Ivanti has issued a security advisory regarding two critical vulnerabilities (CVE-2025-0282 and CVE-2025-0283) affecting its Connect Secure, Policy Secure, and ZTA gateway products. CVE-2025-0282 allows remote code execution by unauthenticated attackers, while CVE-2025-0283 enables local privilege escalation for authenticated users. The article discusses observed attacks exploiting CVE-2025-0282, detailing attack phases and tools used. Affected: Ivanti Connect Secure, Ivanti Policy Secure, Ivanti ZTA gateway
Keypoints :
- Ivanti released a security advisory on Jan. 8, 2025, for CVE-2025-0282 and CVE-2025-0283.
- CVE-2025-0282 is a critical buffer overflow vulnerability allowing remote code execution.
- CVE-2025-0283 is a high-severity buffer overflow allowing local privilege escalation.
- Attacks exploiting CVE-2025-0282 have been observed in the wild.
- Palo Alto Networks offers protections against these vulnerabilities through its products.
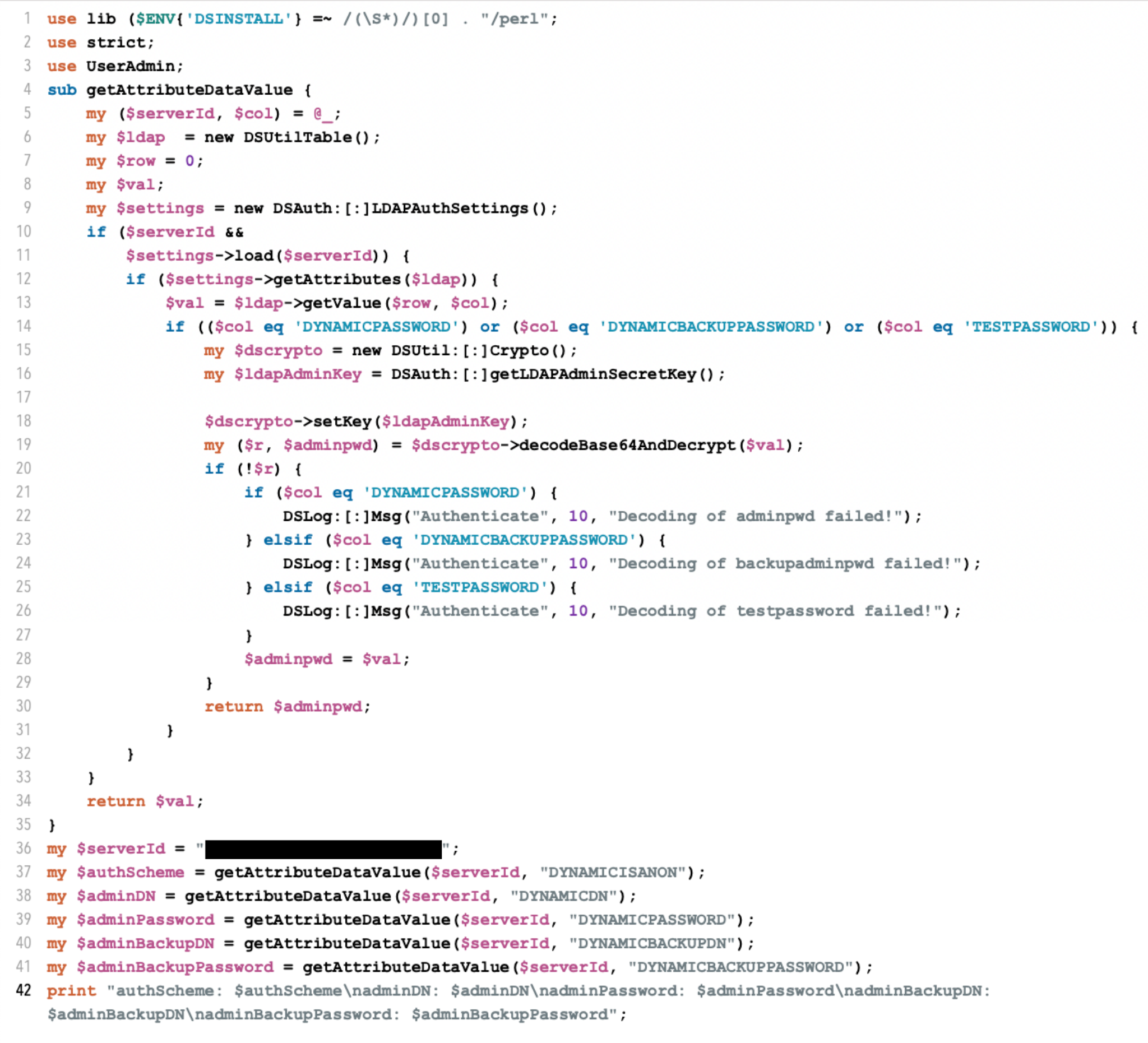
- Attack phases include initial access, credential harvesting, defense evasion, and persistence.
- Specific tools used in the attacks include a custom Perl script and memory dumping tools.
- Ivanti recommends applying patches and monitoring for suspicious activities.
MITRE Techniques :
- Initial Access (T1190) – Exploitation of CVE-2025-0282 for remote code execution.
- Credential Dumping (T1003) – Use of ldap.pl to harvest credentials.
- Lateral Movement (T1021) – Use of RDP to move laterally within the network.
- Defense Evasion (T1070) – Deletion of log files to cover tracks.
- Persistence (T1543) – Creation of scheduled tasks and services for maintaining access.
Indicator of Compromise :
- [IP Address] 185.219.141[.]95 – Nord VPN node observed in debug log file
- [IP Address] 185.195.71[.]244 – Tor exit node observed in debug log file
- [IP Address] 193.149.180[.]128 – C2 address
- [IP Address] 168.100.8[.]144 – C2 address
- [File Hash] 7144B8C77D261985205AE2621EB6242F43D6244E18B8D01D05048337346B6EFD – ldap.pl file
- Check the article for all found IoCs.
close with
Full Research: https://unit42.paloaltonetworks.com/threat-brief-ivanti-cve-2025-0282-cve-2025-0283/