### #PhishingInnovation #EmailSecurityBypass #CorruptedFilesAttack
Summary: A new phishing campaign exploits Microsoft’s Word file recovery feature by sending corrupted documents as email attachments, enabling them to evade security software while still being recoverable by users. This tactic aims to trick recipients into providing their credentials through a QR code linked to a phishing site.
Threat Actor: Unknown | unknown
Victim: Various Organizations | various organizations
Key Point :
- Phishing emails use corrupted Word documents that appear to be from payroll and HR departments.
- Attachments contain themes related to employee benefits and bonuses, enticing users to open them.
- When opened, Word reports the files as corrupted, prompting users to recover the content.
- The recovered document instructs users to scan a QR code, leading to a phishing site mimicking Microsoft login.
- Most antivirus solutions fail to detect these corrupted files, allowing the phishing attack to succeed.
- Users are advised to delete suspicious emails and confirm with network admins before opening attachments.

A novel phishing attack abuses Microsoft’s Word file recovery feature by sending corrupted Word documents as email attachments, allowing them to bypass security software due to their damaged state but still be recoverable by the application.
Threat actors constantly look for new ways to bypass email security software and land their phishing emails in targets’ inboxes.
A new phishing campaign discovered by malware hunting firm Any.Run utilizes intentionally corrupted Word documents as attachments in emails that pretend to be from payroll and human resources departments.
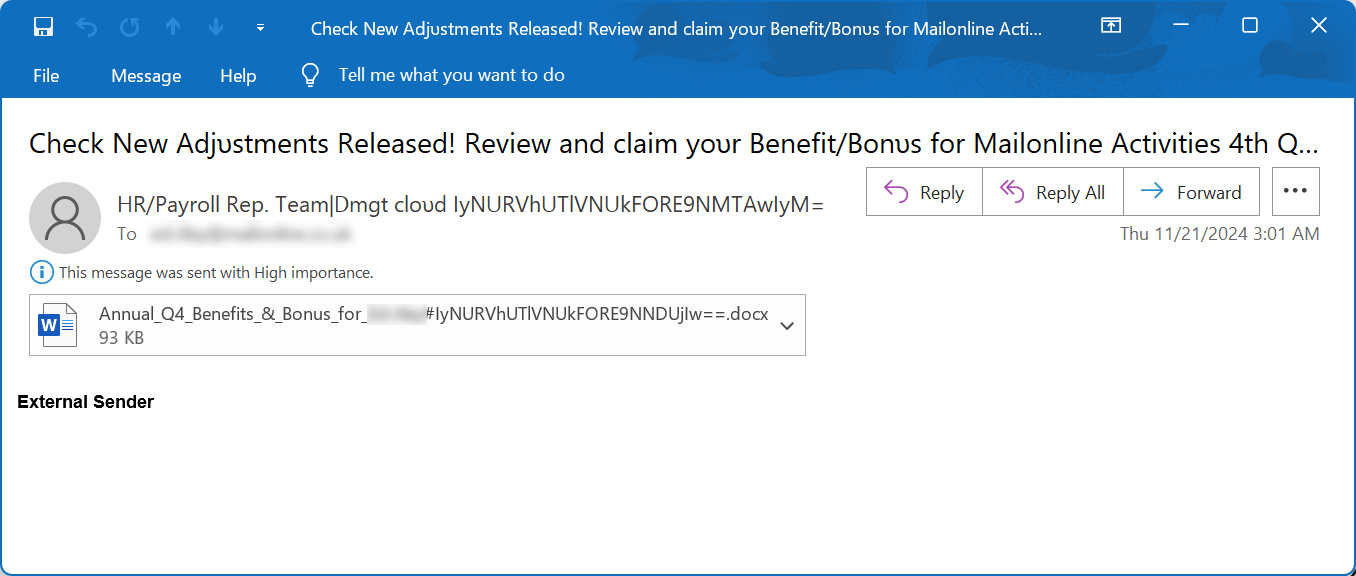
Source: BleepingComputer
These attachments use a wide range of themes, all revolving around employee benefits and bonuses, including:
Annual_Benefits_&_Bonus_for_[name]_IyNURVhUTlVNUkFORE9NNDUjIw__.docx
Annual_Q4_Benefits_&_Bonus_for_[name]_IyNURVhUTlVNUkFORE9NNDUjIw__.docx.bin
Benefits_&_Bonus_for_[name]_IyNURVhUTlVNUkFORE9NNDUjIw__.docx.bin
Due_&_Payment_for_[name]_IyNURVhUTlVNUkFORE9NNDUjIw__.docx.bin
Q4_Benefits_&_Bonus_for_[name]_IyNURVhUTlVNUkFORE9NNDUjIw__.docx.bin
The documents in this campaign all include the base64 encoded string “IyNURVhUTlVNUkFORE9NNDUjIw,” which decodes to “##TEXTNUMRANDOM45##”.
