This article discusses the emergence of Deepseek, an AI-based application, and the subsequent rise in malware targeting its users through deceptive phishing tactics. It highlights how malicious actors create counterfeit websites and applications that mimic Deepseek, deceiving users into downloading malware. Affected: mobile users, cybersecurity sector
Keypoints :
- Deepseek is an advanced AI developed in China, with its first chatbot application due for release in January 2025.
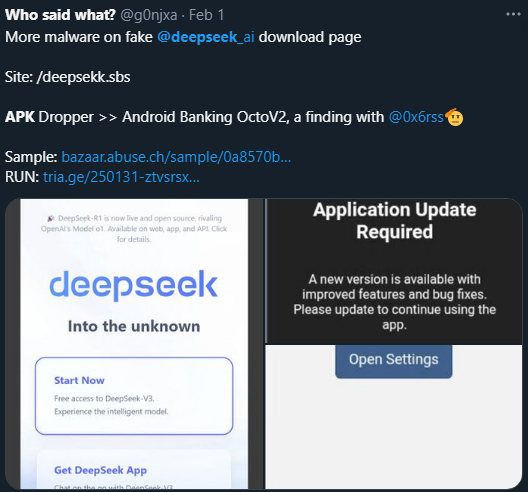
- Threat actors have created deceptive websites that look like Deepseek to trick users into downloading malicious software.
- The malware is delivered via a phishing link resembling the legitimate Deepseek platform.
- Once installed, the malware masquerades as the genuine Deepseek app icon.
- Users are manipulated into enabling permissions that can further compromise their devices.
- The malware employs a Domain Generation Algorithm (DGA) for Command and Control communication.
- K7 Labs advises users to protect their devices with reputable security software.
MITRE Techniques :
- Defense Evasion: Hide Artifacts – The malware disguises itself as the legitimate Deepseek app.
- Defense Evasion: Download New Code at Runtime – Malicious code is downloaded after the app installation.
- User Evasion: Input Injection – Users are tricked into enabling permissions for the malware.
- Privilege Escalation: Device Administrator Permissions – The malware requests device administration permissions.
- Discovery: Security Software Discovery – The malware retrieves information on installed applications.
- Collection: Input Capture – It captures user input for malicious use.
- Impact: Account Access Removal – The malware can potentially lock users out of accounts or devices.
- Impact: Data Encrypted for Impact – User data may be encrypted or rendered inaccessible.
Indicator of Compromise :
- [Package Name] com.vgsupervision_kit29
- [Package Name] com.hello.world
- [Hash] E1FF086B629CE744A7C8DBE6F3DB0F68
- [URL] hxxps://deepsekk[.]sbs/DeepSeek.apk
- [Hash] 99fe380d9ef96ddc4f71560eb8888c00
Full Story: https://labs.k7computing.com/index.php/android-banking-trojan-octov2-masquerading-as-deepseek-ai/