### #NTLMExploitation #PrivilegeEscalation #MicrosoftVulnerabilities
Summary: Recent findings reveal unpatched vulnerabilities in Microsoft’s NTLM protocol, allowing attackers to exploit NTLM leaks for privilege escalation. With Microsoft slow to respond, enterprises must take proactive measures to secure their systems.
Threat Actor: Unknown | unknown
Victim: Enterprises using Microsoft products | enterprises using Microsoft products
Key Point :
- NTLM protocol vulnerabilities allow for easy privilege escalation through credential leaks.
- Microsoft Word, Outlook, Access, Media Player, and Publisher have specific flaws that can be exploited without user action.
- Microsoft’s classification of these vulnerabilities as “Moderate” indicates a lack of urgency in addressing them.
- Recommendations for businesses include disabling NTLM authentication and blocking outbound SMB traffic.
- Immediate action is advised as waiting for a patch may not be a viable solution.
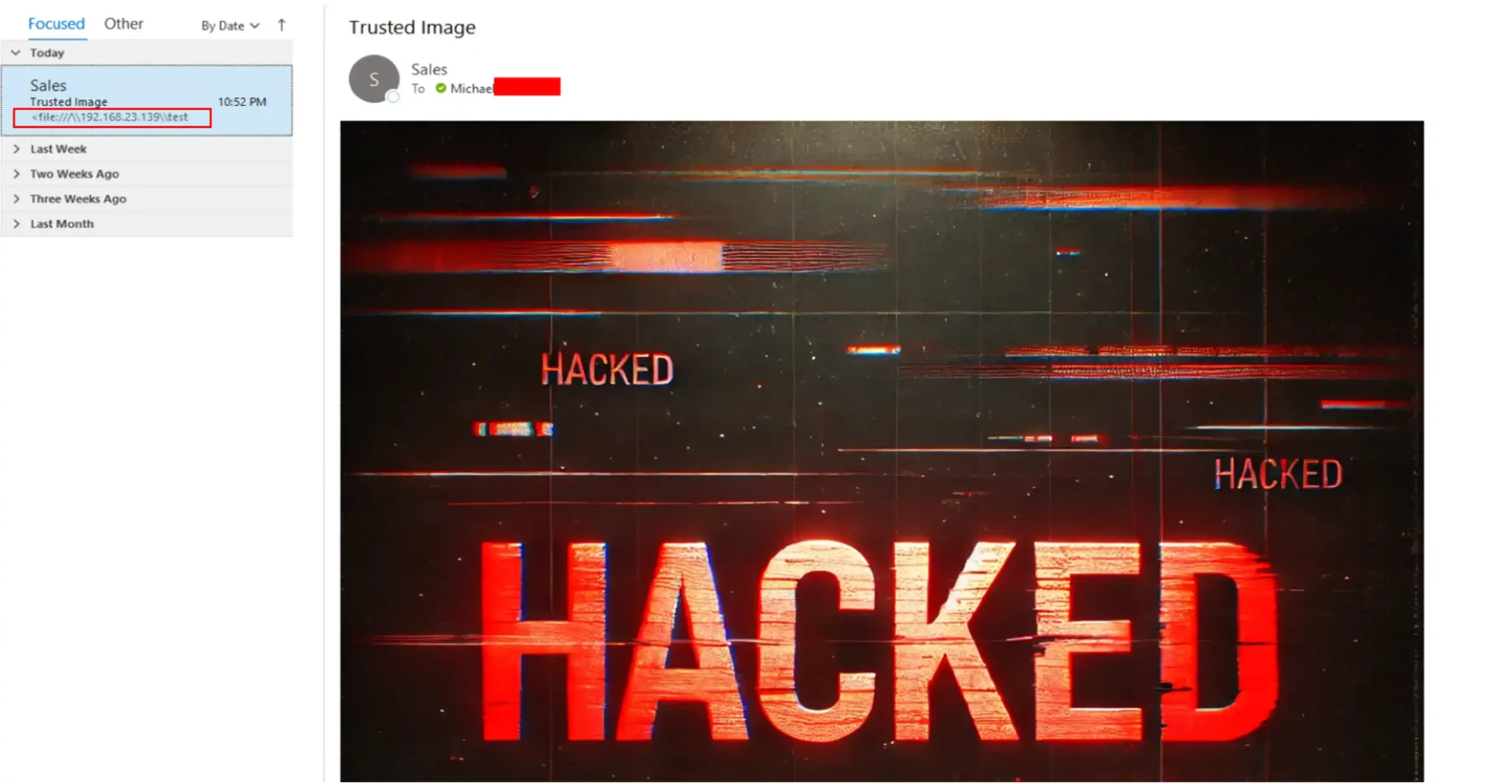
Microsoft’s NTLM protocol has once again become the focus of serious cybersecurity concerns, according to a recent report by Michael Gorelik at Morphisec. The report highlights several unpatched vulnerabilities in widely used Microsoft products, offering attackers easy pathways to privilege escalation through NTLM leaks. With Microsoft slow to address these issues, enterprises are left to fend for themselves.
