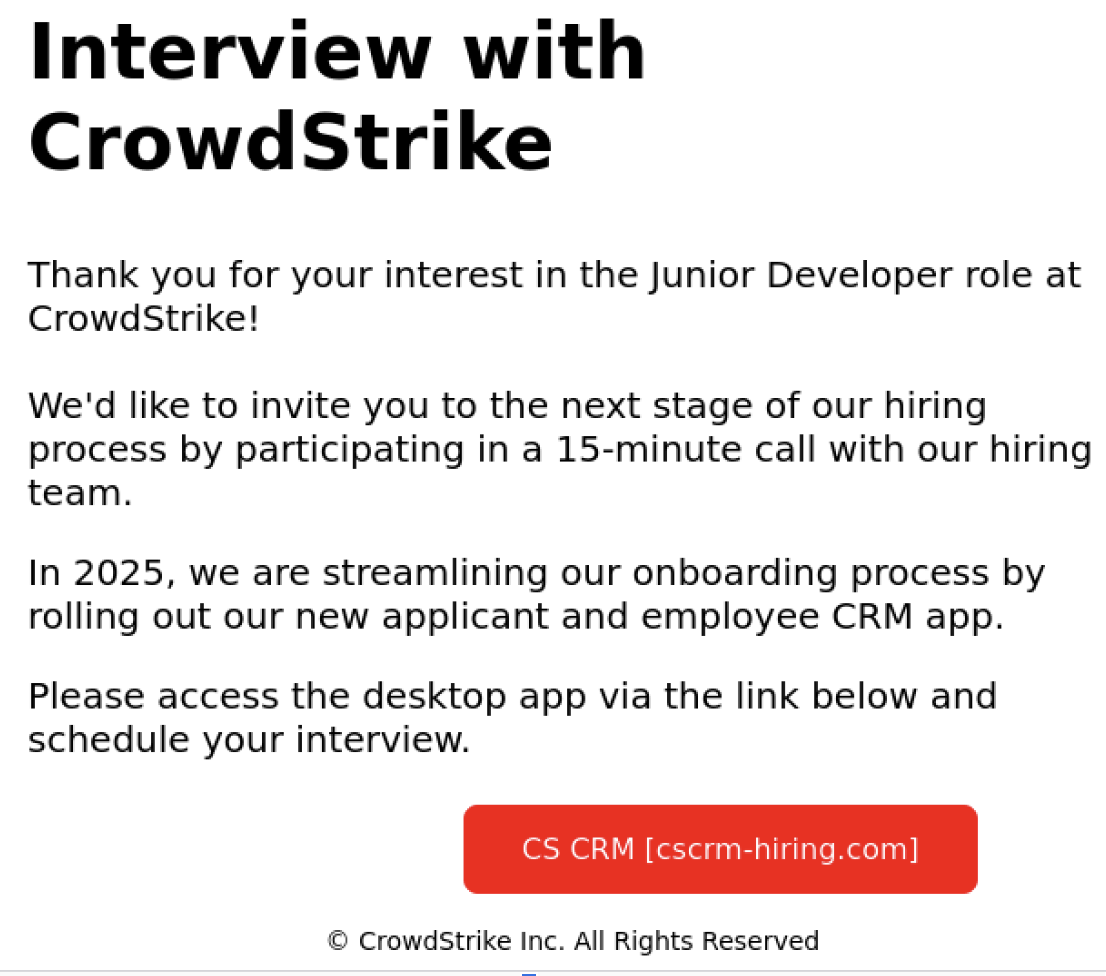
CrowdStrike has identified a phishing campaign that exploits its recruitment branding to deliver malware disguised as a fake employee CRM application. The attack involves a phishing email directing victims to a malicious site where they download a Windows executable that serves as a downloader for the cryptominer XMRig. Affected: cscrm-hiring.com
Keypoints :
- The phishing campaign impersonates CrowdStrike recruitment to lure job seekers.
- Victims are directed to a malicious website to download a fake application.
- The downloaded executable performs environment checks to avoid detection.
- XMRig is downloaded and executed as a cryptominer on the victim’s machine.
- The malware establishes persistence through registry entries and batch scripts.
- Individuals should verify the authenticity of recruitment communications from CrowdStrike.
- Organizations are advised to educate employees on phishing tactics.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: The malware communicates with a mining pool using HTTP.
- T1203 – Exploitation for Client Execution: The phishing email exploits user trust to execute malware.
- T1059.003 – Command and Scripting Interpreter: The malware uses a batch script for persistence.
- T1547.001 – Boot or Logon Autostart Execution: The malware creates a registry entry for persistence.
- T1027 – Obfuscated Files or Information: The executable performs environment checks to evade detection.
Indicator of Compromise :
- [domain] cscrm-hiring[.]com
- [url] https[:]//cscrm-hiring[.]com/cs-applicant-crm-installer[.]zip
- [ip address] 93.115.172[.]41
- [file hash] 96558bd6be9bcd8d25aed03b996db893ed7563cf10304dffe6423905772bbfa1
- [file hash] 62f3a21db99bcd45371ca4845c7296af81ce3ff6f0adcaee3f1698317dd4898b
- Check the article for all found IoCs.
Full Research: https://www.crowdstrike.com/en-us/blog/recruitment-phishing-scam-imitates-crowdstrike-hiring-process/