WordPress has become a popular platform for building websites, including those of governmental entities. This article explores the existence of Indonesian government websites that are built using WordPress but are not properly maintained. We will delve into how Google dorks can be used to identify these sites, the idea for assessing the WordPress versions, and the implications for security vulnerabilities.
Finding Unmaintained Government Websites
By employing a Google dorking technique, we can uncover Indonesian government websites using the domain extension “.go.id” that have been constructed with WordPress. The specific Google search query used is:
site:.go.id inurl:wp-content
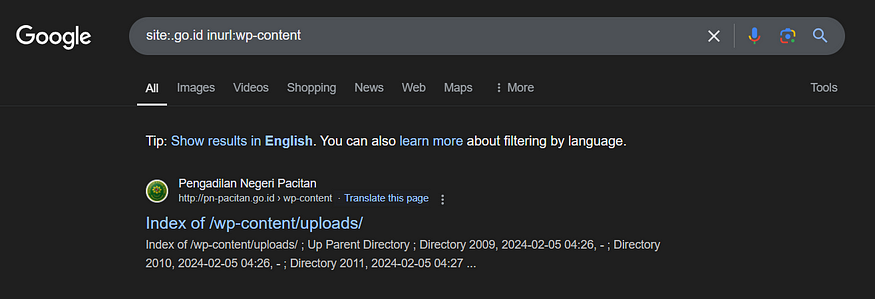
This query targets government websites in Indonesia and filters results to show only those that contain “wp-content” in their URLs — a common directory in WordPress installations. Discovering such URLs can provide insight into websites potentially lacking regular updates or maintenance.
Consolidate Results
To facilitate the analysis of search results, I developed a Chrome plugin that aggregates the links returned by Google searches. This tool makes it easier to compile a list WordPress sites.

Checking WordPress Versions through Source Code
A simple yet effective method for quickly identifying the version of WordPress used on a site is by inspecting the web page’s source code. Specifically, we look for the following meta tag:
<meta name="generator" content="WordPress 6.7.1">

Finding this tag provides immediate information regarding the version of WordPress in use. However, it is important to note that this method may not work for all WordPress installations. Some websites may choose to obfuscate this information for security reasons, or they may have removed the tag entirely, making it impossible to ascertain the version directly from the source code.
Developing a Tool for Version Checking
To streamline the process of checking WordPress versions and the plugins they use, I developed a tool based on previous information (Tag for Version Checking). This tool allows me to efficiently gather information on the WordPress core version. By doing so, we can quickly assess vulnerabilities associated with these plugins.

Examples of Outdated WordPress Sites
The findings from utilizing the aforementioned methods reveal several Indonesian government websites still operating on outdated versions of WordPress. Notably:
- https://lldikti3.kemdikbud.go.id — WordPress Version: 6.5.5
- https://bpkad.cilacapkab.go.id — WordPress Version: 6.4.5
- https://disperkim.tegalkab.go.id — WordPress Version: 5.3.2
The presence of outdated WordPress installations, particularly those running versions as old as 5.x, raises serious security concerns. Older versions are more susceptible to known vulnerabilities, making them prime targets for cyberattacks.
Assessing Vulnerabilities with WPScan
To further investigate potential security weaknesses in these sites, we can utilize resources like WPScan. This tool provides comprehensive information about vulnerabilities associated with specific WordPress versions and plugins. By checking the identified sites against the WPScan database, we can determine their vulnerability status and understand the risks they present.

