The ZDI team analyzes CVE-2025-0411, a zero-day vulnerability in 7-Zip, which was exploited in a SmokeLoader campaign targeting Ukrainian organizations through spear-phishing and homoglyph techniques. The vulnerability allows malicious files to bypass Windows security protections, escalating risks amid the Russo-Ukrainian conflict. Affected: Ukrainian organizations, cyberespionage sector
Keypoints :
- The Zero Day Initiative (ZDI) identified the exploitation of CVE-2025-0411 in September 2024.
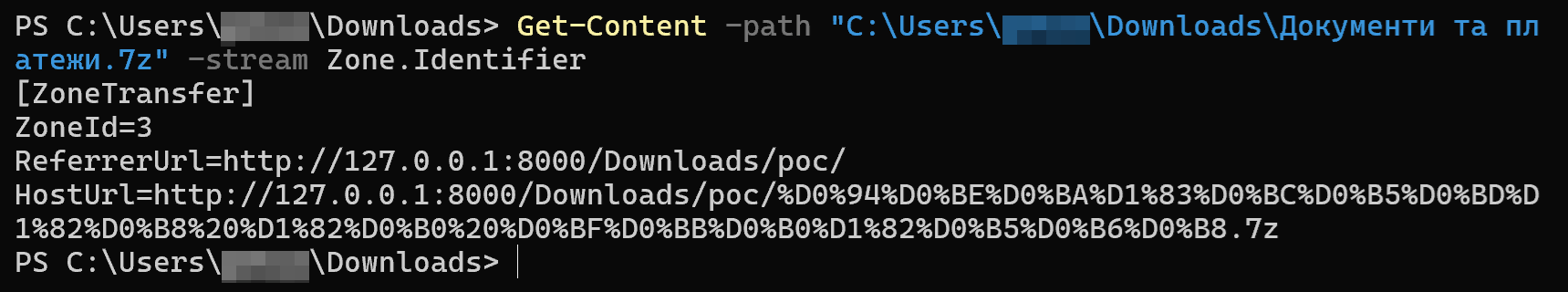
- CVE-2025-0411, a vulnerability in 7-Zip, allows bypassing Windows Mark-of-the-Web protections.
- The vulnerability was exploited by Russian cybercrime groups in a SmokeLoader campaign.
- Homoglyph attacks were used to spoof document extensions, tricking users into executing malicious files.
- A patch for the vulnerability was released in 7-Zip version 24.09 on November 30, 2024.
- Organizations are advised to update 7-Zip and implement rigorous email security measures.
- Several Ukrainian organizations and government entities were targeted during the campaign.
MITRE Techniques :
- Initial Access: Spearphishing Attachment (T1566.001) – Used to deliver malicious 7-Zip archives.
Indicator of Compromise :
- [SHA-256] ba74ecae43adc78efaee227a0d7170829b9036e5e7f602cf38f32715efa51826
- [SHA-256] 84ab6c3e1f2dc98cf4d5b8b739237570416bb82e2edaf078e9868663553c5412
- [SHA-256] 7786501e3666c1a5071c9c5e5a019e2bc86a1f169d469cc4bfef2fe339aaf384
- [SHA-256] a059d671d950abee93ef78a170d58a3839c2a465914ab3bd5411e39c89ae55a2
- [SHA-256] 888f68917f9250a0936fd66ea46b6c510d0f6a0ca351ee62774dd14268fe5420
Full Story: https://www.trendmicro.com/en_us/research/25/a/cve-2025-0411-ukrainian-organizations-targeted.html