
Recorded Future’s Insikt Group has been monitoring the activities of Russian state actors who are intensifying their efforts to hide command-and-control network traffic using legitimate internet services (LIS) and expanding the range of services misused for this purpose. BlueBravo is a threat group tracked by Insikt Group, whose actions align with those of the Russian advanced persistent threat (APT) groups APT29 and Midnight Blizzard, both attributed to Russia’s Foreign Intelligence Service (SVR).
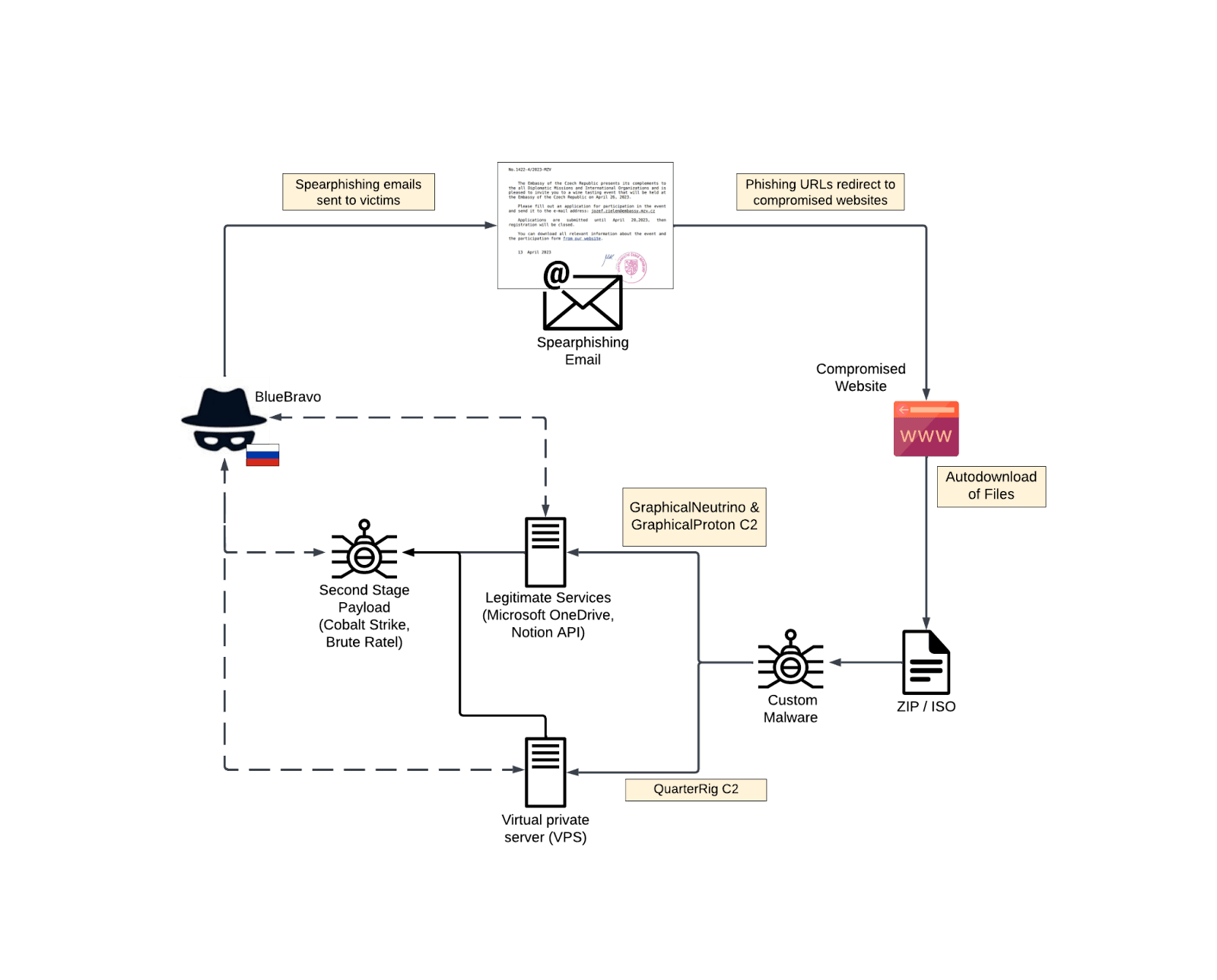
(Overview of BlueBravo attack flow (Source: Recorded Future)
In January 2023, Insikt Group reported on BlueBravo’s use of a themed lure to deliver malware called GraphicalNeutrino. They identified several consistent tactics employed by the group, including compromised infrastructure, known malware families, third-party services for command-and-control (C2), and reused lure themes. Another malware variant used by BlueBravo, named GraphicalProton, was discovered. Unlike GraphicalNeutrino, which used Notion for C2, GraphicalProton uses Microsoft’s OneDrive or Dropbox for communication.
The group’s misuse of LIS is an ongoing strategy, as they have used various online services such as Trello, Firebase, and Dropbox to evade detection. BlueBravo appears to prioritize cyber-espionage efforts against European government sector entities, possibly due to the Russian government’s interest in strategic data during and after the war in Ukraine.
Based on observed trends, Insikt Group predicts that BlueBravo will continue to adapt and create new malware variants while leveraging third-party services for C2 obfuscation. Defenders are urged to invest additional time and resources to track the evolving group, particularly organizations targeted by Russian state actors in relation to the Russia-Ukraine conflict.
BlueBravo is expected to continue developing infrastructure and compromising vulnerable websites to deploy new strains of malware, targeting diplomatic and foreign policy institutions in Eastern Europe, as these organizations provide valuable insight for the Russian intelligence consumers during the ongoing war in Ukraine.
To read the entire analysis with endnotes, click here to download the report as a PDF.
Appendix A — Indicators of Compromise
|
Compromised Domains Associated with BlueBravo Activity: te-as[.]no easym6[.]com remcolours[.]com simplesalsamix[.]com sylvio[.]com[.]br reidao[.]com mightystake[.]com sharpledge[.]com fondoftravel[.]com URLs Associated with BlueBravo Activity: Files: |
Appendix B — Mitre ATT&CK Techniques
| Tactic: Technique | ATT&CK Code |
| Resource Development: Compromise Infrastructure | T1584 |
| Execution: User Execution: Malicious File | T1204.002 |
| Persistence: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1547.001 |
| Defense Evasion: Obfuscated Files or Information: HTML Smuggling | T1027.006 |
| Defense Evasion: Obfuscated Files or Information: Dynamic API Resolution | T1027.007 |
| Defense Evasion: Masquerading: Right-to-Left Override | T1036.002 |
| Defense Evasion: Masquerading: Match Legitimate Name or Location | T1036.005 |
| Defense Evasion: Deobfuscate/Decode Files or Information | T1140 |
| Defense Evasion: Hijack Execution Flow: DLL Search Order Hijacking | T1574.001 |
| Defense Evasion: Hijack Execution Flow: DLL Side-Loading | T1574.002 |
| Defense Evasion: Impair Defenses: Disable or Modify Tools | T1562.001 |
| Discovery: System Owner/User Discovery | T1033 |
| Discovery: System Information Discovery | T1082 |
| Command and Control: Application Layer Protocol: Web Protocols | T1071.001 |
| Command and Control: Web Service: Bidirectional Communication | T1102.002 |
| Command and Control: Ingress Tool Transfer | T1105 |
Source: Original Post
“An interesting youtube video that may be related to the article above”