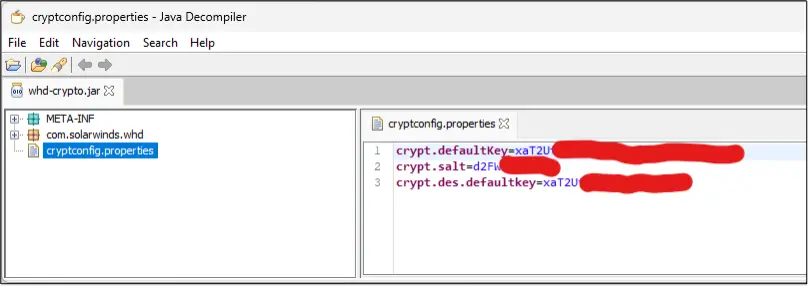
The NetSPI red team discovered a vulnerability in SolarWinds’ Web Help Desk software due to predictable encryption keys used to protect sensitive data, allowing attackers to easily decrypt stored passwords. SolarWinds has issued a patch and users are advised to upgrade and restrict access to backup files. Affected: SolarWinds Web Help Desk, sensitive data security
Keypoints :
- A predictable encryption key exposes sensitive data in SolarWinds’ Web Help Desk.
- The encryption method used is AES-GCM, which requires careful nonce management to ensure security.
- Decompilation of the Java application allows for the recovery of encryption keys and passwords.
- Backup files may contain various sensitive information, necessitating restricted access.
- SolarWinds issued a patch for the vulnerability.
MITRE Techniques :
- T1066: Indicator Removal on Host – The attacker may modify the backup files to remove IOCs.
- T1552: Unsecured Credentials – Weak keys allowing access to sensitive data and decryption of passwords.
- T1070: Indicator Removal on Host – Using decompilation techniques to identify vulnerabilities in the application.
Indicator of Compromise :
- Domain: solarwinds.com
- IP Address: Not explicitly stated
- URL: https://nvd.nist.gov/vuln/detail/CVE-2024-28989
- Hash: No specific hashes provided
- Email Address: Not explicitly stated