### #SMOKEDHAM #UNC2465 #RansomwareEvolution
Summary: The SMOKEDHAM backdoor, utilized by the financially motivated threat actor UNC2465, has been a key player in extortion and ransomware operations since 2019. This analysis by TRAC Labs highlights the sophisticated techniques employed by UNC2465 to infiltrate and exploit target networks.
Threat Actor: UNC2465 | UNC2465
Victim: Various Organizations | Various Organizations
Key Point :
- SMOKEDHAM is delivered via trojanized software installers disguised as legitimate tools.
- The backdoor enables initial access for network reconnaissance and lateral movement, leading to ransomware deployment.
- UNC2465 has shifted focus from DARKSIDE to LOCKBIT ransomware, showcasing adaptability in their operations.
- Infection techniques include DLL side-loading, PowerShell obfuscation, and modifications to Windows services for persistence.
- Dynamic C2 URLs and encrypted communications enhance the stealth and resilience of SMOKEDHAM’s operations.
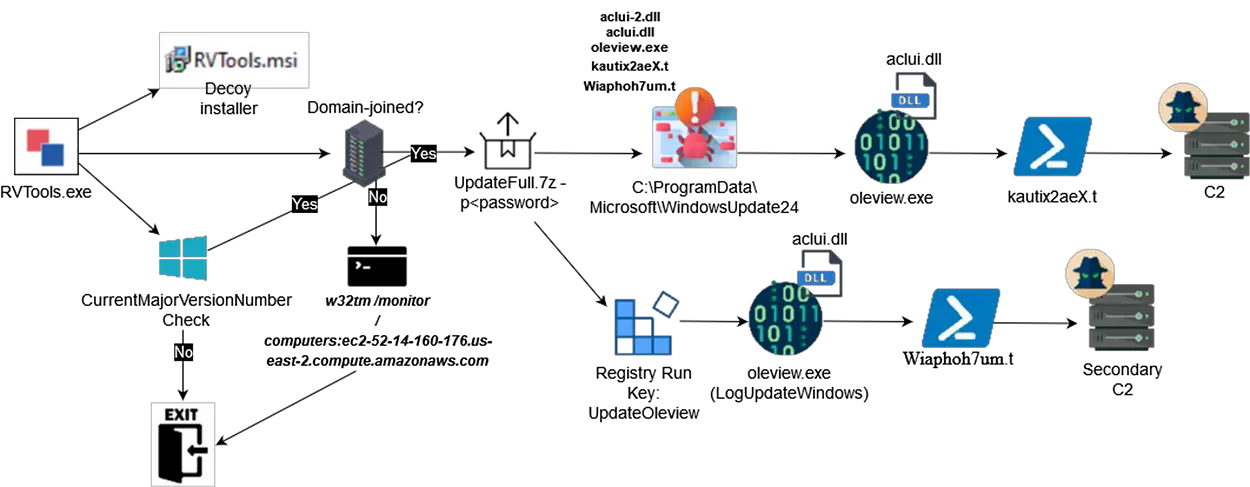
A comprehensive analysis by TRAC Labs has shed light on the SMOKEDHAM backdoor, a malicious tool leveraged by the financially motivated threat actor UNC2465. Active since 2019, SMOKEDHAM plays a central role in complex extortion and ransomware operations, marking UNC2465 as one of the most persistent and adaptive threat groups in the cybersecurity landscape.
SMOKEDHAM is a highly adaptable backdoor deployed via trojanized software installers, often spread through malvertising campaigns. According to TRAC Labs: “UNC2465 has leveraged trojanized installers disguised as legitimate tools, such as KeyStore Explorer and Angry IP Scanner, to deliver SMOKEDHAM payloads.”
Once embedded, SMOKEDHAM grants attackers initial access to a target’s system, paving the way for network reconnaissance, lateral movement, and, eventually, ransomware deployment. Historically linked to DARKSIDE ransomware, UNC2465 has since shifted its focus to LOCKBIT ransomware.
The infection process of SMOKEDHAM involves stealthy techniques, including DLL side-loading and PowerShell obfuscation. Key steps in the infection chain include:
- Trojanized Installers: Distributed through malicious advertising on platforms like Google Ads, these installers appear as legitimate software but contain the SMOKEDHAM payload.
- Service Manipulation: The backdoor alters the configuration of Windows services such as MSDTC to establish persistence and escalate privileges. “The purpose of running these commands is to later DLL side-load the binary named
oci.dllretrieved from the C2 server.” - Registry and Batch Script Modifications: Malicious scripts execute payloads, modify registry keys for persistence, and dynamically construct PowerShell commands for obfuscation.
UNC2465 uses a range of tools for post-compromise activities:
- Network Reconnaissance: Tools like Advanced IP Scanner and BloodHound identify valuable targets within a compromised network.
- Credential Harvesting: Mimikatz extracts sensitive credentials for further exploitation.
- Firewall Evasion: NGROK is used to expose internal services like RDP to the internet, bypassing network defenses.
TRAC Labs also noted: “Approximately 6 hours after the execution of the malicious binary on the beachhead host, the threat actors moved laterally to the Domain Controller using WMI.”
SMOKEDHAM’s communication with its command-and-control (C2) server is characterized by resilience and stealth:
- Dynamic C2 URLs: It uses domain fronting techniques, leveraging services like Cloudflare Workers to obscure traffic origins.
- Data Exfiltration and Commands: The malware sends reconnaissance data (e.g.,
whoami,systeminfo) and executes arbitrary PowerShell commands via encrypted communications. “The payload checks if the decrypted command contains “delay.” If it does, it configures the sleep interval between further C2 communications. If the response from the server contains “exit” — the payload process exits,” TRAC Labs explains.
The SMOKEDHAM backdoor exemplifies the evolving sophistication of cyber threat actors like UNC2465. With advanced techniques for stealth, persistence, and network infiltration, this malware remains a significant threat to organizations worldwide.