
Recorded Future’s Insikt Group has identified TAG-70, a threat actor likely operating on behalf of Belarus and Russia, conducting cyber-espionage against targeting government, military, and national infrastructure entities in Europe and Central Asia since at least December 2020. In its latest campaign, which ran between October and December 2023, TAG-70 exploited cross-site scripting (XSS) vulnerabilities in Roundcube webmail servers in its targeting of over 80 organizations, primarily in Georgia, Poland, and Ukraine. This activity is reminiscent of other Russian-aligned threat groups such as BlueDelta (APT28) and Sandworm, which have targeted email solutions, including Roundcube, in previous campaigns.
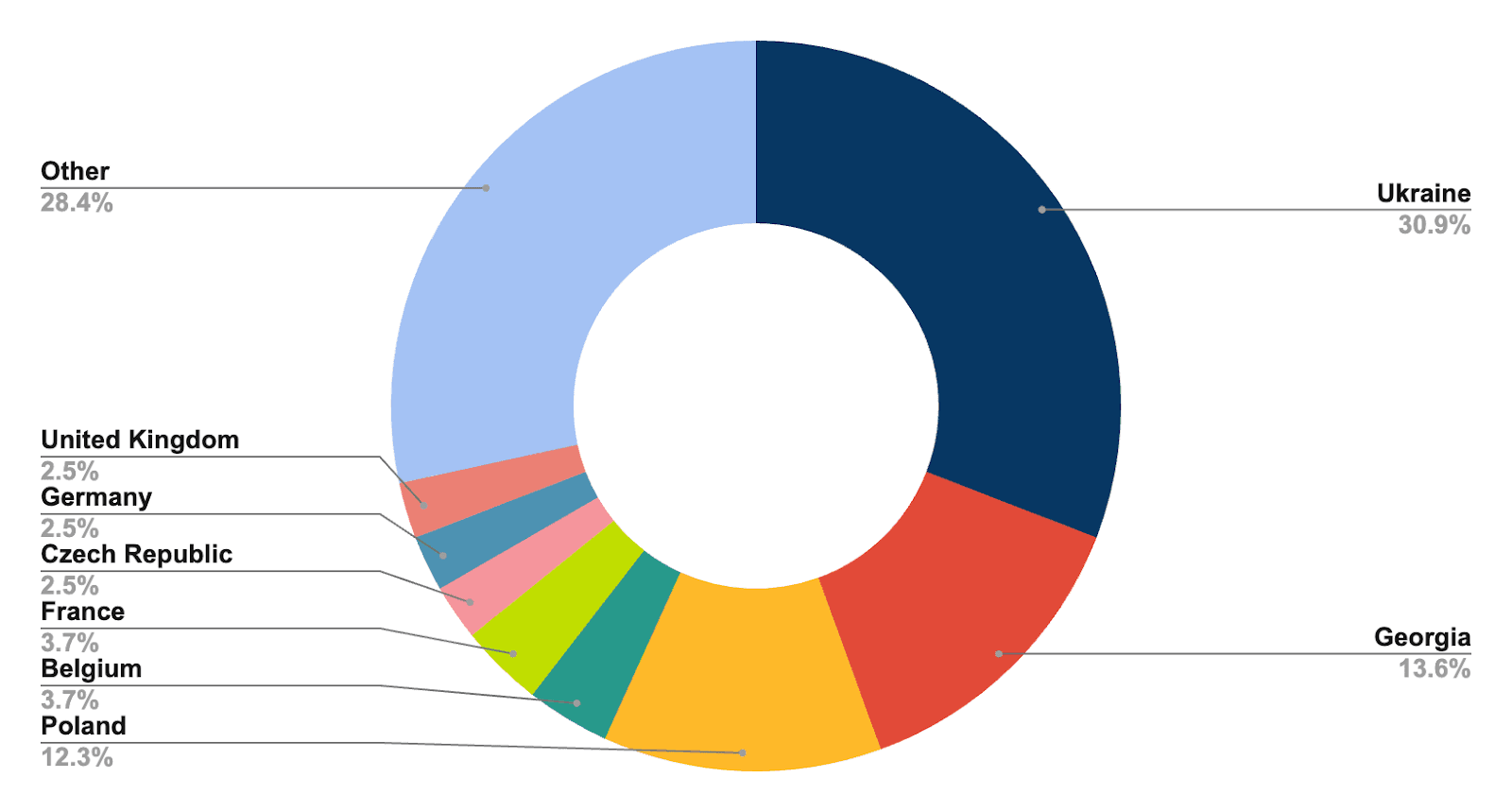
Geographic spread of victims of TAG-70s Roundcube exploit in October 2023 (Source: Recorded Future)
The compromised email servers represent a significant risk, particularly in the context of the ongoing conflict in Ukraine. They could expose sensitive information about Ukraine’s war effort, its diplomatic relations, and its coalition partners. Moreover, the targeting of Iranian embassies in Russia and the Netherlands suggests a broader geopolitical interest in assessing Iran’s diplomatic activities, especially regarding its support for Russia in Ukraine. Similarly, espionage against Georgian government entities reflects interests in monitoring Georgia’s aspirations for European Union (EU) and NATO accession.
To mitigate the risk posed by TAG-70’s campaign, organizations should ensure that their Roundcube installations are patched and up-to-date, while actively hunting for indicators of compromise (IoCs) in their environments. The sophistication of TAG-70’s attack methods and its targeting of government and military entities underscore the need for robust cybersecurity measures and proactive threat intelligence efforts. The widespread nature of TAG-70’s activities and its potential impact on national security highlight the urgency for vigilance and preparedness among affected organizations and government agencies.
To read the entire analysis, click here to download the report as a PDF.
Appendix A — Indicators of Compromise
| Domains: bugiplaysec[.]com hitsbitsx[.]com ocsp-reloads[.]com recsecas[.]com IP Addresses: Malware Samples (SHA256): |
Appendix B — MITRE ATT&CK Techniques
| Tactic: Technique | ATT&CK Code |
| Initial Access: Phishing | T1583.001 |
| Execution: Exploitation for Client Execution | T1583.003 |
| Persistence: Valid Accounts | T1583.004 |
| Credential Access: Exploitation for Credential Access | T1566.002 |
| Credential Access: Input Capture | T1203 |
| Discovery: File and Directory Discovery | T1203 |
| Collection: Email Collection | T1203 |
| Command and Control: Non-Standard Port | T1203 |
Source: Original Post
“An interesting youtube video that may be related to the article above”