The Sandworm APT group, linked to Russian military intelligence, has ramped up cyber-espionage attacks against Ukrainian organizations, focusing on critical infrastructure and state bodies since the full-scale invasion in 2022. The group employs trojanized Microsoft KMS activators and fake Windows updates to infect systems with various malware, including Dark Crystal RAT. Affected: Ukraine, critical infrastructure, state organizations
Keypoints :
- Sandworm APT (APT44) has consistently targeted Ukrainian organizations.
- Cyber-espionage campaign intensified post the full-scale invasion of Ukraine in 2022.
- The campaign utilizes trojanized KMS activation tools and fake Windows updates.
- Malware includes BACKORDER and Dark Crystal RAT, which steal sensitive data.
- Techniques include using a Trojanized ZIP file and a typosquatted domain for infection.
- Defenders can leverage SIGMA rules from the SOC Prime Platform to detect Sandworm activities.
- Evading detection is achieved by using Living Off the Land Binaries (LOLBINs) and disabling Windows Defender.
- New tools and malware iterations are consistently identified, showing an evolving attack strategy.
MITRE Techniques :
- Credential Dumping (T1003) – Exploits unauthorized copies of Microsoft office software to gain credentials.
- Command and Control (T1071) – Uses various backdoors to maintain C2 server connections.
- Malicious File Execution (T1203) – Distributes malware through trojanized files like KMS activators and fake updates.
- Persistence (T1547) – Maintains access by creating scheduled tasks via schtasks.exe.
- Defense Evasion (T1562) – Disables Windows Defender to bypass security protocols.
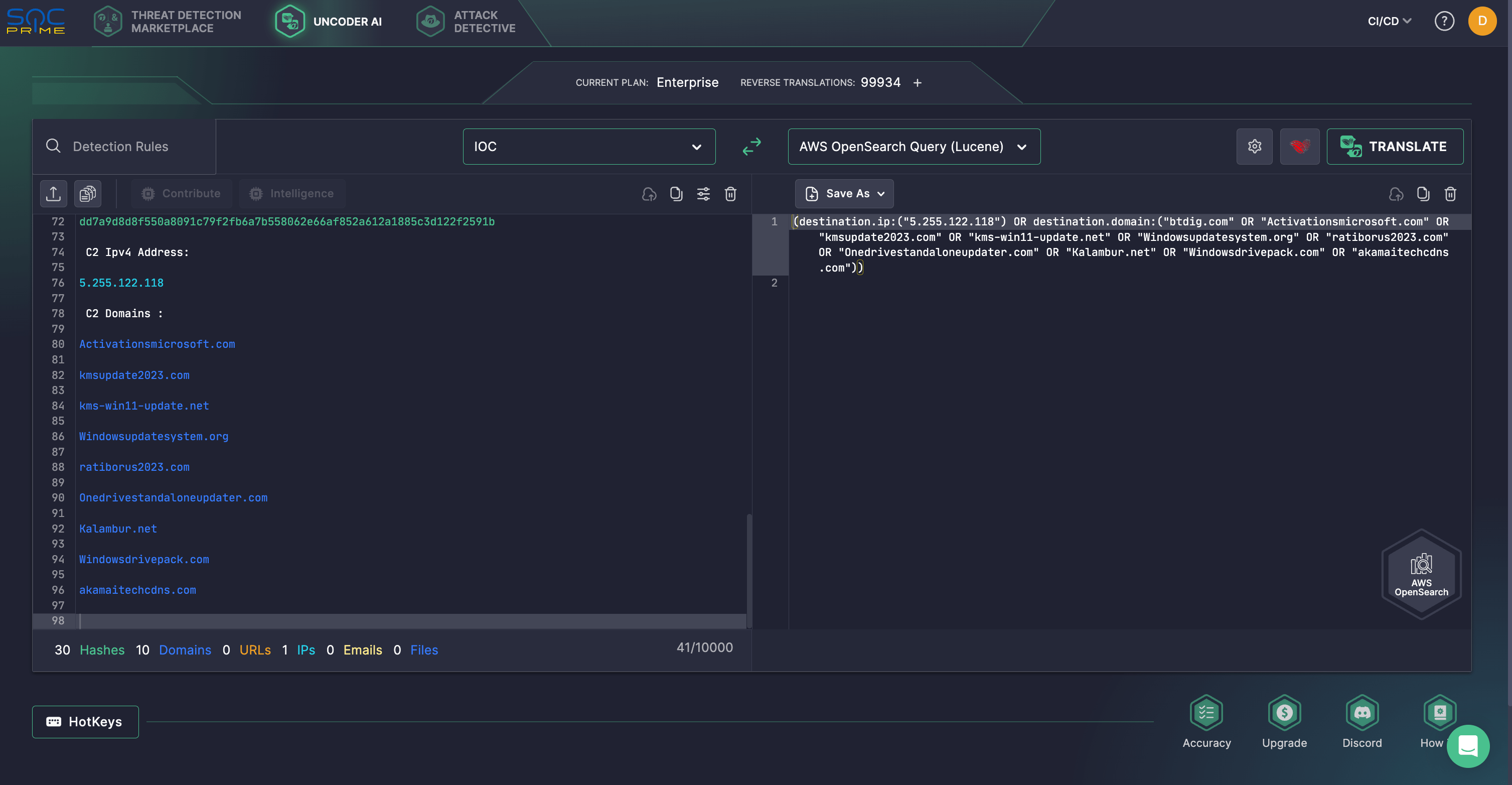
Indicator of Compromise :
- [File] KMSAuto++x64_v1.8.4.zip
- [Domain] kalambur[.]net
- [File] Runtime Broker.dll
- [File] kalambur2021_v39.exe
Full Story: https://socprime.com/blog/detect-sandworm-apt-attacks-against-ukraine/