When opening the attachments, Word will detect that the file is corrupted and state that it “found unreadable content” in the file, asking if you wish to recover it.
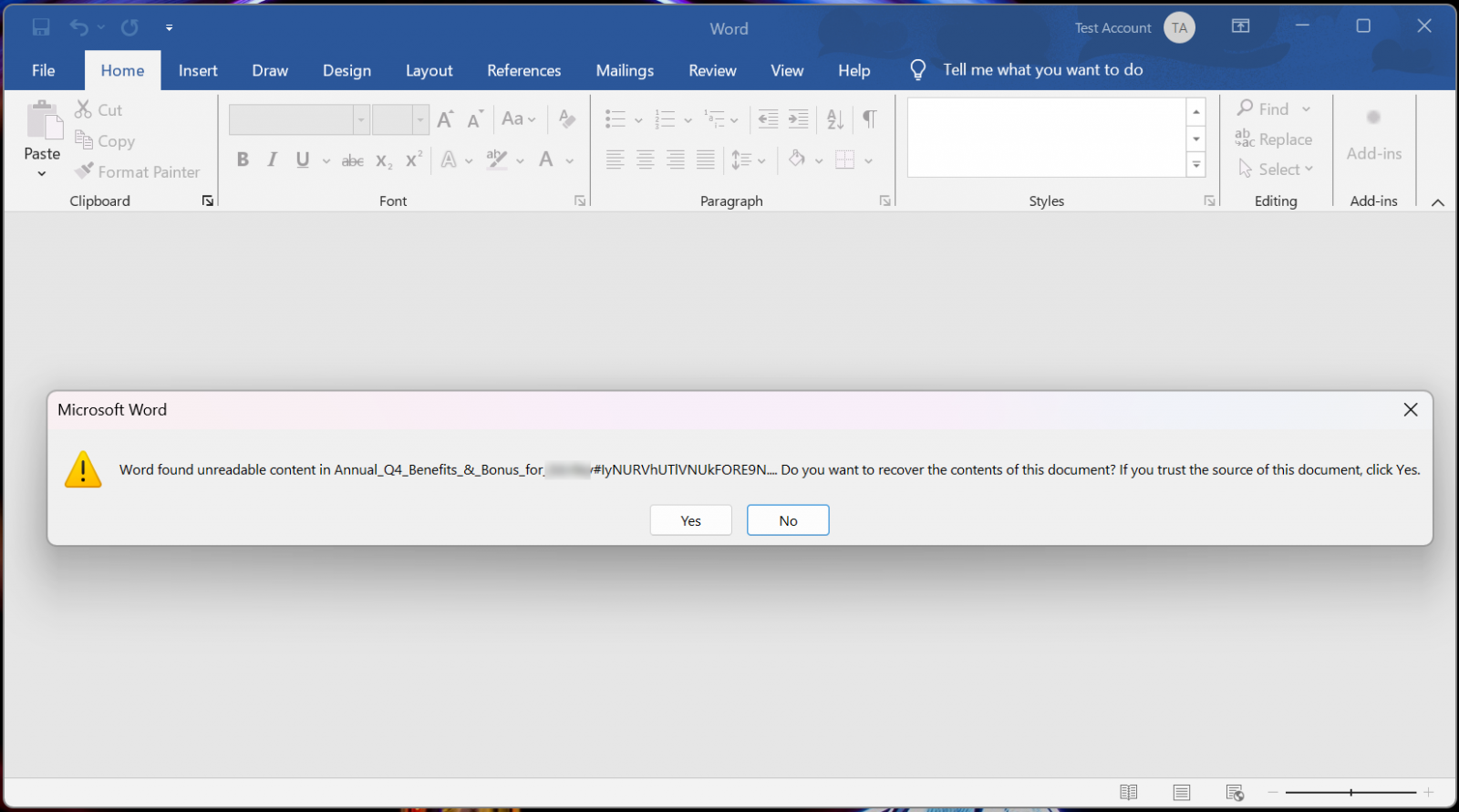
Source: BleepingComputer
These phishing documents are corrupted in such a way that they are easily recoverable, displaying a document that tells the target to scan a QR code to retrieve a document. As you can see below, these documents are branded with the logos of the targeted company, such as the campaign targeting Daily Mail shown below.
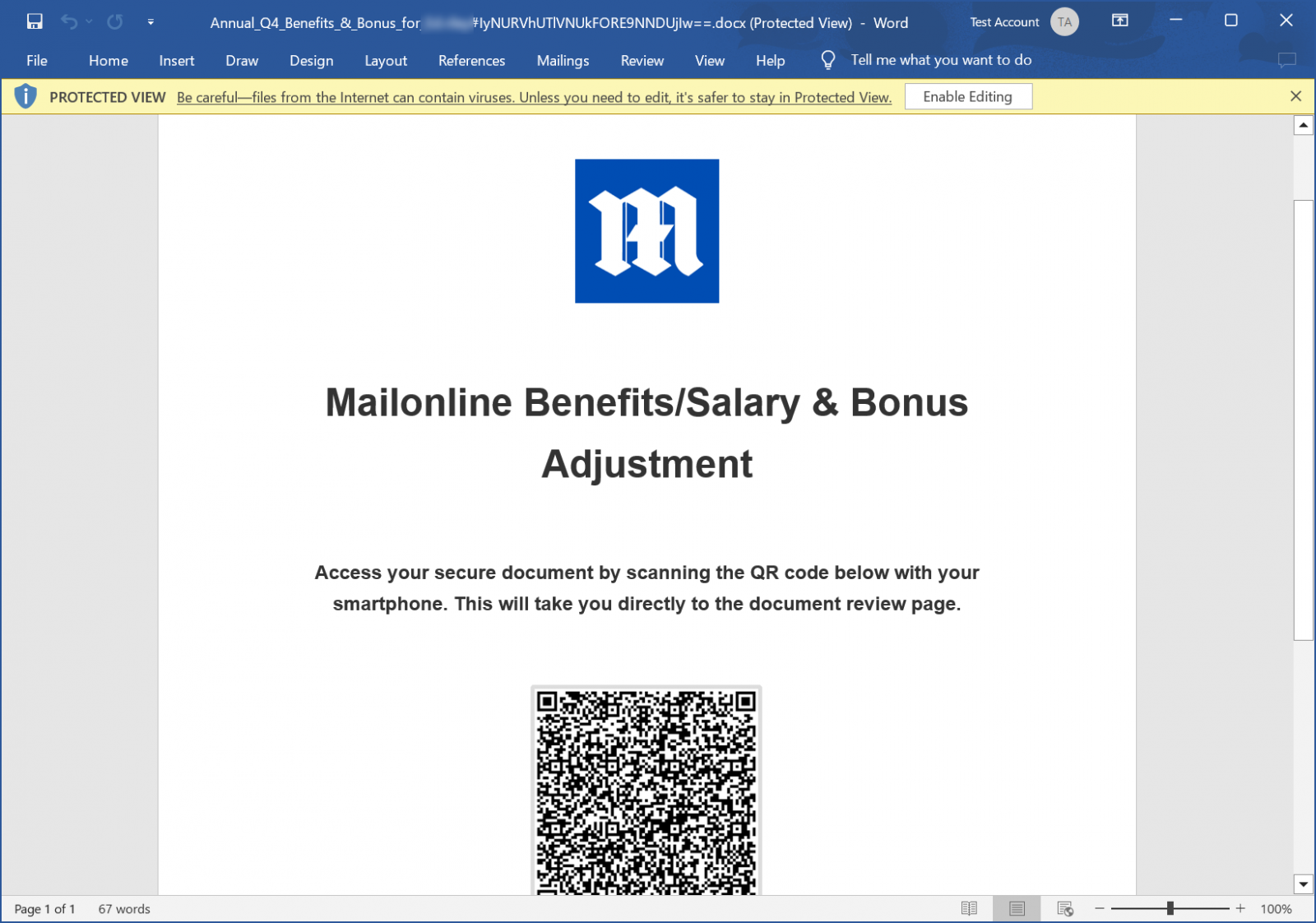
Source: BleepingComputer
