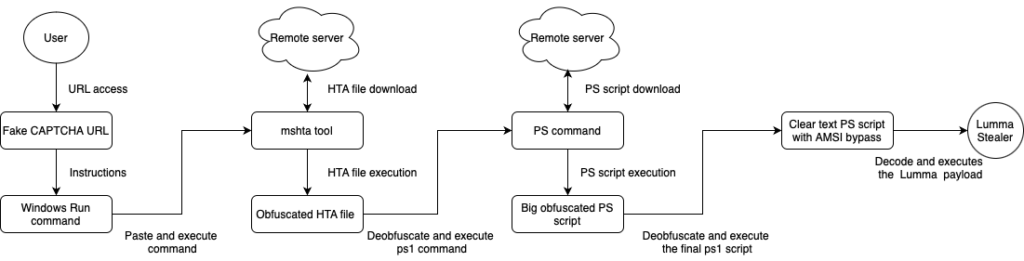
A new malware campaign has emerged, utilizing fake CAPTCHAs to deliver Lumma Stealer, a malware operating under the malware-as-a-service (MaaS) model. This global campaign targets various industries, with a focus on telecom, and employs multiple infection techniques. The attackers use social engineering tactics to trick victims into executing commands that lead to malware installation. Affected: Windows
Keypoints :
- Netskope Threat Labs identified a new Lumma Stealer campaign using fake CAPTCHAs.
- The campaign targets victims globally, including countries like Argentina, Colombia, and the United States.
- Multiple industries are affected, with the telecom sector being the most targeted.
- Attackers deliver Lumma via cracked software, Discord CDN, and fake CAPTCHA pages.
- Infection techniques include process hollowing and PowerShell one-liners.
- Fake CAPTCHAs instruct victims to run commands that facilitate malware installation.
- The malware employs evasion techniques to bypass security controls.
- Netskope has observed new payloads and malvertising websites in this campaign.
MITRE Techniques :
- Process Hollowing (T1091): Attackers use process hollowing to inject malware into legitimate processes.
- PowerShell (T1059.001): PowerShell is used to execute commands and download additional payloads.
- Masquerading (T1036): Fake CAPTCHA pages are used to trick victims into executing commands.
- Exploitation of Trusted Relationships (T1199): The use of mshta.exe to download and execute HTA files from remote servers.
- Bypass User Account Control (UAC) (T1088): The malware circumvents UAC by executing commands outside the browser context.
Indicator of Compromise :
- [url] h3.errantrefrainundocked.shop
- [file name] riii2.aspx
- [file hash] Trojan.GenericKD.75371630
- [file hash] Trojan.GenericKD.75345562
- [file hash] Trojan.Generic.37229350
- Check the article for all found IoCs.
Full Research: https://www.netskope.com/blog/lumma-stealer-fake-captchas-new-techniques-to-evade-detection