresses.
Threat Intelligence API queries for the 15 IP addresses revealed that six have already figured in malicious campaigns. Take a look at three examples below.
| MALICIOUS IP ADDRESS | ASSOCIATED THREAT TYPES |
|---|---|
| 103[.]169[.]142[.]0 | Attack Command and control (C&C) Generic Malware Phishing Suspicious |
| 141[.]193[.]213[.]10 | Attack C&C Generic Malware Phishing Spam Suspicious |
| 75[.]2[.]60[.]5 | Attack C&C Generic Malware Phishing Spam |
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Full Research: https://circleid.com/posts/a-dns-investigation-of-the-gootloader-campaign