Summary: Security researchers from Hunt.io have identified a cyber operation utilizing the Sliver command-and-control framework and Ligolo-ng tunneling tool, targeting victims by impersonating Y Combinator. The operation highlights the evolving tactics of cybercriminals leveraging trusted brands to establish credibility and evade detection.
Threat Actor: Cybercriminals | cybercriminals
Victim: Y Combinator | Y Combinator
Key Point :
- The attackers registered a domain mimicking Y Combinator to deflect suspicion and establish a facade of authenticity.
- A malicious ELF file was identified, serving as a Sliver implant for stealthy communication with the attackers’ infrastructure.
- Ligolo-ng was used to facilitate internal network exploration, enhancing the attackers’ lateral movement capabilities.
- Frequent cycling of TLS certificates associated with the Sliver C2 indicates attempts to mislead security researchers.
Security researchers from Threat Hunting Platform Hunt.io have uncovered a recent operation leveraging the Sliver command-and-control (C2) framework and Ligolo-ng tunneling tool. The operation aimed at targeting victims using the trusted name of Y Combinator, a renowned startup accelerator.
Originally developed by Bishop Fox for adversary emulation and red teaming, Sliver has found a new audience among cybercriminals and nation-state actors. Hunt.io’s report describes Sliver as a cross-platform command-and-control (C2) framework with robust functionality, including support for encrypted communications over channels like mTLS, WireGuard, HTTP(S), and DNS. Its compatibility with Windows, macOS, and Linux has made it an attractive option for threat actors seeking to evade detection while conducting operations.
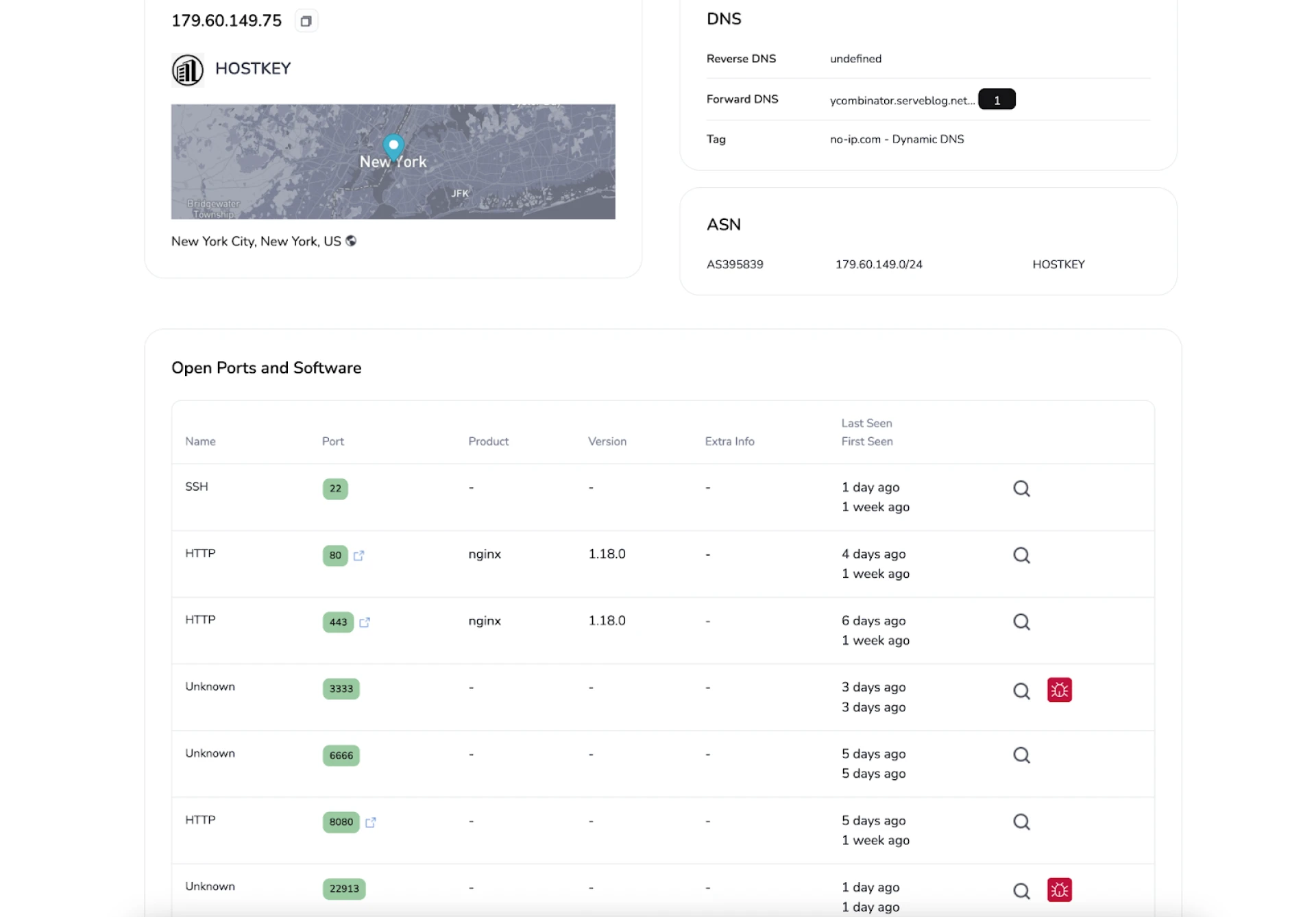
The attackers registered a domain, ycombinator.serveblog[.]net, to resemble Y Combinator’s official website. According to Hunt.io, this spoofed domain redirects users to Y Combinator’s legitimate site, possibly as a means of deflecting suspicion while establishing a facade of authenticity. “The similarity to the legitimate brand name suggests a potential attempt to establish trust or credibility,” the report states.
Further investigation revealed the presence of a malicious ELF file, identified on VirusTotal, which communicated with an IP linked to Sliver C2 on ports associated with both Sliver and Ligolo-ng. This file, named “cloud” and flagged by multiple antivirus vendors, appears to serve as a Sliver implant designed for stealthy network communication with the attackers’ infrastructure.
Ligolo-ng, a tool popular with penetration testers, was also deployed in this campaign to support stealthy internal network exploration. As Hunt.io noted, Ligolo-ng “allows security professionals to securely access internal networks via a reverse TCP/TLS connection.” This tool’s capabilities align well with Sliver’s features, enhancing the attackers’ ability to move laterally within targeted environments.
Through proactive analysis, Hunt.io discovered that the primary IP associated with Sliver C2 frequently cycled through TLS certificates, including one tied to the spoofed Y Combinator domain. Some certificates used “localhost” as a common name, potentially as a tactic to mislead researchers by mimicking local testing certificates. Hunt.io researchers stated, “These findings emphasize the importance of monitoring subtle changes in known malicious infrastructure indicators,” as this can help identify additional servers linked to ongoing campaigns.