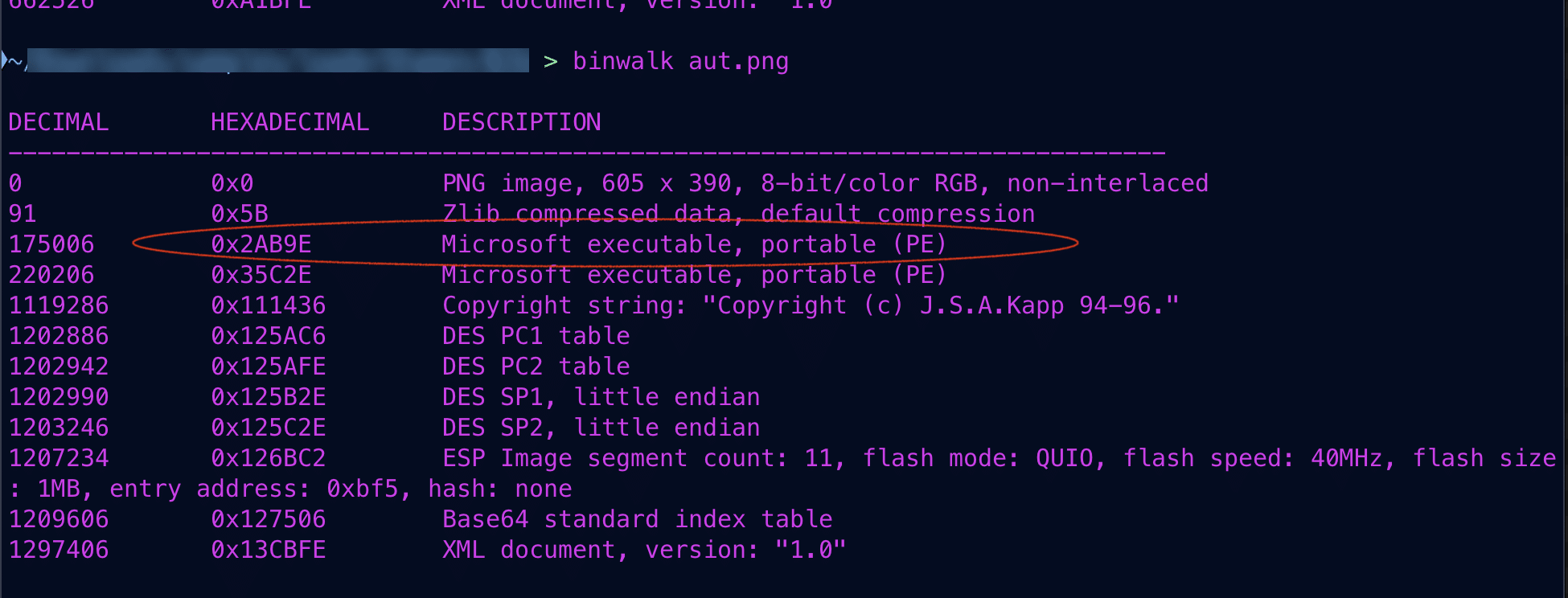
A series of sophisticated cyberattacks targeting organizations in Chinese-speaking regions have been identified, utilizing a multi-stage loader called PNGPlug to deliver the ValleyRAT malware. The attacks begin with phishing tactics, leading to the installation of a malicious MSI package that deploys the malware while maintaining a facade of legitimacy. Affected: Chinese-speaking organizations, Hong Kong, Taiwan, China
Keypoints :
- Attacks are targeting organizations in Hong Kong, Taiwan, and China.
- Utilizes a multi-stage loader named PNGPlug to deliver the ValleyRAT payload.
- The attack begins with a phishing webpage prompting victims to download a malicious MSI package.
- The MSI package executes benign applications while extracting an encrypted malware payload.
- PNGPlug loader patches ntdll.dll for memory injection and checks for antivirus software.
- ValleyRAT malware employs advanced techniques such as shellcode execution, obfuscation, and persistence mechanisms.
- Attribution of the campaign is linked to the Silver Fox APT group.
- Highlights operational gaps in cybersecurity measures among targeted organizations.
- Attackers use legitimate software as a delivery mechanism for malware.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: The loader communicates with the command-and-control (C2) server to fetch additional malicious components.
- T1203 – Exploitation for Client Execution: The attack exploits users through a phishing webpage to download a malicious MSI package.
- T1059.001 – Command and Scripting Interpreter: The loader runs commands to inject malicious payloads into memory.
- T1027 – Obfuscated Files or Information: The use of .png file extensions conceals the malicious payloads.
- T1547.001 – Boot or Logon Autostart Execution: The loader modifies the registry to maintain persistence.
Indicator of Compromise :
- [IP Address] 156.247.33[.]53
- [File Hash] 08dad42da5aba6ef48fca27c783f78f06ab9ea7a933420e4b6b21e12e550dd7d
- [File Hash] 33bc111238a0c6f10f6fe3288b5d4efe246c20efd8d85b4fe88f7d602d70738e
- [File Hash] 50a64e97c6a5417023f3561f33291b448ce830a4d99c40356af67301c8fa7523
- [File Hash] 45.195.148[.]107
- Check the article for all found IoCs.
Full Research: https://intezer.com/blog/malware-analysis/weaponized-software-targets-chinese/