Recent reports indicate unauthorized access in Japan, primarily using LinkedIn as an infection vector. The Lazarus attack group has been identified as responsible for these attacks, which have targeted organizations since 2019. Recommendations include restricting the use of social networking services on work devices. Affected: LinkedIn, Bitcoin.DMM.com
Keypoints :
- Unauthorized access incidents in Japan linked to LinkedIn.
- Lazarus attack group exploits LinkedIn for cyber attacks.
- Recommendations include restricting SNS use on work devices.
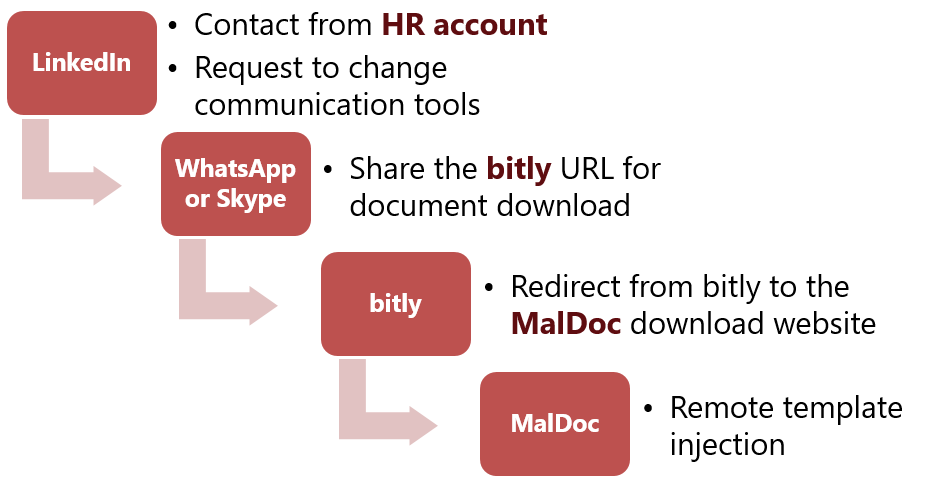
- Three specific operations by the Lazarus group are detailed: Dream Job, Dangerous Password, and AppleJeus.
- Attackers often impersonate recruiters and request file downloads.
- Use of legitimate LinkedIn accounts by attackers complicates detection.
MITRE Techniques :
- Initial Access (T1071.001) – Exploiting LinkedIn to contact targets and lure them into downloading malicious files.
- Credential Dumping (T1003) – Hijacking legitimate LinkedIn accounts to gain access to targeted organizations.
- Execution (T1203) – Encouraging victims to execute malicious documents or files received through LinkedIn.
- Command and Control (T1071) – Utilizing Telegram for command and control after initial contact via LinkedIn.
Indicator of Compromise :
- No IoCs found
Full Research: https://blogs.jpcert.or.jp/en/2025/01/initial_attack_vector.html