Summary: Security researcher Ron Masas from Imperva Threat Research has revealed a new method for attackers to exploit Chrome users via the File System Access API, which can bypass security mechanisms on both Windows and macOS. This exploit can lead to severe security vulnerabilities, particularly for macOS users, if they inadvertently grant file access to malicious applications.
Threat Actor: Unknown | unknown
Victim: Chrome users | Chrome users
Key Point :
- Attackers can exploit the File System Access API to read and write local files without 0-day vulnerabilities.
- Chrome’s blocklist for sensitive files has loopholes that can be exploited using symbolic links.
- Proof-of-concept applications demonstrate how users can be tricked into granting file access, leading to arbitrary code execution.
- Recommendations include removing execute permissions from files modified by the File System Access API to enhance security.
- Users are advised to be cautious and think twice before allowing file access to prevent potential security breaches.
Security researcher Ron Masas from Imperva Threat Research has uncovered a new way attackers can target Chrome users without relying on 0-day vulnerabilities. This approach leverages the File System Access API, which allows websites to read and write to local files when users grant permission. According to Masas, “This API bypasses both Windows and macOS security mechanisms,” raising serious concerns, especially for macOS users, who rely on the operating system’s Gatekeeper feature to prevent unauthorized code execution.
Masas’ interest in this exploit type began years ago with the Java applet “drive-by download” technique, which allowed web pages to execute arbitrary code. In the modern version of this attack, “a single misclick could lead to a compromised system,” especially when Chrome’s File System Access API is involved.
Masas identified that Chrome has a blocklist to restrict access to sensitive files, but it has loopholes. By leveraging symbolic links (symlinks), attackers can trick Chrome into writing to files that are otherwise protected. “The Google Chrome Helper acts,” Masas notes, “as an intermediary between Chrome and any installed plugins,” providing attackers with a direct route to execute code when overwritten.
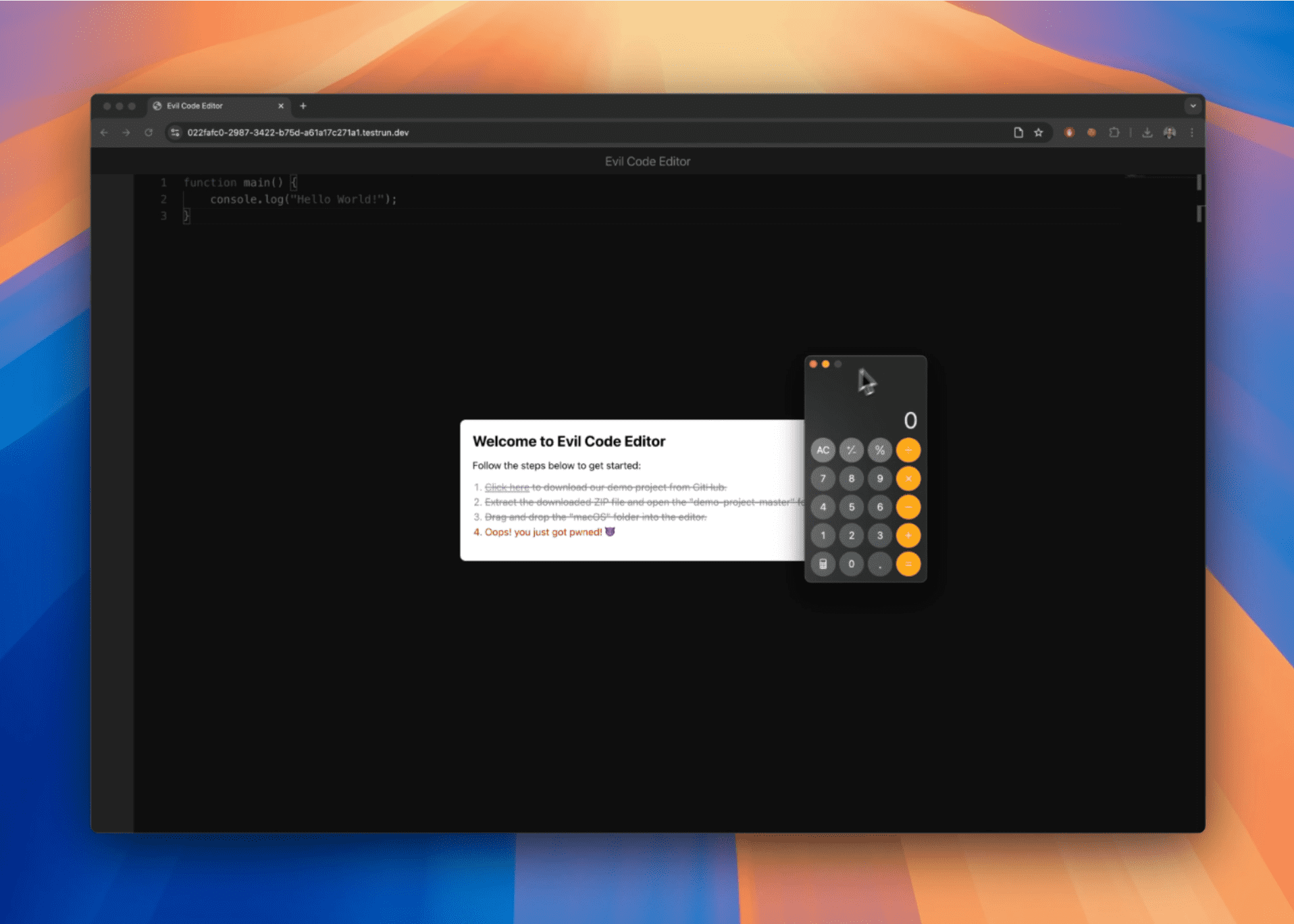
To showcase the potential impact, Masas developed two proof-of-concept applications: a browser AI helper and a fake online IDE called “Evil Code Editor.” Both PoCs were designed to lure users into granting file access, which could then be used to execute arbitrary commands. Masas explains, “If users follow these steps, attackers could execute arbitrary commands on their machines,” highlighting the severity of this exploit.
The report recommends that Google remove execute permissions from files modified by the File System Access API to mitigate these attacks. While Google plans to implement restrictions in Chrome 132, this issue remains unpatched at present.
As Masas concludes, “Even today, a few wrong clicks can open the door to serious security issues. Stay alert and think twice before allowing access to your files.” This reminder underscores the risks of modern web functionality, where convenience and security are constantly at odds.
Related Posts:
Source: https://securityonline.info/javascript-drive-by-attacks-new-exploits-without-0-day-in-google-chrome