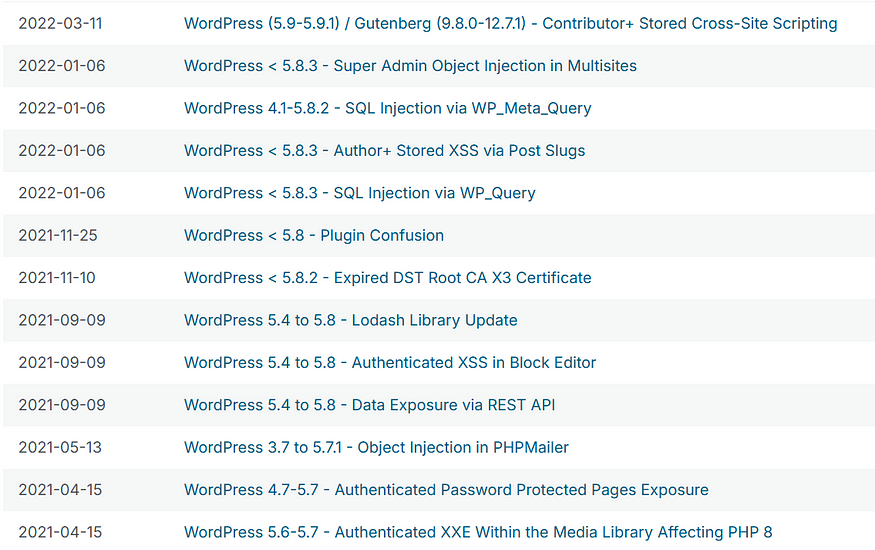
Analysis of Vulnerabilities Detected on the Website https://disperkim.tegalkab.go.id
After running a detailed security scan using WPScan on the government website https://disperkim.tegalkab.go.id, we discovered a total of 51 vulnerabilities within the WordPress installation and its associated themes and plugins.

Below, iprovide an overview of the most critical vulnerabilities and potential impacts.
Critical Vulnerabilities Descriptions and Impacts
- WordPress < 5.4.1 — Password Reset Tokens Failed to Be Properly Invalidated: Password reset tokens were not properly invalidated after use, which could allow attackers to reuse previously issued tokens and gain unauthorized access to user accounts.
- WordPress < 5.4.1 — Unauthenticated Users Can View Private Posts: This vulnerability allows unauthenticated users to access private or unpublished posts by exploiting specific endpoints, leading to unauthorized exposure of sensitive content.
- WordPress < 5.4.1 — Authenticated Cross-Site Scripting (XSS) in Customizer: Authenticated users with low privileges can inject malicious scripts into the WordPress Customizer, potentially compromising the site or stealing sensitive data from other users.
- WordPress < 5.4.2 — Authenticated XSS in Block Editor: Low-privilege authenticated users can exploit the Block Editor to inject and execute arbitrary JavaScript, enabling attacks such as session hijacking or unauthorized actions.
- WordPress < 5.4.2 — Authenticated Stored XSS via Theme Upload: A vulnerability where authenticated users with theme upload permissions can inject persistent malicious scripts into the site, potentially compromising admin accounts.
- WordPress < 5.8.2 — SQL Injection via WP_Query: Improper sanitization in WP_Query allows attackers to inject SQL commands, leading to database manipulation, data leakage, or complete site compromise.
- WordPress < 5.8 — Plugin Confusion: This issue involves mismanagement of plugins where attackers could exploit name collisions or mismatches to execute unauthorized code.
- WordPress 3.7 to 5.7.1 — Object Injection in PHPMailer: The PHPMailer component was susceptible to object injection attacks, which could be used to execute arbitrary code or escalate privileges within the server environment.
- WordPress < 5.4.2 — Open Redirection: Improper validation of URLs in some WordPress endpoints allows attackers to redirect users to malicious websites, potentially leading to phishing or malware installation.
- WordPress < 5.8.2 — Expired DST Root CA X3 Certificate: An expired certificate issue could cause connection failures to certain services, impacting site functionality and potentially exposing sensitive data due to fallback mechanisms.
Next Check Exploit Database
After identifying the vulnerabilities, we can check the Exploit Database to see if there are any available exploits that we can use. This step is crucial as it allows us to assess the risk level associated with each vulnerability. By reviewing the database, we can determine whether an exploit has been documented and if it can be leveraged against the specific vulnerabilities found.
For an example:

Views: 0