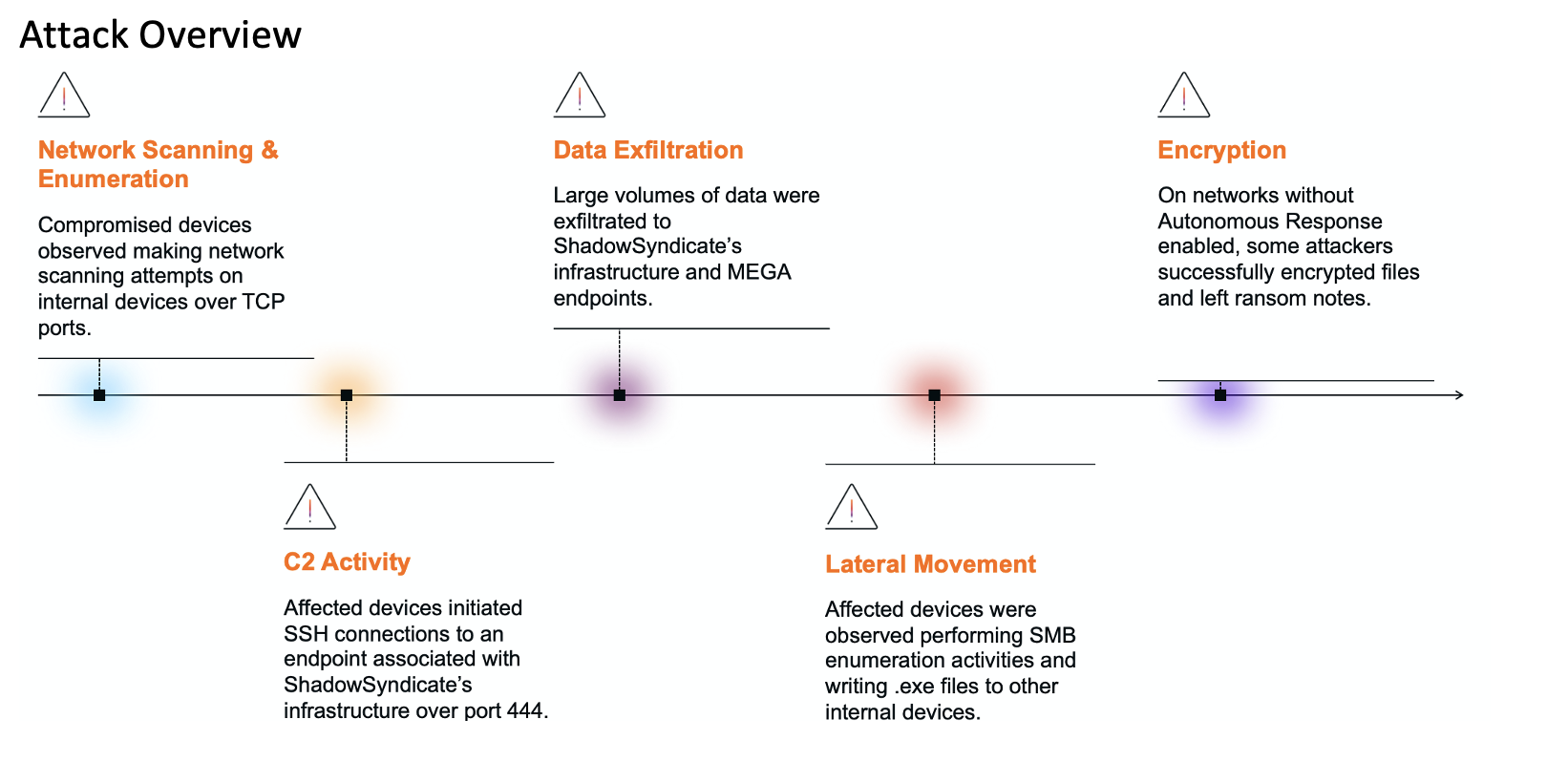
Darktrace’s investigation into RansomHub attacks revealed connections to the ShadowSyndicate threat group, which has been active since July 2022. ShadowSyndicate has adopted RansomHub’s ransomware services, leading to a surge in attacks across various sectors in late 2024. The attacks involved complex tactics, including data exfiltration and file encryption, with ransom notes threatening data leaks. Affected: Darktrace customer networks, RansomHub, ShadowSyndicate
Keypoints :
- Darktrace investigated RansomHub attacks between September and October 2024.