Scanning the QR code will bring the user to a phishing site that pretends to be a Microsoft login, attempting to steal the user’s credentials.
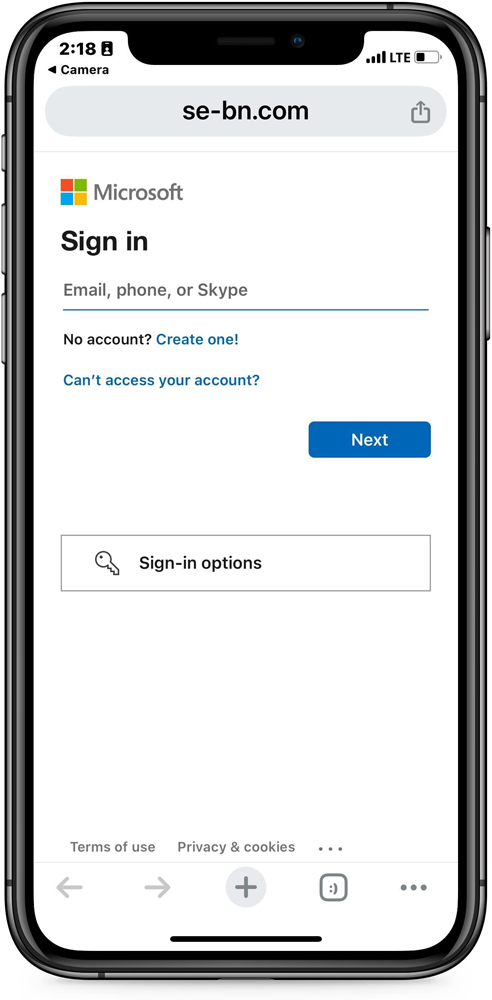
Source: BleepingComputer
While the ultimate goal of this phishing attack is nothing new, its use of corrupted Word documents is a novel tactic used to evade detection.
“Although these files operate successfully within the OS, they remain undetected by most security solutions due to the failure to apply proper procedures for their file types,” explains Any.Run.
“They were uploaded to VirusTotal, but all antivirus solutions returned “clean” or “Item Not Found” as they couldn’t analyze the file properly.”
These attachments have been fairly successful in achieving their goal.
From attachments shared with BleepingComputer and used in this campaign, almost all have zero detections [1, 2, 3, 4] on VirusTotal, with only some [1] detected by 2 vendors.
At the same time, this could also be caused by the fact that no malicious code has been added to the documents, and they simply display a QR code.
The general rules still apply to protect yourself against this phishing attack.
If you receive an email from an unknown sender, especially if it contains attachments, it should be deleted immediately or confirmed with a network admin before opening it.