Although NTLM is considered outdated, it remains a fallback for authentication in many environments. “The real issue lies in how file access requests can trigger NTLM fallback authentication, especially when connecting to a rogue SMB server,” Gorelik explains. This fallback exposes users to unintended credential leaks, often without any explicit user action.
Attackers can exploit leaked NTLM hashes for pass-the-hash attacks, enabling authentication without needing plaintext passwords. “If the NTLM hash belongs to a privileged user, attackers can perform DCSync attacks, request new Kerberos tickets, or escalate privileges within the domain,” the report notes.
The report outlines five key vulnerabilities across popular Microsoft products:
- Microsoft Word – RTF Auto Link Leak By embedding malicious OLE links in RTF files, attackers can trigger NTLM leaks. Even if users decline a prompt to enable external links, the flaw in Word’s “QueryHotLinks” function bypasses this rejection, sending NTLM hashes to the attacker’s server. Microsoft categorized this as “Moderate,” offering no immediate patch.
- Microsoft Outlook – Remote Image Tag Outlook automatically renders images from trusted senders, creating a loophole for attackers. “As soon as Outlook tries to fetch the image, it sends an NTLM authentication request to the attacker’s SMB server, leaking your NTLM hash,” Gorelik warns. The risk escalates with compromised trusted accounts.
- Microsoft Access – Remote Table Refresh Access databases can leak NTLM credentials via AutoExec macros that initiate remote table connections before users even enable active content. “This renders the initial warning messages ineffective,” the report explains.
- Windows Media Player – Legacy Playlist Files A double-click on a .wax or .wvx media file can trigger NTLM credential leaks as the player connects to an attacker-controlled SMB server. Shockingly, Microsoft deems this behavior “By Design” and has no plans for a fix.
- Microsoft Publisher – Remote Recipient List Publisher leaks NTLM hashes during the initial validation of remote recipient lists, even before users decide whether to access the data. The attacker doesn’t even need the file to exist; the verification attempt is sufficient to compromise credentials.
Microsoft’s response to these vulnerabilities has been underwhelming. In many cases, the company classified the risks as “Moderate” or described the vulnerabilities as features rather than flaws. Gorelik observes, “Even with the latest developments in Windows 11… Microsoft is more focused on sidestepping the issue rather than fixing it outright.”
With no immediate fixes from Microsoft, businesses must take the lead in securing their environments. Key recommendations include:
- Disabling NTLM Authentication: Use Group Policy to restrict NTLM usage and enforce Kerberos-only authentication.
- Blocking Outbound SMB Traffic: Prevent connections to untrusted networks to mitigate NTLM leaks.
- Educating End Users: Train employees to recognize and avoid potential exploitation vectors.
Gorelik concludes, “Waiting for a patch is not advisable. Businesses should take immediate steps to mitigate exposure rather than relying on a fix that may never come.”
Related Posts:
Source: https://securityonline.info/unpatched-ntlm-flaws-leave-microsoft-systems-vulnerable