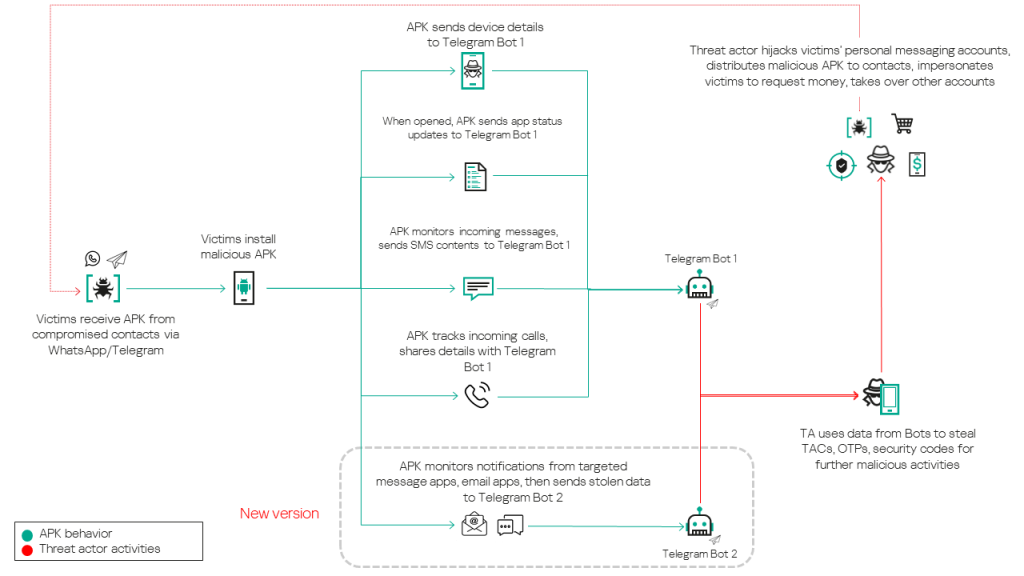
The article discusses a malicious Android campaign named “Tria Stealer” that targets users in Malaysia and Brunei through wedding invitation-themed social engineering tactics. The malware collects sensitive data, including SMS, call logs, and emails, and exfiltrates it to the threat actor via Telegram bots. It is believed that the campaign is operated by an Indonesian-speaking actor. Affected: Android, Telegram, WhatsApp
Keypoints :
- The “Tria Stealer” campaign began in mid-2024, primarily targeting users in Malaysia and Brunei.
- The malware collects SMS data, call logs, and messages from various apps.
- Data is exfiltrated to Telegram bots using the Telegram API.
- The threat actor impersonates victims to request money transfers from their contacts.
- Malware is distributed through messages inviting users to view wedding invitations.
- The campaign has been ongoing since March 2024, with multiple APK versions identified.
- The malware requests various permissions to access sensitive information on victims’ devices.
- Stolen data is used to hijack victims’ accounts on messaging platforms and other services.
- The threat actor is likely Indonesian-speaking, as evidenced by language artifacts found in the malware.
- Users are advised against installing apps from untrusted sources to mitigate risks.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: The malware uses Telegram API for communication with C2 servers.
- T1071.003 – Application Layer Protocol: The malware communicates with Telegram bots to exfiltrate data.
- T1083 – File and Directory Discovery: The malware collects information about the device brand and model.
- T1069 – Permission Groups: The malware requests permissions to access SMS and call logs.
- T1203 – Exploitation for Client Execution: The malware is distributed via social engineering tactics through messaging apps.
Indicator of Compromise :
- [file hash] daa30cd6699c187bb891448b89be1340
- [file hash] 162ed054914a8c71ad02126693c40997
- [file hash] 9698fa3e7e64272ff79c057e3b8be5d8
- [file hash] 9a0147d4c9d6ed3be82825ce35fdb4ee
- [file hash] e4da1332303b93f11d40787f7a79b917
- [file hash] 4ff2572a40300c0cce4327ec34259902
Full Research: https://securelist.com/tria-stealer-collects-sms-data-from-android-devices/115295/