Domestic violent extremists (DVEs) in the United States are increasingly doxing senior leaders from the public and private sectors — publishing their personally identifiable information (PII) with malicious intent and without the leaders’ consent. Historically, DVE doxing attempts usually targeted other DVEs and political opponents, but recent trends show a broadening scope of targets, including government officials, executives, and heads of various institutions. These doxes often follow the leaders’ or their companies’ involvement in contentious issues, such as stances on geopolitical conflicts, diversity policies, and political alignments.
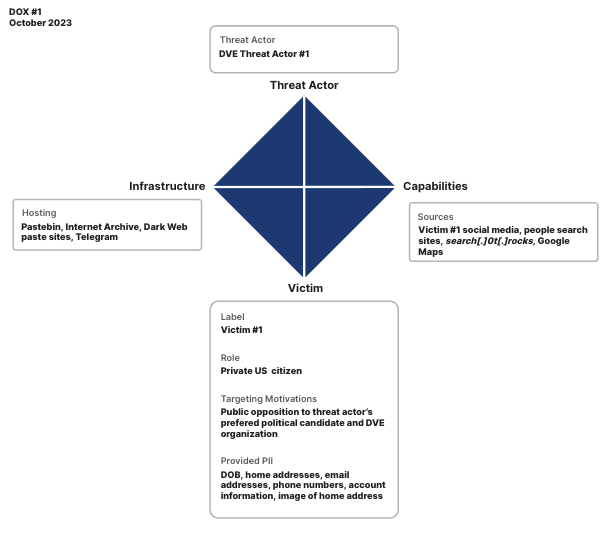 Diamond model analysis of Dox #1 (Source: Recorded Future)
Diamond model analysis of Dox #1 (Source: Recorded Future)
Escalating Threats: The Rise of DVE Doxing and Strategies for Defense
Insikt Group evaluated three case studies of DVE doxing attempts, examining the DVE threat actors, their targets, their sources and methods for conducting the dox, and their means of publishing the dox. Research found that those who are doxed by DVEs are at a heightened risk of physical threats, such as harassment, stalking, protests, surveillance, and even physical attacks, as well as cyber threats. Victims and their organizations face not only physical risks but also significant financial and reputational damage from the negative sentiment campaigns that typically accompany doxing incidents. A notable uptick in doxing, especially against corporate leaders, was reported in 2023, with a SafeHome survey indicating that eleven million Americans have been doxed.
Several factors are expected to spur DVE doxing efforts, including geopolitical events like the Israel-Hamas conflict, the 2024 US presidential election, and private sector engagement with social justice issues. As businesses and government entities navigate these sensitive areas, their leaders may increasingly find themselves in the crosshairs of DVE doxing campaigns, particularly as they make public statements or policy decisions on controversial issues among DVEs.
To combat the threat of doxing, leaders are advised to enhance their cyber hygiene, utilize threat monitoring services like the Recorded Future Intelligence Cloud, and take proactive measures to minimize their digital footprint. This includes removing PII from accessible online platforms, conducting regular audits of their digital presence, and preparing for potential doxing incidents. Following a doxing event, it’s crucial to document the incident, assess the risks based on the exposed information, attempt to mitigate the source of the leak and engage with law enforcement if necessary.
To read the entire analysis, click here to download the report as a PDF.
Doxing, short for “dropping dox,” is a cyberattack that involves researching and publicly broadcasting private or identifying information about an individual or organization. This information can include addresses, phone numbers, email addresses, social security numbers, and other personal data. The purpose of doxing is often to intimidate, harass, or publicly shame the target.
DVE stands for Domestic Violent Extremists. These are individuals or groups based within a country who commit or plan to commit violent acts in furtherance of ideological, political, or social goals. DVEs often target government institutions, individuals, or specific communities, and their activities can include terrorism, hate crimes, and other forms of violence.
MITRE TTP :
- Initial Access (TA0001)
- Spearphishing (T1566): Domestic Violent Extremists (DVEs) may use spearphishing tactics to obtain personally identifiable information (PII) for doxing purposes.
- Execution (TA0002)
- User Execution (T1204): Victims may inadvertently execute malicious actions by interacting with content shared by DVEs, such as clicking on links that lead to doxing materials.
- Collection (TA0009)
- Gather Victim Identity Information (T1589): DVEs collect PII, including home addresses, phone numbers, and email addresses, from various sources for doxing.
- Impact (TA0040)
- Data Manipulation (T1565): DVEs manipulate data by publishing victims’ PII online without consent and with malicious intent.
- Command and Control (TA0011)
- Web Protocols (T1071): DVEs use web protocols and online platforms, such as Telegram channels, blogs, and paste sites, to host and distribute dox files.
- Exfiltration (TA0010)
- Exfiltration Over Web Service (T1567): DVEs may use web services to exfiltrate collected PII for the purpose of doxing.
- Defense Evasion (TA0005)
- Obfuscated Files or Information (T1027): DVEs may obfuscate dox files or use code words to avoid detection and terms of service (ToS) enforcement on online platforms.