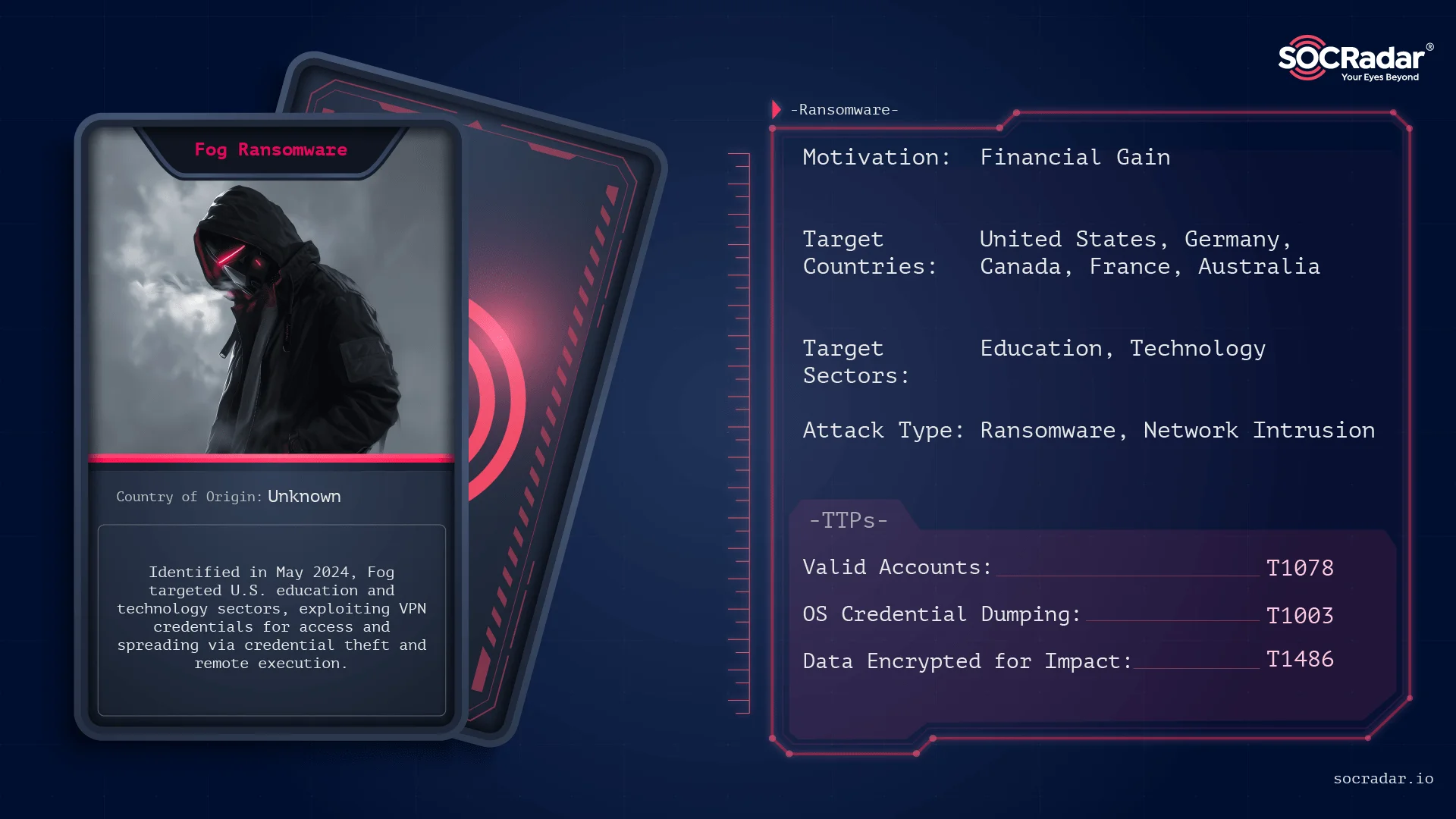
Fog Ransomware, detected in May 2024, primarily targets educational institutions in the US, employing a double extortion tactic. It utilizes a TOR-based data leak site to pressure victims into compliance by threatening to release stolen data if ransoms are not paid. The operational structure behind Fog remains unclear, emphasizing the model of varied affiliates over unified groups. Affected: educational institutions, business services, technology firms, government
Keypoints :
- Fog Ransomware emerged in April 2024 and was first seen in the wild in May 2024.
- Primarily targets US-based educational institutions, business services, and technology companies.
- Operates a double extortion model, leveraging ransomware and data theft.
- Utilizes a TOR-based data leak site to list victims and host stolen data.
- The US accounts for over 50% of recorded victims, with notable activity also in Germany, Australia, and Brazil.
- Employs various tactics and techniques for initial access, lateral movement, and data exfiltration.
- Organizations are encouraged to adopt proactive measures like MFA, EDR, and employee training to mitigate risks.
- SOCRadar offers tools and services to help detect and prevent ransomware attacks.
MITRE Techniques :
- Initial Access: Phishing (T1566) – Uses phishing emails to trick users into downloading malicious payloads.
- Initial Access: Exploitation of Public-Facing Apps (T1190) – Exploits vulnerabilities in internet-facing applications to gain access.
- Execution: Command and Scripting Interpreter (T1059) – Uses PowerShell or Bash scripts to execute malicious commands.
- Persistence: Scheduled Task/Job (T1053) – Creates scheduled tasks to maintain access after a reboot.
- Privilege Escalation: Abuse Elevation Control Mechanism (T1548) – Exploits vulnerabilities or misconfigurations to gain admin privileges.
- Defense Evasion: Obfuscated Files or Information (T1027) – Uses packing, encryption, or other methods to evade detection.
- Credential Access: Credential Dumping (T1003) – Uses tools like Mimikatz to steal credentials from memory.
- Discovery: System Information Discovery (T1082) – Gathers information about the infected system.
- Lateral Movement: Remote Services (RDP, SMB) (T1021) – Uses compromised credentials to move laterally within the network.
- Collection: Data from Local System (T1005) – Gathers sensitive files before exfiltration.
- Exfiltration: Exfiltration Over Web Service (T1567) – Sends stolen data to attacker-controlled servers.
- Impact: Data Encrypted for Impact (T1486) – Encrypts victim files and demands ransom for decryption.
Indicator of Compromise :
- URL http://malicious.com/path
- Domain fogransomware.com
- IP Address IPv4: 192.168.1.1
- Email Address attacker@example.com
- MD5: 7f6c3f2e244f243c1efe57a840945d24
Full Story: https://socradar.io/dark-web-profile-fog-ransomware/