- ShadowSyndicate is a threat actor linked to multiple ransomware families since July 2022.
- RansomHub emerged as a Ransomware-as-a-Service (RaaS) operator post-FBI takedown of ALPHV/BlackCat.
- ShadowSyndicate has integrated RansomHub into its operations, leveraging its ransomware in recent attacks.
- Data exfiltration and file encryption were key tactics in the observed attacks.
- Ransom notes followed a specific naming pattern and threatened data leaks if ransoms were not paid.
- Darktrace’s analysis identified multiple incidents across different sectors, including education and manufacturing.
MITRE Techniques :
- RECONNAISSANCE – T1592.004 Client Configurations: Gathering information about client systems.
- RECONNAISSANCE – T1590.005 IP Addresses: Identifying IP addresses for potential targets.
- RECONNAISSANCE – T1595.001 Scanning IP Blocks: Scanning for active IP addresses.
- RECONNAISSANCE – T1595.002 Vulnerability Scanning: Identifying vulnerabilities in systems.
- DISCOVERY – T1046 Network Service Scanning: Scanning for active services on the network.
- DISCOVERY – T1018 Remote System Discovery: Identifying remote systems within the network.
- DISCOVERY – T1083 File and Directory Discovery: Locating files and directories on systems.
- INITIAL ACCESS – T1189 Drive-by Compromise: Gaining access through compromised websites.
- INITIAL ACCESS – T1190 Exploit Public-Facing Application: Exploiting vulnerabilities in public-facing applications.
- COMMAND AND CONTROL – T1001 Data Obfuscation: Hiding data to evade detection.
- COMMAND AND CONTROL – T1071 Application Layer Protocol: Using application layer protocols for communication.
- COMMAND AND CONTROL – T1071.001 Web Protocols: Leveraging web protocols for command and control.
- COMMAND AND CONTROL – T1573.001 Symmetric Cryptography: Using cryptography for secure communications.
- COMMAND AND CONTROL – T1571 Non-Standard Port: Utilizing non-standard ports for communication.
- DEFENSE EVASION – T1078 Valid Accounts: Using valid accounts to bypass security measures.
- DEFENSE EVASION – T1550.002 Pass the Hash: Exploiting hashed credentials for access.
- LATERAL MOVEMENT – T1021.004 SSH: Using SSH for lateral movement within the network.
- LATERAL MOVEMENT – T1080 Taint Shared Content: Manipulating shared content for lateral movement.
- LATERAL MOVEMENT – T1570 Lateral Tool Transfer: Transferring tools laterally within the network.
- LATERAL MOVEMENT – T1021.002 SMB/Windows Admin Shares: Utilizing SMB for lateral movement.
- COLLECTION – T1185 Man in the Browser: Intercepting data within the browser.
- EXFILTRATION – T1041 Exfiltration Over C2 Channel: Exfiltrating data through command and control channels.
- EXFILTRATION – T1567.002 Exfiltration to Cloud Storage: Sending data to cloud storage services.
- EXFILTRATION – T1029 Scheduled Transfer: Scheduling data transfers for exfiltration.
- IMPACT – T1486 Data Encrypted for Impact: Encrypting data to extort victims.
Indicator of Compromise :
- [IP] 83.97.73[.]198
- [IP] 108.181.182[.]143
- [IP] 46.161.27[.]151
- [IP] 185.65.212[.]164
- [IP] 66[.]203.125.21
- Check the article for all found IoCs.
Full Research: https://darktrace.com/blog/ransomhub-ransomware-darktraces-investigation-of-the-newest-tool-in-shadowsyndicates-arsenal