### #MallocStackLoggingExploit #LocalPrivilegeEscalation #AppleVulnerability
Summary: A critical vulnerability in Apple’s MallocStackLogging framework allows attackers to achieve local privilege escalation on macOS systems, posing a significant security risk. Despite Apple’s mitigations, the flaw can be exploited through clever manipulation of log file writes.
Threat Actor: Unknown | Unknown
Victim: Apple | Apple
Key Point :
- The vulnerability, designated CVE-2023-32428, has a CVSS score of 7.8, indicating high severity.
- Attackers can exploit the MallocStackLogging framework to gain root privileges without needing a password.
- Apple’s mitigations, such as randomizing log filenames and using secure flags, have significant flaws that can be bypassed.
- Gergely Kalman demonstrated the exploit by creating a file in /etc/sudoers.d to grant root access.
- The vulnerability affects macOS Ventura 13.3 and earlier, with patches available in macOS Ventura 13.4 and other platforms.
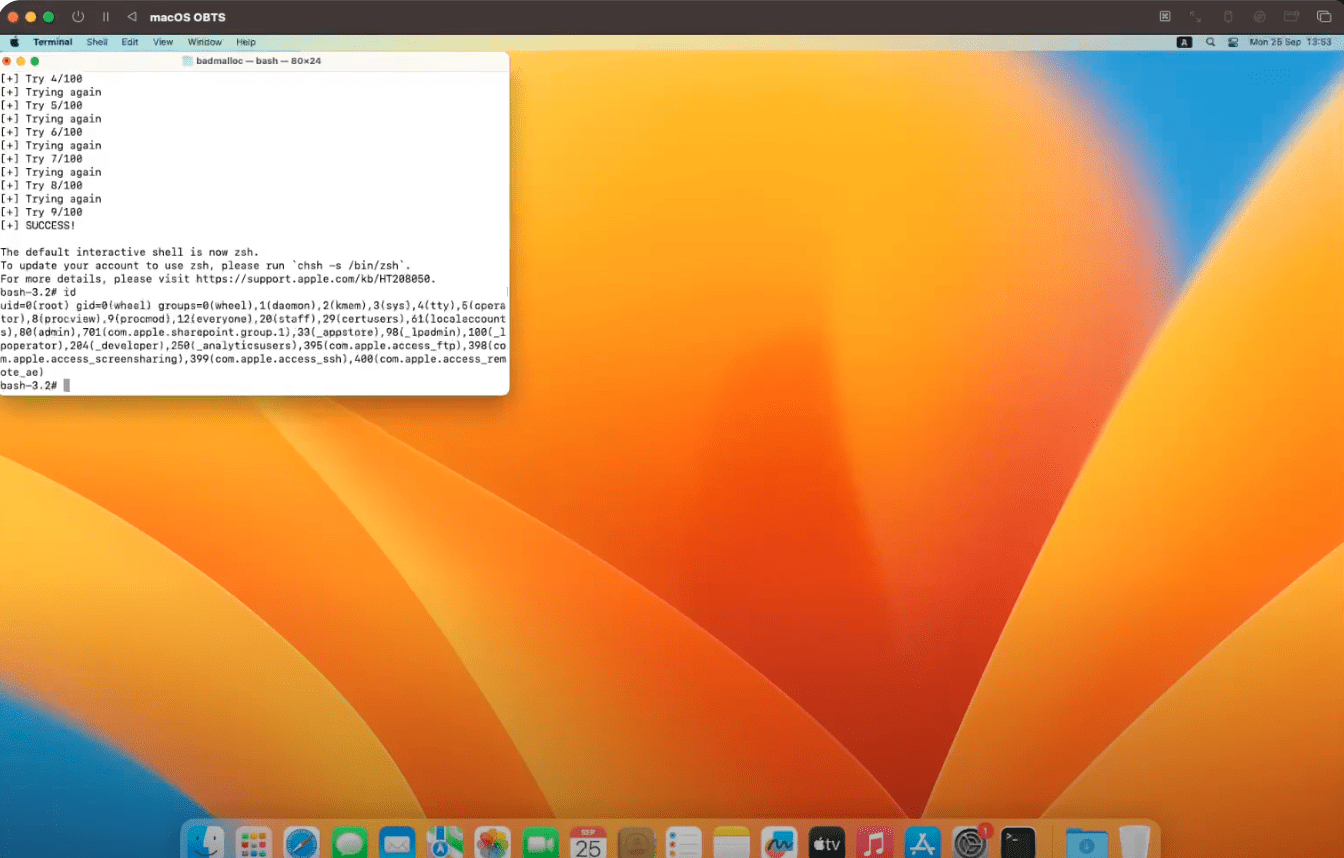
Security researcher Gergely Kalman has detailed a high-severity vulnerability in Apple’s MallocStackLogging framework that could allow attackers to gain local privilege escalation (LPE) on macOS systems. The flaw, designated CVE-2023-32428 with a CVSS score of 7.8, demonstrates how seemingly helpful developer tools can be manipulated to bypass security measures and compromise high-privilege operations.
MallocStackLogging is a debugging framework in macOS, used for monitoring memory allocations. The vulnerability exploits the framework’s ability to dynamically load into processes without requiring special permissions. “The MallocStackLogging.framework will be loaded by the dynamic loader (dyld) into any process whenever a MallocStack* environment variable is detected,” Kalman explained. This functionality works even with suid-root binaries, making it a ripe target for attackers.
The key danger lies in how the framework writes log files: “The target process has no idea that this is happening,” Kalman noted, emphasizing that these files are created with the privileges of the running process.
Apple implemented several mitigations to limit exploitation, including:
- Using
open()with secure flags to prevent overwriting files and following symlinks. - Randomizing log filenames to thwart prediction attempts.
- Restricting file permissions to enhance security.
However, Kalman highlighted significant flaws in these mitigations. For example, “access() is useless for securing filesystem operations” because files can be swapped after permission checks but before they are opened. Additionally, the O_NOFOLLOW flag in open() only prevents symlinks in the last path component, leaving other parts of the path vulnerable to manipulation.
Kalman developed an exploit that uses a race condition to redirect log file writes to arbitrary locations accessible by the process. By combining this with a well-timed symlink replacement, attackers can manipulate privileged binaries such as crontab.
For instance, the exploit creates a file in /etc/sudoers.d to grant root access without requiring a password. Kalman demonstrated this method in a proof-of-concept, gaining root privileges by exploiting the vulnerability.
The vulnerability impacts macOS Ventura 13.3 and earlier versions. Apple has patched the issue in macOS Ventura 13.4 and other platforms like iOS and tvOS 16.5. Users are strongly encouraged to update their devices to avoid potential exploitation.
Kalman expressed mixed feelings about the discovery, noting, “For all of this work, I received $22,500, which was pretty disappointing, since my TCC bypasses were worth more.”
Related Posts:
Source: https://securityonline.info/macos-vulnerability-cve-2023-32428-grants-root-access-poc-published