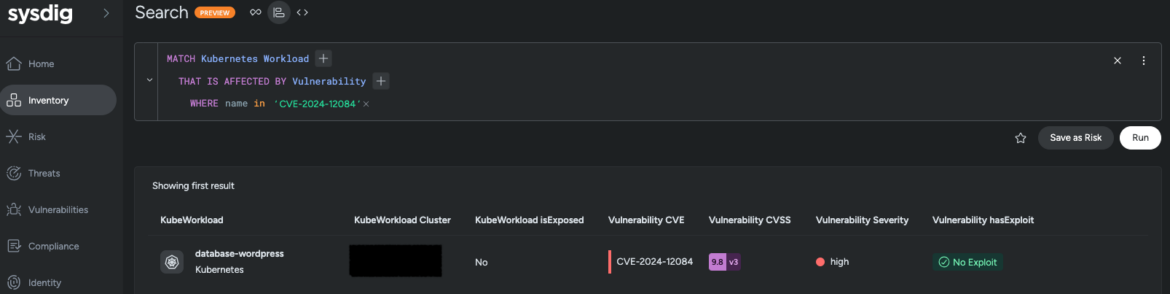
On January 14, 2025, multiple vulnerabilities were discovered in the rsync utility, with CVE-2024-12084 being the most critical as it allows for remote code execution. This article discusses detection and mitigation strategies for this vulnerability. Affected: rsync
Keypoints :
- Six vulnerabilities were announced affecting the rsync utility.
- CVE-2024-12084 has a CVSS score of 9.8, indicating a severe heap overflow vulnerability.
- Other vulnerabilities include CVE-2024-12085 (information leak), CVE-2024-12086 (information leak), CVE-2024-12087 (path traversal), CVE-2024-12088 (path traversal), and CVE-2024-12747 (symbolic link race condition).
- Rsync is commonly used for file transfers and can operate as a daemon on TCP port 873.
- Detection of CVE-2024-12084 involves monitoring for unusual command executions by rsync processes.
- Sysdig Secure can help identify affected workloads and respond to potential exploitation.
- Immediate patching to rsync version 3.4.0 is recommended to remediate the vulnerabilities.
MITRE Techniques :
- Execution (T1203): Exploitation for client execution through unexpected command execution in rsync.
Indicator of Compromise :
- [file name] rsync
- [file name] rsyncd
- [others ioc] TCP port 873
- [others ioc] heap overflow
- Check the article for all found IoCs.
Full Research: https://sysdig.com/blog/detecting-and-mitigating-cve-2024-12084-rsync-remote-code-execution/