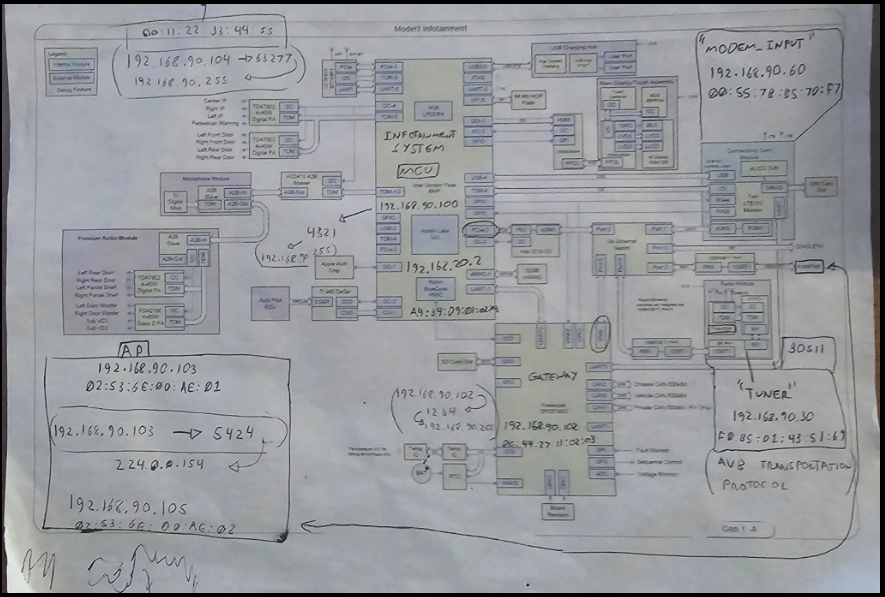
This article discusses the exploration of vulnerabilities in the Tesla Model 3, detailing various methods and tools used for testing, including attempts at exploiting USB ports, LTE connectivity, and GPS spoofing. The author shares insights from their research journey, highlighting both successes and failures in identifying potential security flaws. Affected: Tesla Model 3
Keypoints :
- The research aims to find vulnerabilities in the Tesla Model 3.
- Initial research involved studying past successful Tesla hackers.
- USB ports were tested for data connectivity to the Infotainment System.
- Attempts to exploit WiFi and LTE connectivity yielded no significant results.
- GPS spoofing was identified as a potential vulnerability using a rooted Android device.
- The Denial of Service vulnerability was found in the browser interface of the Tesla Model 3.
- Collaboration with Tesla led to the resolution of the identified vulnerabilities.
MITRE Techniques :
- Denial of Service (T1499) – Exploiting the browser interface to crash the entire Tesla Model 3 interface.
- Credential Dumping (T1003) – Spoofing GPS coordinates to gain unauthorized access to vehicle functions.
Indicator of Compromise :
- [url] https://owner-api.teslamotors.com/
- [url] https://github.com/nullze/Tesla-Tester/blob/master/tesla-tester.py
- [IoC Category] CVE-2020–10558
- [IoC Category] CVE-2022–27948
- Check the article for all found IoCs.
Views: 1