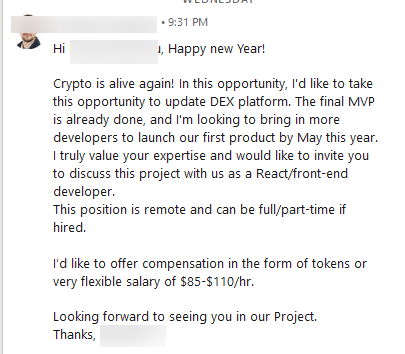
Bitdefender Labs alerts on a malicious campaign by the North Korean Lazarus Group, utilizing fake LinkedIn job offers to capture credentials and distribute malware. Victims are lured with enticing job proposals, leading to data harvesting and deployment of sophisticated malware targeting cryptocurrency wallets. Affected: LinkedIn, Cryptocurrency Sector, Various Organizations
Keypoints :
- The Lazarus Group is using fake LinkedIn job offers as a phishing tactic.
- Attackers target job seekers by proposing remote cryptocurrency-related positions.
- Harvesting of personal data occurs during the fake “hiring” process.
- The malware targets multiple operating systems including Windows, MacOS, and Linux.
- Information exfiltration is done through various methods including harvesting browser credentials and files.
- The malware has multiple components, including keyloggers and crypto miners.
- Victims could include individuals in sensitive sectors like aviation and defense.
- Users are advised to be vigilant and avoid running unverified code from dubious sources.
MITRE Techniques :
- T1071 – Application Layer Protocol: Data exfiltration occurs via HTTP and Tor protocols.
- T1041 – Exfiltration Over Command and Control Channel: Gathering sensitive data through established C2 channels.
- T1566 – Phishing: Fake job offers used to lure potential victims compelling them to share personal information.
- T1203 – Exploitation for Client Execution: Execution of JavaScript and Python scripts to deploy malware.
- T1204 – User Execution: Users unwittingly executing malicious codes by engaging with fake job applications.
Indicator of Compromise :
- [IP Address] 192.0.2.0
- [Filename] main99_65.py
- [Hash] 617205f5a241c2712d4d0a3b06ce3afd
- [URL] http://example[. ]com
- [Domain] malicious[. ]com